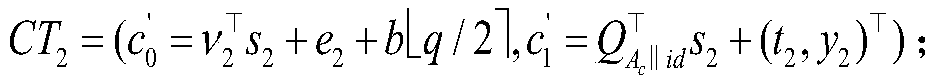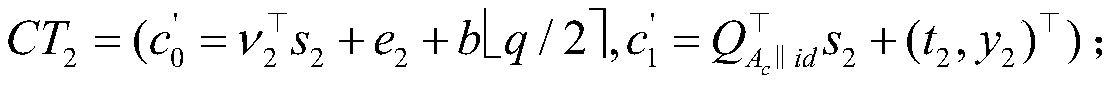Cloud storage ciphertext data public key searchable encryption method under the standard model
A standard model and encryption method technology, applied in the field of cyberspace security, can solve problems such as insecurity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] Describe technical scheme of the present invention in detail below:
[0037] The initial stage of the system: the system first sets the security parameters required by the lattice cipher algorithm, and runs the trapdoor generation function to generate the public-private key pair of the data receiver and the cloud server. The system then randomly selects two uniform random n×m matrices and two n-dimensional vectors: set a special vector encoding function.
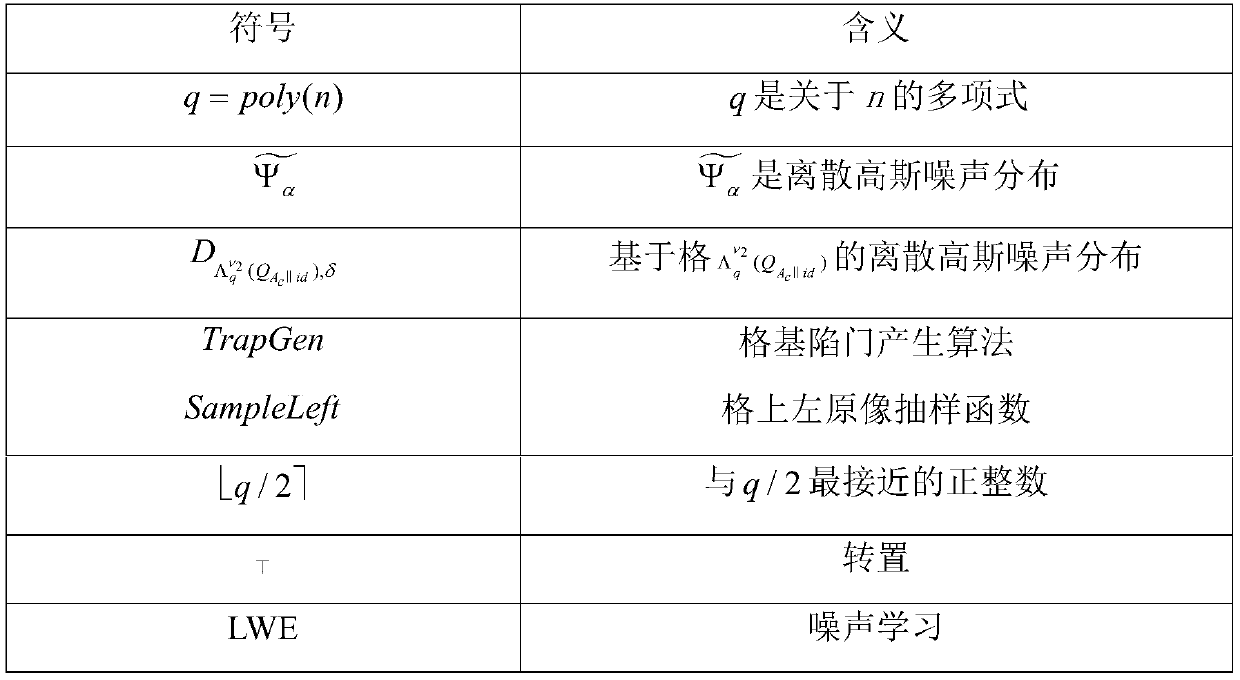
[0038]Keyword ciphertext generation stage: the data owner calculates the public matrix associated with the keyword, and obtains the first component of the keyword ciphertext according to the LWE encryption idea; the data owner selects a random challenge identity, and calculates The public matrix associated with it also obtains the second component of the keyword ciphertext according to the LWE encryption idea.
[0039] Search trapdoor generation stage: the data receiver uses his own private key, and according to the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com