A Hardware Implementation Method and Circuit of Additive Mask Against Energy Analysis Attack
An energy analysis attack and additive masking technology, which is applied in the field of information security chip design, can solve the problems of large ROM consumption and high cost, and achieve the effects of avoiding information leakage, simple structure, and easy execution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to better illustrate the present invention, the present invention will be described in detail with preferred embodiments and accompanying drawings, specifically as follows:
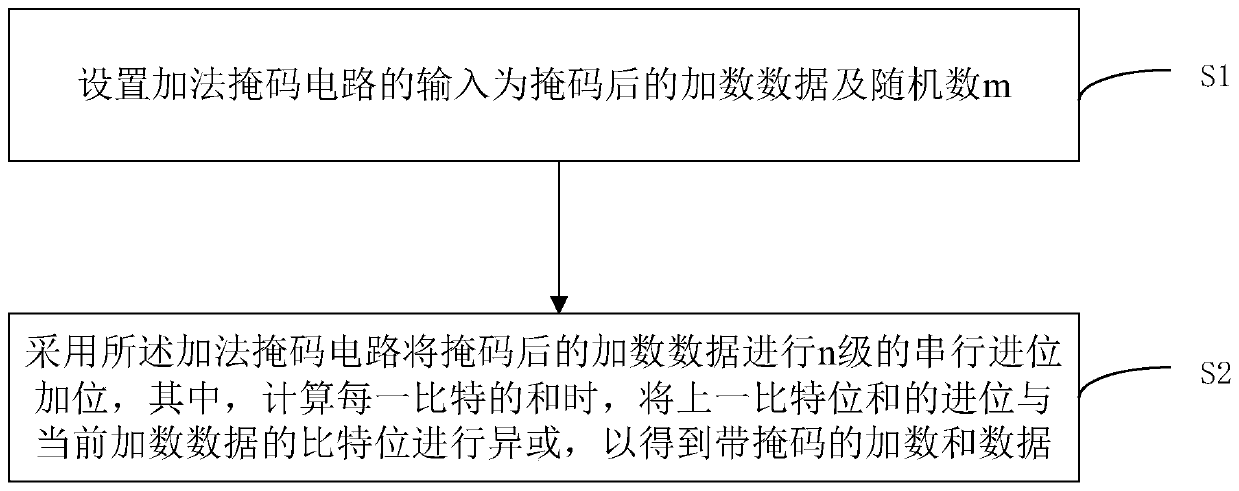
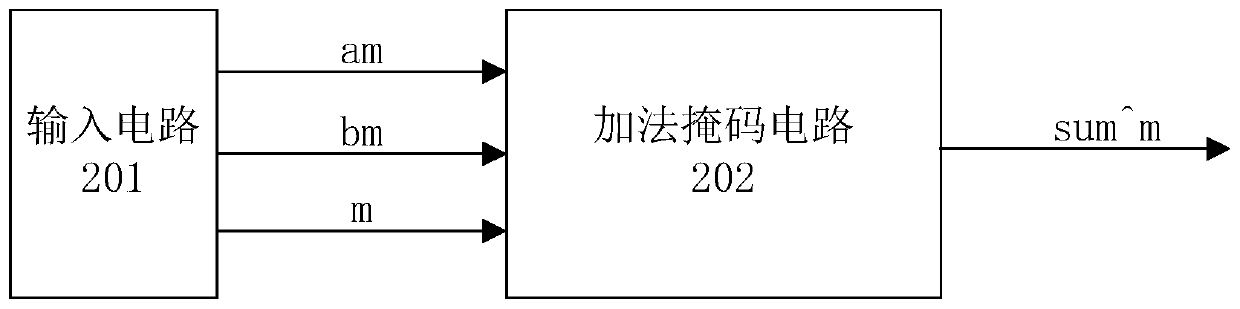
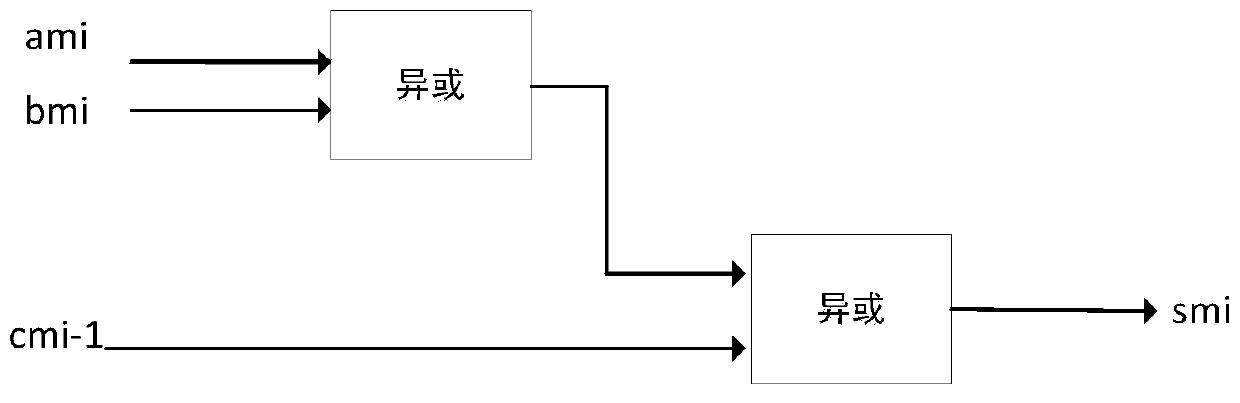
[0030] This embodiment provides a hardware implementation circuit of an additive mask against energy analysis attacks. The circuit is used for calculating the sum of addends with a mask, and obtaining the sum with a mask, so that no mask removal operation will occur in the process of calculating the addend. Specifically, the finite field GF(2 n ) in which the two addends are a and b respectively, and m is GF(2 n ) field of random numbers. The sum of the two numbers a and b is recorded as sum, that is, the following formula is established:
[0031] sum=a+b (1)
[0032] Among them, a, b, sum are GF(2 n ), "+" is defined as the addition modulo n operation.
[0033] Then a, b mask method is as follows
[0034] a^m=am (2)
[0035] b^m=bm (3)
[0036] Among them, "^" is defined as a bit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com