Encryption/decryption function generating method, an encryption/decryption method and related apparatuses
A function generation and function technology, applied in the information field, can solve problems such as imperfect design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
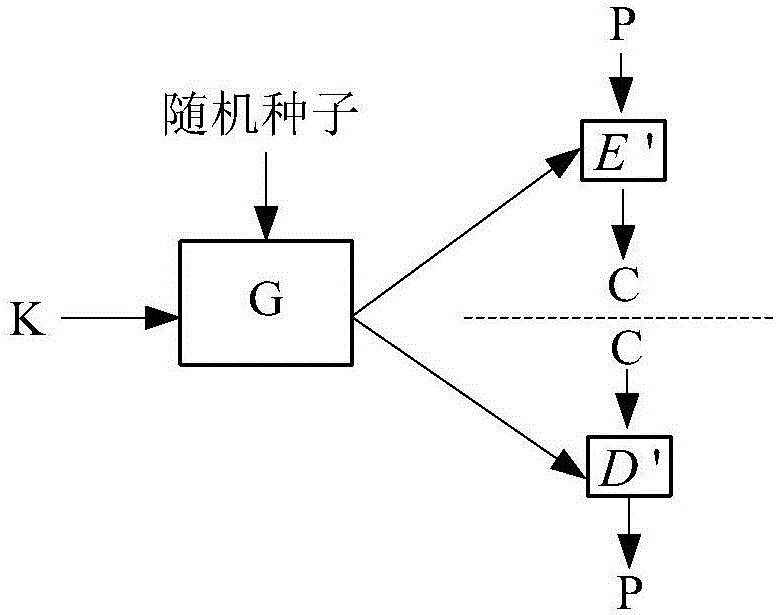
[0175] An embodiment of the present invention provides a method for generating an encryption function. Specifically, as Figure 8 As shown in , the method includes the following steps:
[0176] 801. The encryption function generator obtains the random seed and the original key.
[0177] Specifically, in the encryption function generation method provided in the embodiment of the present invention, the encryption function generation device first needs to obtain a random seed and an original key.
[0178] A random seed is a fixed-length bit string and can be used to generate random numbers by using a random number generator. A random number generator can be thought of as a function g(x) where the input is a fixed-length random seed such as a k-bit string and the output is a sequence of random numbers having a length of any number of bits and used as a source of random numbers for subsequent use; and A key is a set of information codes and the key participates in and exerts ce...
Embodiment 2
[0260] An embodiment of the present invention provides an encryption method. Specifically, as Figure 10 As shown in , the method includes the following steps:
[0261] 1001. The encryption device receives the plaintext input by the user.
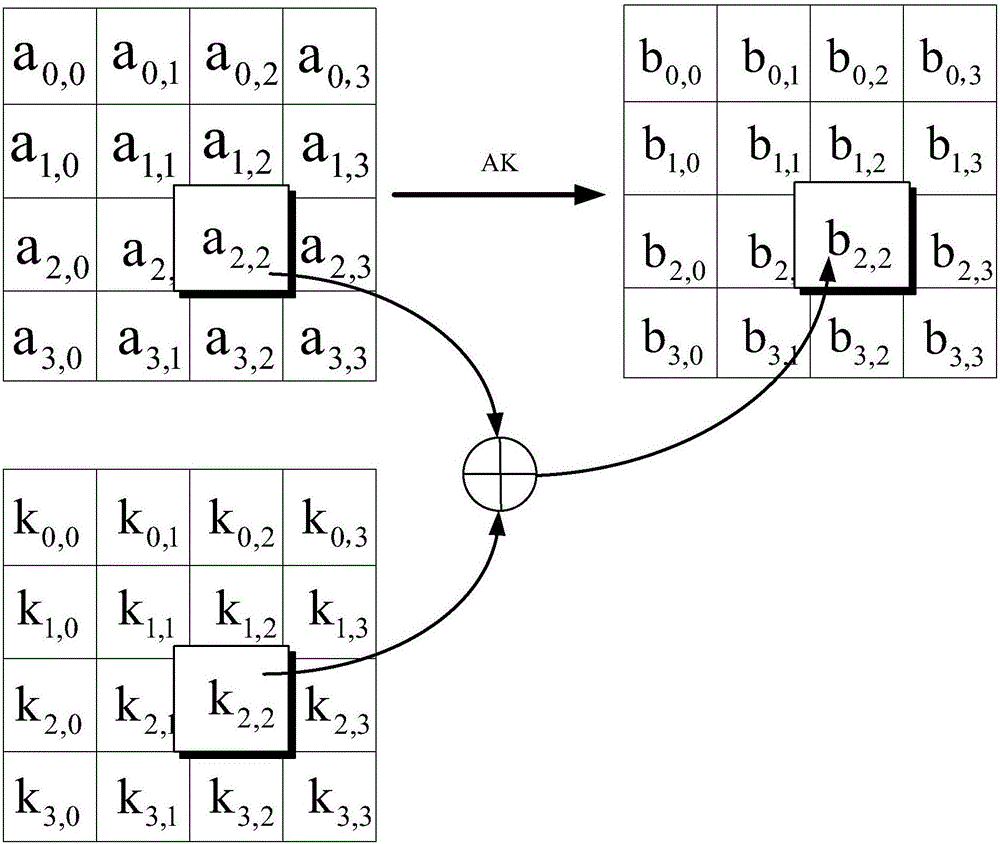
[0262] 1002. The encryption device calculates input mask data according to the pre-stored affine extension mask and the input affine extension mask in the plaintext.
[0263] Specifically, in the embodiment of the present invention, the affine extension mask is an affine transformation matrix for mapping m-bit data to n-bit data, where m and n are preset positive integers, and n>m.
[0264] In this way, after performing the affine expansion transformation in step 1002, the plaintext can be expanded from an m-dimensional column vector to an n-dimensional column vector. Exemplarily, assuming that the plaintext input in the embodiment of the present invention is 128 bits, the input plaintext can be extended from 128 bits to 16n bits by mean...
Embodiment 3
[0293] An embodiment of the present invention provides a method for generating a decryption function. Specifically, as Figure 12 As shown in , the method includes the following steps:
[0294] 1201. The device for generating a decryption function obtains a random seed and an original key.
[0295] Specifically, in the decryption function generation method provided in the embodiment of the present invention, the decryption function generation device first needs to obtain a random seed and an original key.
[0296] A random seed is a fixed-length bit string and can be used to generate random numbers by using a random number generator. A random number generator can be viewed as a function g(x) where the input is a fixed-length random seed, such as a k-bit string, and the output is a sequence of random numbers of any number of bits in length and used as a source of random numbers for subsequent use; And the key is a set of information codes, and the key participates in the "op...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com