Method and apparatus for preventing malicious submission of webpage request
A web page request and malicious technology, applied in the field of network communication, to avoid the instantaneous increase of load and prevent malicious users from frequently submitting a large number of requests to the website
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
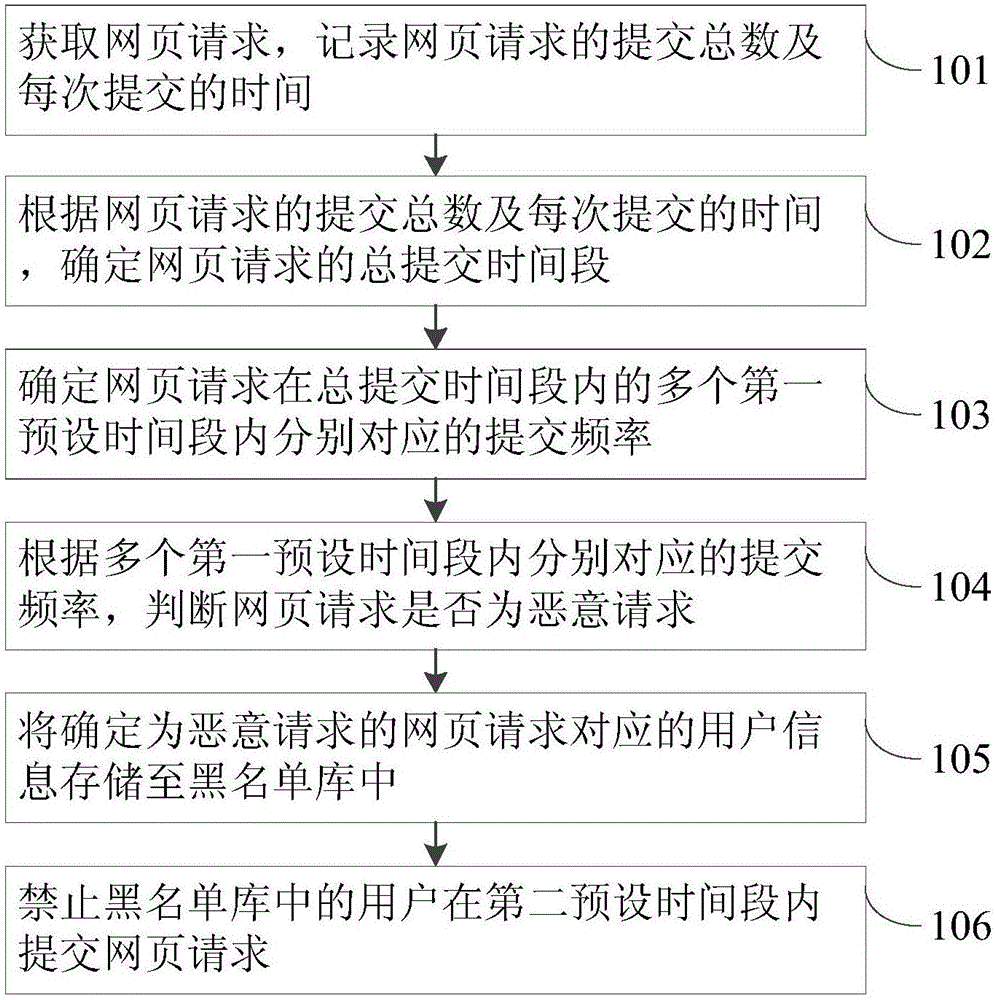
[0046] The embodiment of the present invention discloses a method for preventing malicious submission of a web page request, refer to figure 1 , figure 1 It is a flow chart of the method for preventing malicious submission of webpage requests provided by the method embodiment 1 of the present invention, including:
[0047] S101. Obtain webpage requests, and record the total number of webpage requests submitted and the time of each submission.
[0048] A web page request is a request message submitted by a user to a server using a computer (client). Generally, it includes the request method for the resource, the identifier of the resource, and the protocol used in the first line of the message.
[0049] In the first embodiment of the method of the present invention, the system records the time each user submits a web page request and the total number of times each user submits a web page request. Optionally, record the total number of web page requests submitted and the time of each s...
Embodiment 2
[0070] The embodiment of the invention also discloses a method for preventing malicious submission of a web page request. figure 2 , figure 2 This is another flowchart of the method for preventing malicious submission of webpage requests provided by the method embodiment 2 of the present invention, and on the basis of the method embodiment 1, further includes:
[0071] S107. According to the users in the preset whitelist library, allow the webpage request submitted by the users in the whitelist library.
[0072] Corresponding to some large customers or old users, there is no need to determine whether the web page requests they submit are malicious requests, so these users can be added to the whitelist database. This will not only reduce the amount of system calculations, but also improve the efficiency of the website.
[0073] S108. Store multiple webpage requests determined as malicious requests into folders distributed by hash rules.
[0074] When storing webpage requests, the sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com