SQL injection attack defensive system and method based on dynamic conversion
A dynamic transformation and injection attack technology, applied in the field of network security, can solve problems such as difficulty in establishing normal SQL statements and SQL injection attacks, large and diverse data volume, and inability to defend against SQL injection attacks from the root cause
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
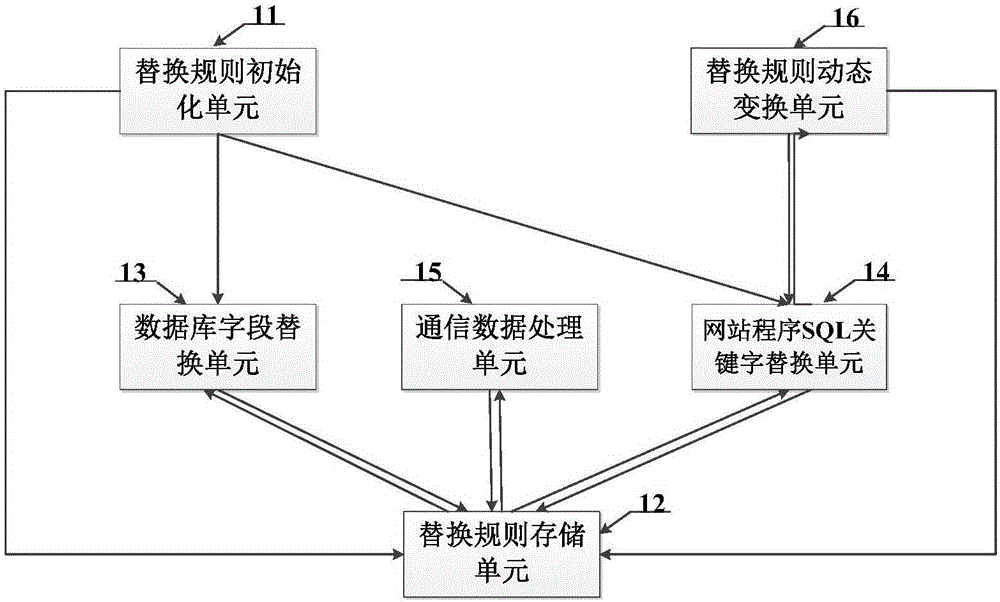
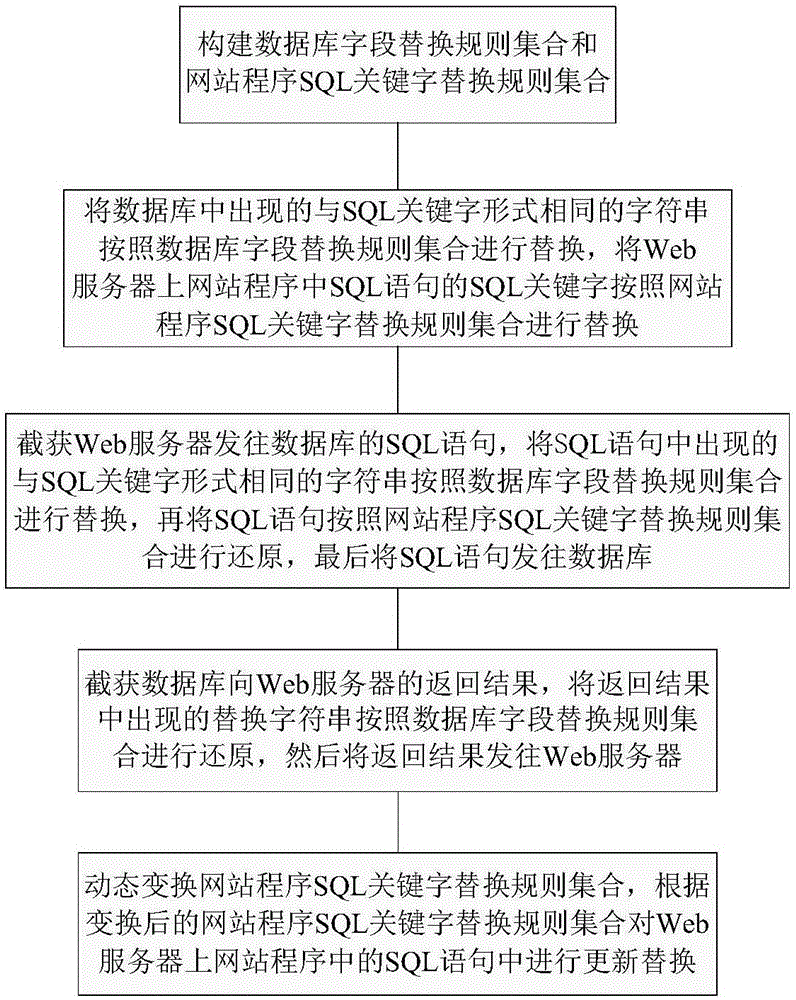
Image
Examples
Embodiment 1
[0083] Embodiment 1 is an example of a normal user operating the database. Assume that the SQL query statement for login verification in a website program is select*from users where name='username entered by the user' and pw='password entered by the user'; the correct user name is admin, and the correct password is password, Username admin and password password are stored in the database. The SQL keyword set A configured by the user is {..., select, where, and,...}. The database field replacement rule set B constructed according to set A is {..., select→string a, where→string b, and→string c,...} The string is briefly described); the website program SQL keyword replacement rule set C constructed according to the set A is {..., select→string h, where→string i, and→string j,...} (this For the convenience of description, the replacement character strings are also briefly described, and the character strings h, i, and j are different from the character strings a, b, and c). Fir...
Embodiment 2
[0085] The second example of a normal user operating the database is given below. Assume that the SQL query statement for login verification in a website program is select*from users where name='user name entered by the user' and pw='password entered by the user'; the correct user name is select, and the correct password is password, The username select and the password password are stored in the database. The SQL keyword set A configured by the user is {..., select, where, and,...}. The database field replacement rule set B constructed according to set A is {..., select→string a, where→string b, and→string c,...} The string is briefly described); the website program SQL keyword replacement rule set C constructed according to the set A is {..., select→string h, where→string i, and→string j,...} (this For the convenience of description, the replacement character strings are also briefly described, and the character strings h, i, and j are different from the character strings ...
Embodiment 3
[0087] An example of SQL injection attack is given below.
[0088] Assume that the SQL query statement for login verification in a website program is select*from users where name='username entered by the user' and pw='password entered by the user'; the correct user name is admin, and the correct password is password, Username admin and password password are stored in the database. If the user name of the assailant's input is 1'or'1'='1, and the password of the input is 1'or'1'='1, without arranging the defense system of the present invention, the SQL statement sent to the database will be Become select*from users where name='1'or'1'='1'and pw='1'or'1'='1', which is equivalent to select*from users, the attacker passes such Injection can realize the login to the website without account and password, and achieve its attack purpose. But after deploying the defense system of the present invention, according to the scheme of the defense system of the present invention, first const...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com