Physical slicing method based on SDN technology
A technology of physical slicing and technology, applied in the field of physical slicing based on SDN technology, can solve problems such as slicing technology cannot meet security requirements, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
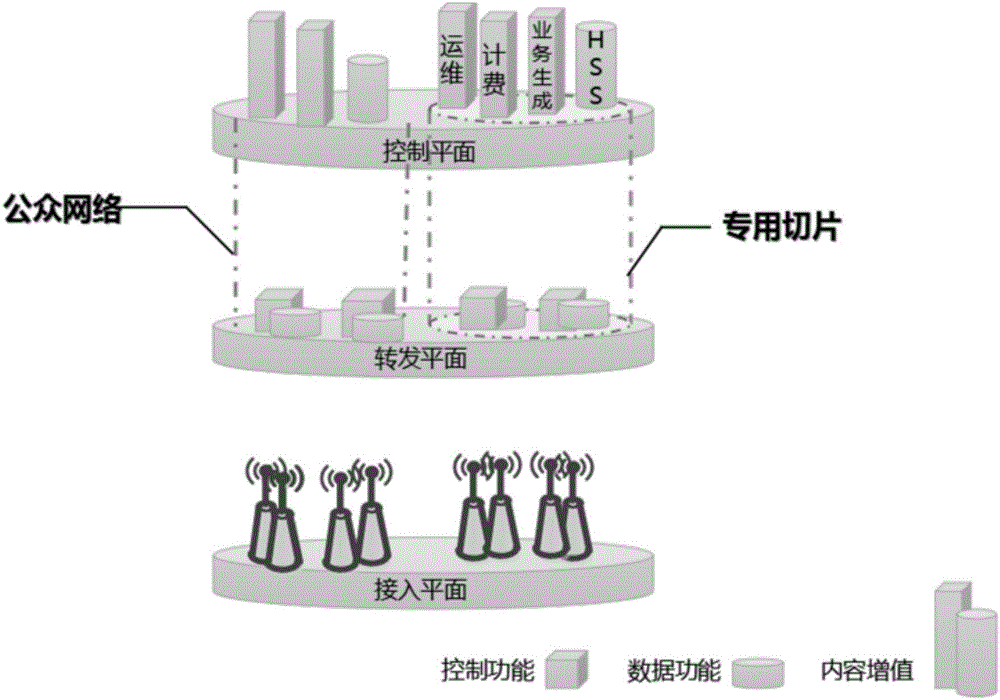
[0049] Embodiment one: if Figure 4 shown.
[0050] The specific physical slicing method includes the following steps:
[0051] Step S1, the operator sets dedicated infrastructure resources in the forwarding plane, and divides the set dedicated infrastructure resources into three levels: primary, intermediate and advanced;
[0052] Specifically, the dedicated infrastructure resources are devices certified by organizations with information security device certification qualifications.
[0053]Classify infrastructure resources according to their trust level and the functions they can realize; specifically, special infrastructure resources are divided into primary and low levels according to their level of trust and the functions they can realize. , intermediate and advanced;
[0054] The credible level division mechanism of dedicated infrastructure resources is based on Article 4 of the "Information Security Level Protection Management Measures (Trial)": the security protecti...
Embodiment 2
[0077] Embodiment 1 is described by taking an online payment scenario as an example.
[0078] 1) Set up dedicated infrastructure resources and grade them; the infrastructure resources required for online payment are computing equipment and data storage equipment. Therefore, the operator's infrastructure resources should include these two types of equipment.
[0079] 2) Determine the user level; users who can provide online payment functions are divided into levels according to the scale of use they can provide and the security level of the user (ordinary user, VIP user, etc.).
[0080] 3) Form a physical slicing template; according to the user level, select a corresponding level of equipment (for example, can provide 1000 operations / second computing capability, 10000 operations / second computing capability, etc.) in the dedicated infrastructure resources to form a physical slicing template.
[0081] 4) After receiving user requirements, form physical slices through the NFV orc...
