Botnet detection method based on Netflow and DNS blog
A botnet, DNS query technology, applied in electrical components, transmission systems, etc., can solve the problems of unable to find the control domain name of the FFSN network, high misjudgment rate, unable to accurately locate the FFSN dynamic malicious domain name, etc., to improve the positioning accuracy and Effectiveness, the effect of reducing the false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
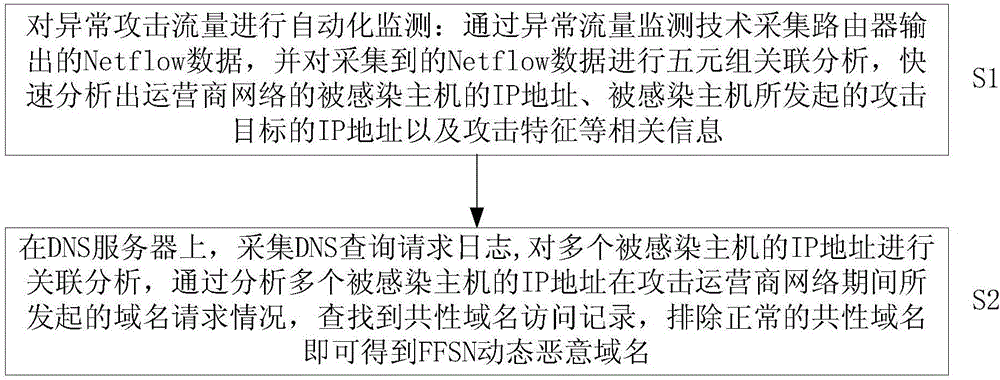
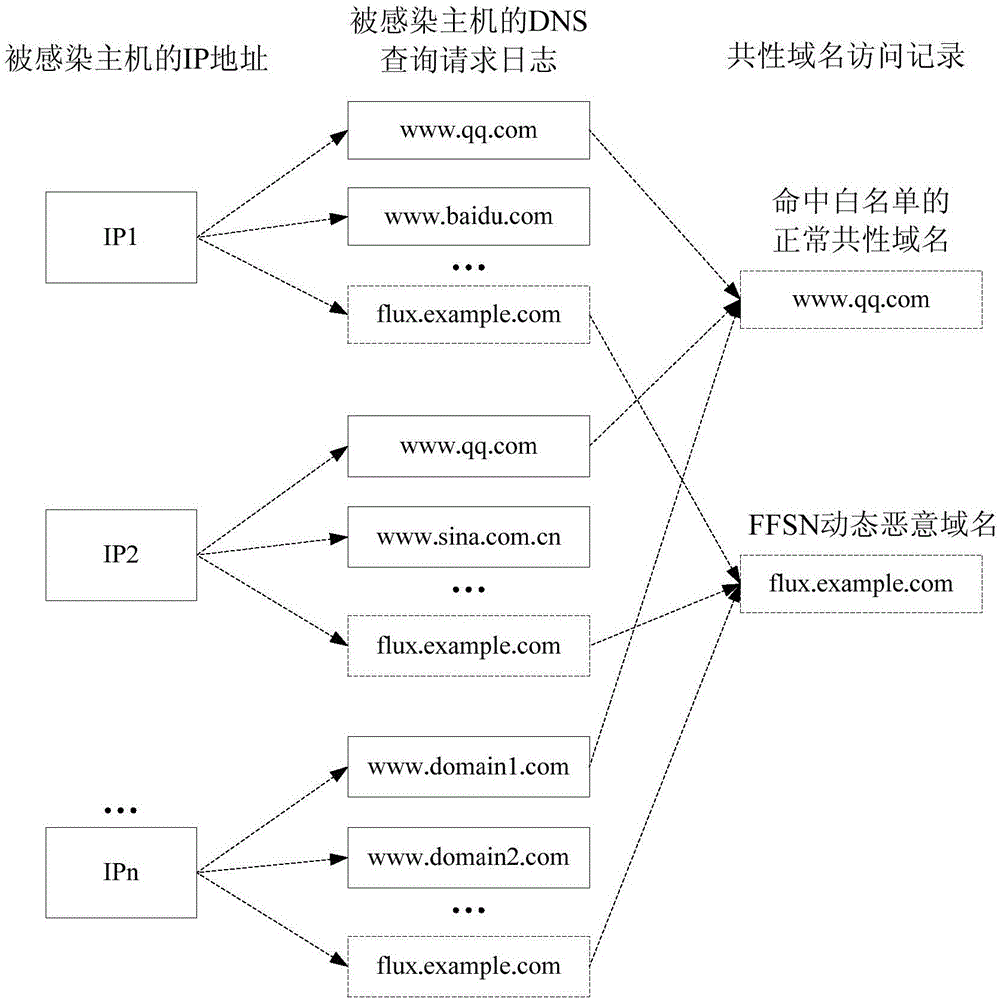
[0020] Existing botnet detection methods usually use a certain dimension of detection technology, the recognition accuracy of FFSN dynamic malicious domain names is low, and the positioning effect is not good, and the present invention is aimed at a large number of DDoS generated by FFSN networks such as Botnet and Fast-Flux Attack, providing a botnet detection method based on Netflow and DNS logs, using multi-dimensional (including source IP address, source port, destination IP address, destination port and protocol type) fusion detection technology, which can automatically detect FFSN dynamic malicious The domain name greatly improves the positioning accuracy and effectiveness of FFSN dynamic malicious domain names, and restrains the spread of FFSN network from the source, reduces the bandwidth congestion, denial of service duration and occurrence probability of basic network facilities of operators and users, and guarantees It improves the security of Internet basic network ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com