One-way process forward-secure technology implement method
A technology of forward security and implementation method, which is applied in the field of one-way process forward security technology realization, can solve the unsolved problems of mobile communication forward security technology channel resources, calculation efficiency, etc., and achieve easy implementation, high fault tolerance, logic simple effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
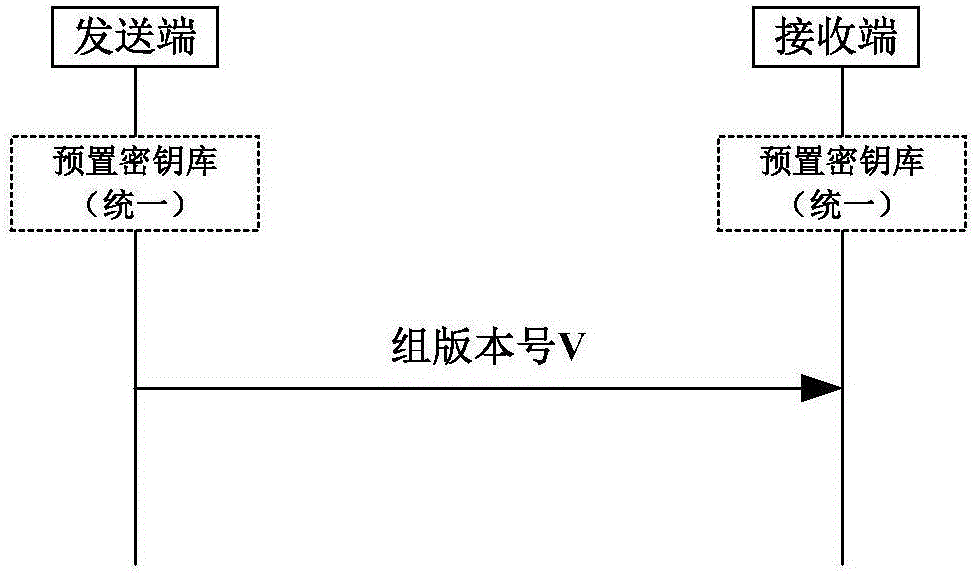
[0063] In order to make the purpose and technical solution of the present invention clearer, based on the method proposed above, a specific example workflow of one-way process forward security interaction will be given according to the actual process scenario in the end-to-end non-center mode.
[0064] Such as Figure 5 as shown, Figure 5 It is a schematic flow chart of Embodiment 1 of the present invention. In this scenario, there are two types of devices, the sending end and the receiving end, which mainly include the following steps:
[0065] Step 501: Preset the same keystore at the sending end and the receiving end respectively;
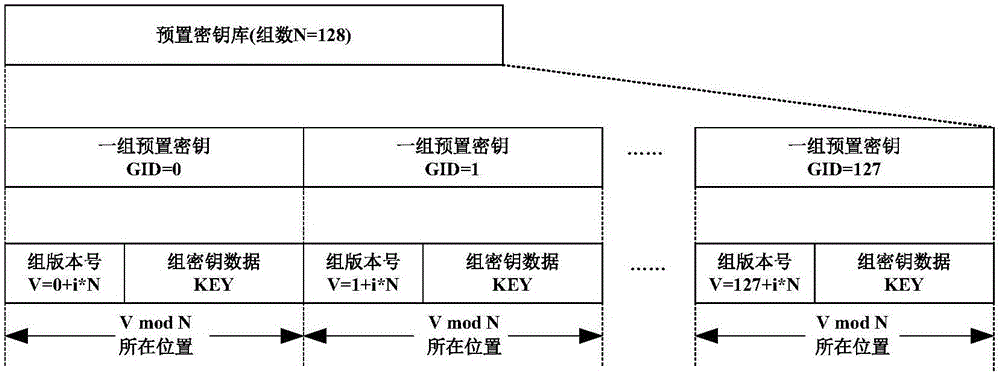
[0066] Set the number of keystore groups N=128, the group number GID is 0~127, the initialization keystore of the sending end is Data_O (the format is: group version number V_O+group key data KEY_O), the initialization keystore of the receiving end is Data_T( The format is: group version number V_T+group key data KEY_T). The current versions...
Embodiment 2
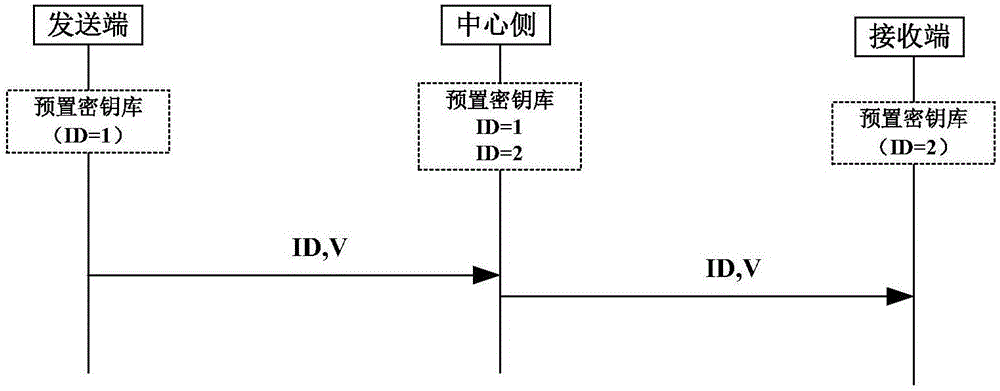
[0076] In order to make the purpose and technical solution of the present invention more clear, based on the method proposed above, a specific example workflow of one-way process forward security interaction will be given according to the actual process scenario in the centered mode.
[0077]In this scenario, there are three types of devices: the sender, the center, and the receiver. Set the number of keystore groups N = 128, the group number GID is 0 to 127, and the initialization keystore of the sender (ID = 1) is Data_O (format It is: group version number V_O+group key data KEY_O), and record the current version Cur_V_O=0 of the sending end; the initialization keystore of the receiving end (ID=2) is Data_T (the format is: group version number V_T+group key data KEY_T ), and record the current version of the receiving end Cur_V_T=0; the central side saves the keystore and the current initial version information of the sending end and the receiving end as (ID=1, V_O_C=0, KEY_O...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com