Method and device for detecting man-in-the-middle attack
A detection method and attack detection technology, applied in the field of network security, can solve the problems of weak detection technology, failure to improve the security of SMTPS services, and inability to completely solve the problems of SSL encryption services not being attacked by man-in-the-middle, so as to achieve wide application range and facilitate dynamic expansion Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
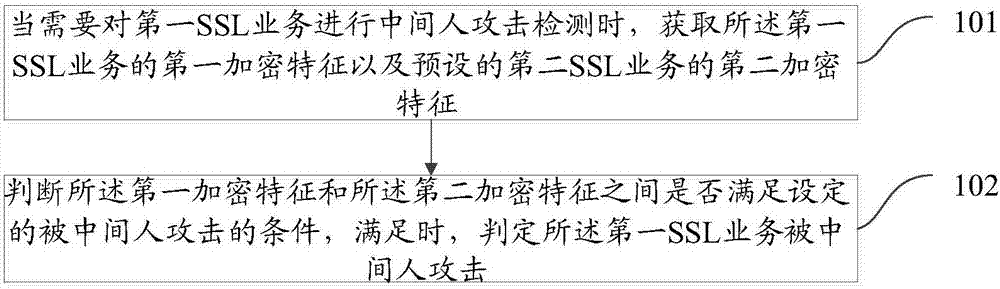
[0055] image 3 It is a schematic diagram of the implementation flow of a detection method for a man-in-the-middle attack according to an embodiment of the present invention. The method includes:
[0056] Step 101: When it is necessary to detect a man-in-the-middle attack on the first SSL service, obtain the first encryption feature of the first SSL service and the preset second encryption feature of the second SSL service;
[0057] Specifically, when it is necessary to detect whether the first SSL service is attacked by a man-in-the-middle, the first encryption feature of the first SSL service and the preset second encryption feature of the second SSL service are obtained, so as to and the second encryption feature to determine whether the first SSL service is attacked by a man-in-the-middle.
[0058] Here, the first SSL service and the preset second SSL service are services carried by different application layer protocols based on the SSL encryption protocol; for example, f...
Embodiment 2
[0125] Embodiment 1 of the present invention will be further described below through a specific example. In this implementation, accessing the application server in mode A is the first SSL service, and the certificate trust chain for accessing the application server in mode A is the first encryption feature. Modes B and C Access to the application server is the second SSL service. The certificate trust chain for accessing the application server in methods B and C is the second encryption feature. The certificate trust chain for accessing the application server in method A is the same as the certificate trust chain for accessing the application server in method B and C. is the condition to be satisfied between the first encryption feature and the second encryption feature; Figure 5 It is a schematic diagram of a specific implementation flow chart of the detection method of the second man-in-the-middle attack in the embodiment of the present invention, and the method includes: ...
Embodiment 3
[0151] Embodiment 1 and Embodiment 2 are further described below through a specific example. In this implementation, sending emails using the SMTPS protocol is the first SSL service, and the certificate trust chain for sending emails using the SMTPS protocol is the first encryption feature. , using POP3S, IMAPS, HTTPS and other protocols to send e-mail is the second SSL service, using POP3S, IMAPS, HTTPS and other protocols to send e-mail certificate trust chain is the second encryption feature, using SMTPS protocol to send e-mail certificate trust chain and The same certificate trust chain for sending emails using POP3S, IMAPS, HTTPS and other protocols is a condition to be satisfied between the first encryption feature and the second encryption feature; email is the main communication medium for most organizations and is indispensable for users Communication tools, so the importance of email security is undeniable. The technical details of this embodiment will be described i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com