Embodiment 3
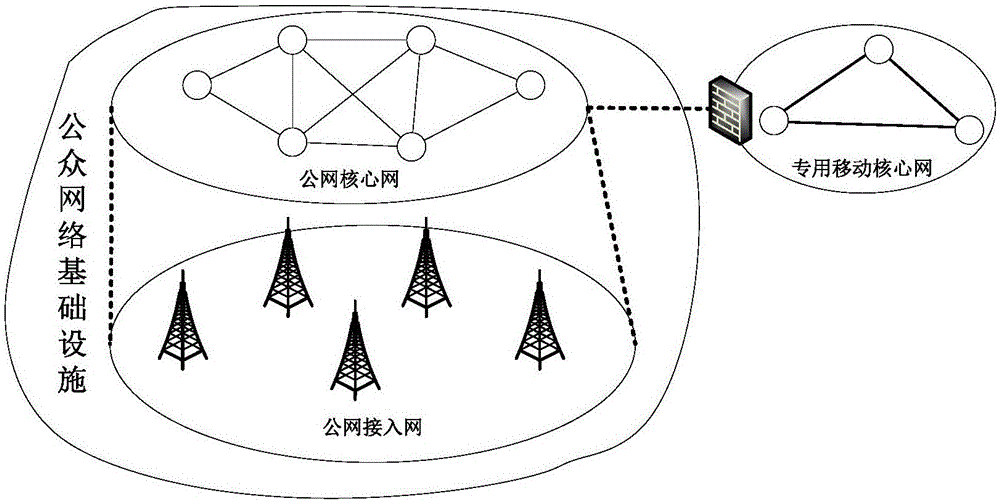
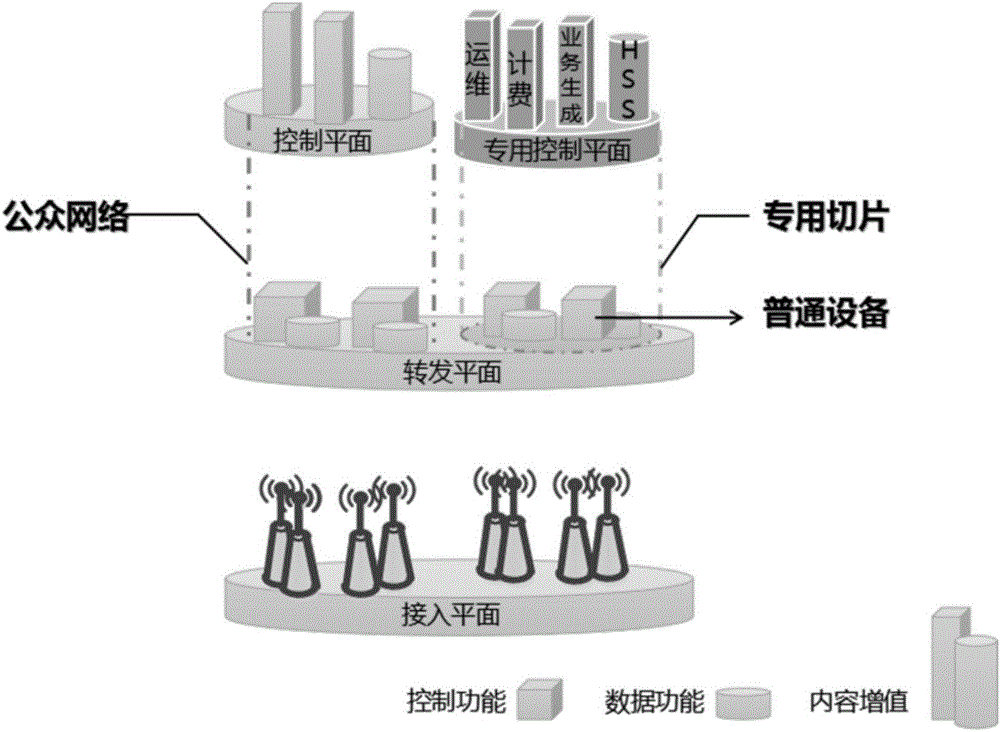
[0083] For some applications with higher security levels and lower application flexibility requirements, dedicated applications and business support systems and dedicated forwarding planes can be deployed independently. The dedicated forwarding plane has only dedicated equipment, which is for certain specific services and is separately divided. The forwarding plane of the public network does not matter. Private services are interconnected with the public network through limited security isolation gateways. Private services refer to services with a particularly high security level. If the services are threatened, it will cause irreparable damage to the entire system. For example, the control command business of the control system of a special industry. Such as Figure 6 shown. Compared with the above technologies, this alternative not only uses dedicated infrastructure resources, but also completely separates dedicated infrastructure resources from public network equipment, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com