Method and apparatus for third party to control device
A technology for controlling equipment and intelligent equipment, applied in the direction of program control, computer control, comprehensive factory control, etc., can solve problems such as inconvenient operation, and achieve the effect of improving safety and usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
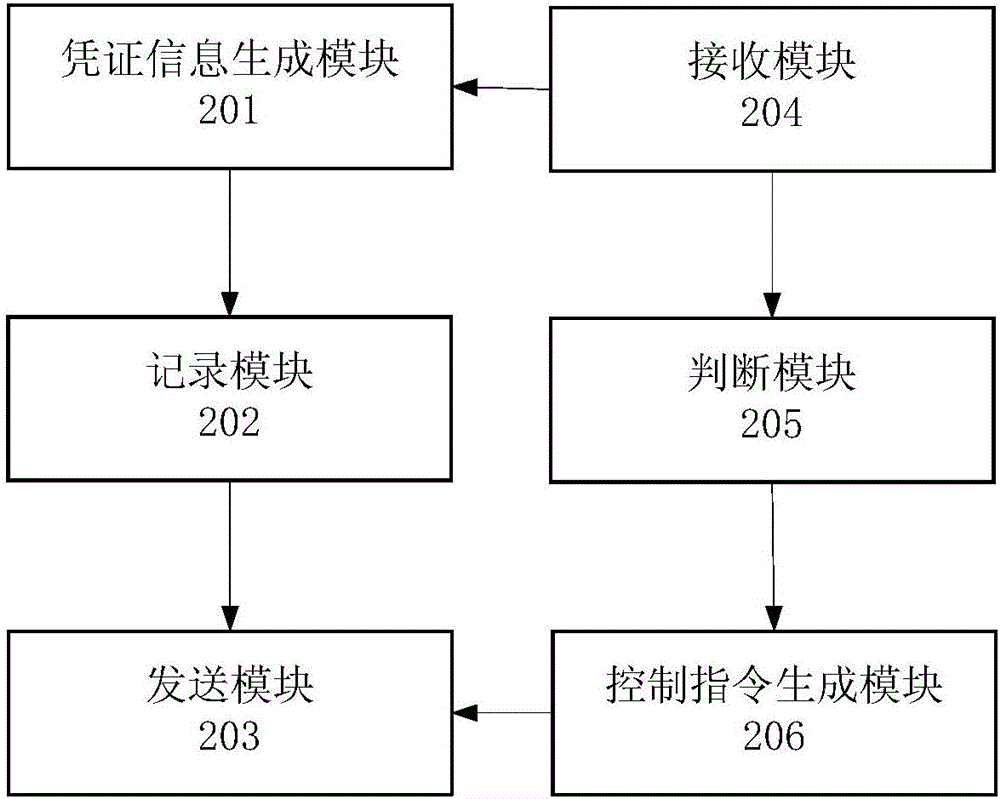
Image
Examples
Embodiment 1
[0066] The authorized user on the first terminal is an authorized user of the first smart device, and has control authority for at least one control content of the first smart device. The access user on the second terminal is not an authorized user of the first smart device, but needs to control the first smart device. For example, when the smart device is an access control system, the authorized user has control authority over the door opening control of the access control system, or at the same time also has control authority over the door closing control of the access control system. When the smart device is not an access control device, the authorized user has the control authority for multiple control contents of the smart device.
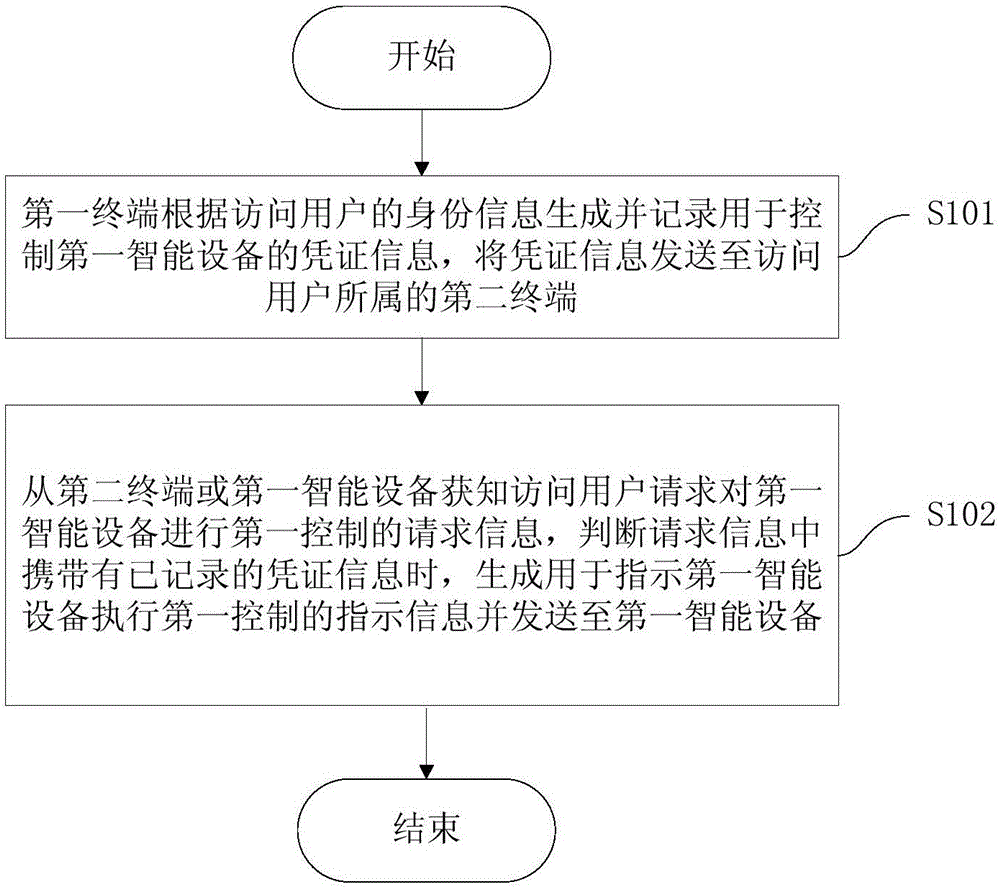
[0067] figure 1 It is a flowchart of a method for a third-party control device in an embodiment; the method for a third-party control device includes:
[0068] Step 101, the first terminal generates and records credential information for con...
