Ad hoc network opportunistic routing method avoiding malicious attacks
A malicious attack and routing technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of inconsistent information verification, information difference between statistical information and routing information table, misjudgment, etc., to ensure information Security, the effect of improving data transmission capability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] Embodiments of the present invention will be described below in conjunction with the accompanying drawings.
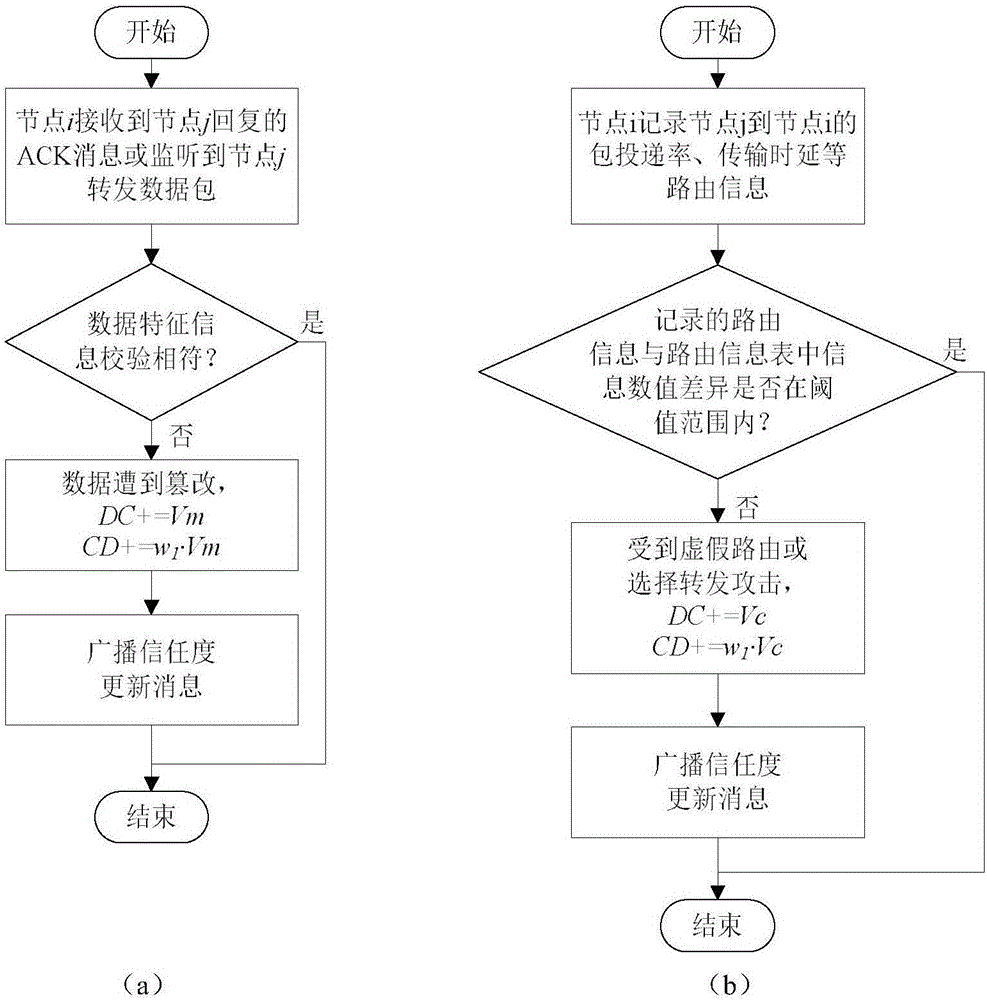
[0051] The present invention designs an Ad hoc network opportunistic routing method for avoiding malicious attacks. Firstly, the prior information on the operation of the opportunistic routing protocol is obtained by updating the routing information, and then the data transmission process is performed on the premise of obtaining the routing information, and the candidate forwarding node is selected. Mechanisms and forwarding nodes establish mechanisms to transmit packets along opportunistic paths from source nodes to destination nodes. In addition, the protocol identifies malicious nodes in the network through the malicious behavior identification mechanism and node trust mechanism and removes the malicious nodes from the Ad hoc network. The removed malicious nodes will not be able to participate in the data transmission process.
[0052] Step (1), the routing i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com