Embodiment 2
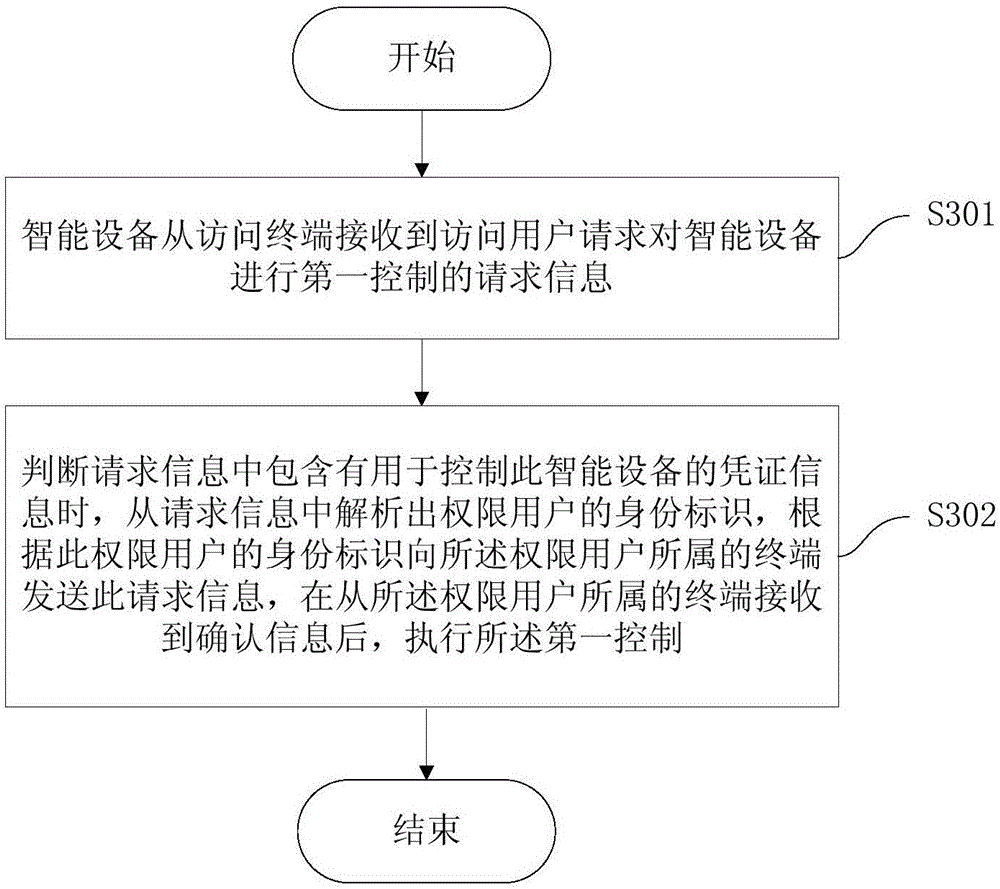
[0094] image 3 It is the third-party control device method in the second embodiment, the execution subject of this method is a smart device, and this method includes:
[0095] Step 301, the smart device receives request information from the access terminal for the first control of the smart device by the access user;
[0096] Step 302, when it is judged that the request information contains credential information for controlling the smart device, parse out the identity of the authorized user from the request information, and send the request information to the terminal to which the authorized user belongs according to the identity of the authorized user and performing the first control after receiving confirmation information from the terminal to which the authorized user belongs.
[0097] The method further includes: after parsing out the identity of the authorized user, when judging according to the identity of the authorized user that the authorized user has the authority...
specific Embodiment 1
[0107] Such as Figure 5 As shown, the terminal belonging to user A who has the control authority to the access control system is the first terminal, and the terminal to which user B has no control authority to the access control system is the second terminal.
[0108] The first terminal sends a request for acquiring user information to the second terminal. A specific implementation may be that the first terminal dynamically generates an application (APP) in webpage format, and pushes its uniform resource locator (URL) to the second terminal in the form of real-time communication (IM). User B clicks on the URL to activate the application in webpage format. This application can obtain user B's user information (user ID and device ID, etc.), and the APP can establish a session with the application of the first terminal, and send user B's user information through this session information. This APP is also the window for user B to send subsequent messages.
[0109] The first te...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com