Application system data safety protection method and system combined with cloud storage
An application system and data security technology, applied in the field of data security, can solve the problems of not being universal and not convenient for rapid development and deployment, and achieve the effect of improving work efficiency and reducing transformation costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
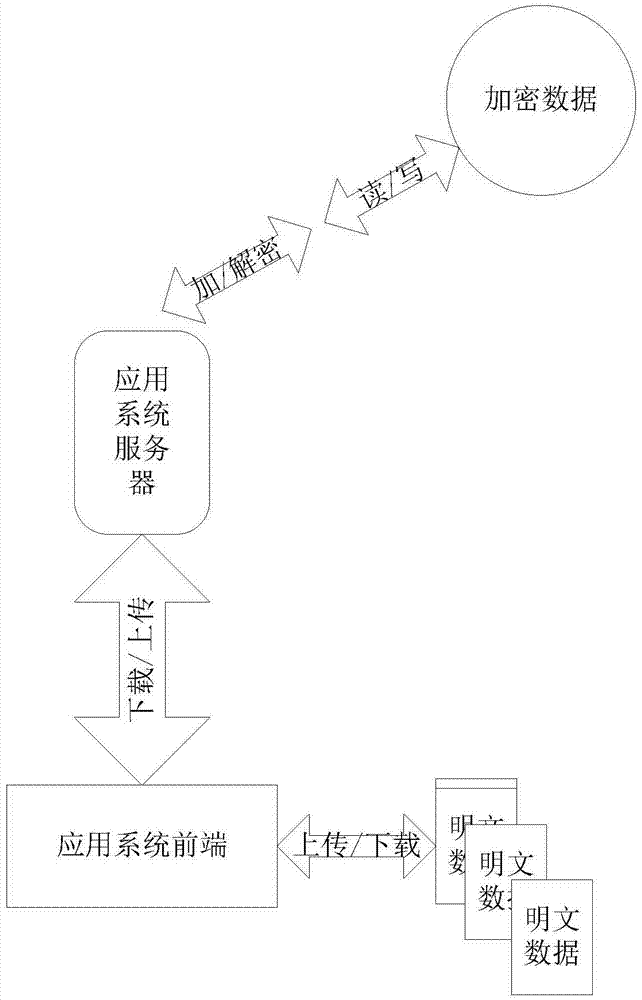
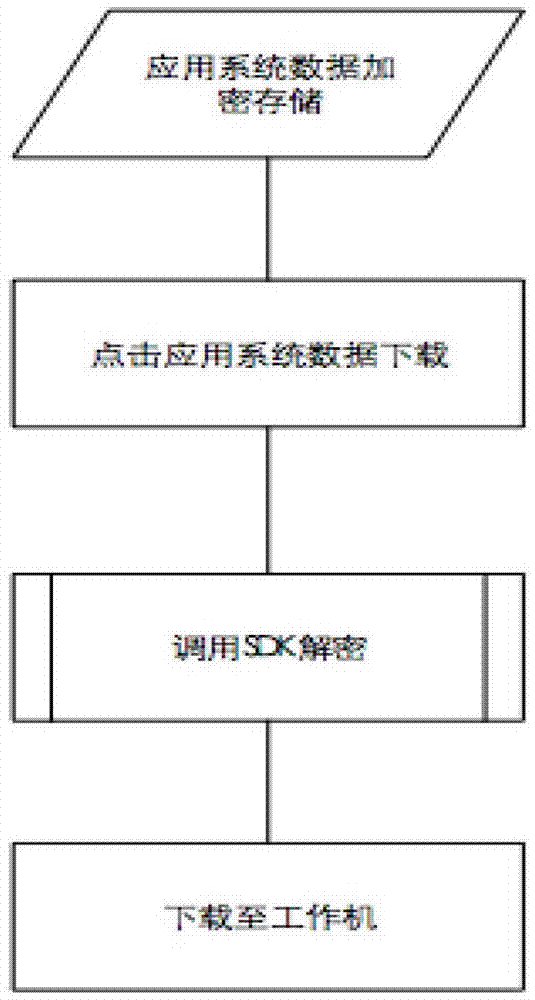
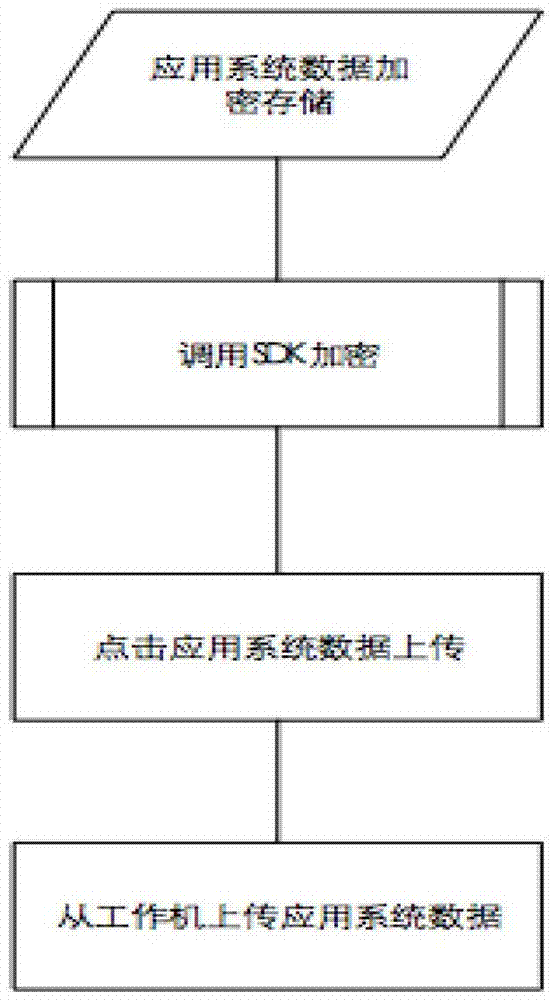
[0036] The business system data download isolation of embodiment 1 is as follows: Figure 7shown. The system includes the situation where the terminal is used locally. After the file is encrypted and stored in the cloud storage disk through the data security server, the terminal downloads it from the cloud storage disk when it is used. When it is used locally, the terminal cannot directly communicate with the cloud storage disk without going through the data security server. interact. The data that needs to be saved by the application system server is encrypted by the data security server and stored in the cloud storage disk. When the terminal is in use, it can obtain the location of the cloud storage disk where the document is located by querying the database, download it from the cloud storage disk to the terminal isolation disk, and then the client on the terminal The program opens. Another hidden function of this example is that the path of the cloud storage disk and the...
Embodiment 2
[0037] Embodiment 2 is a standard usage scenario. The file is still used through the application system, but the file is saved and protected by the data security server, and the terminal identification is added. The business system data download isolation of embodiment 2 is as follows Figure 8 shown. In this embodiment, there are multiple application system servers and cloud storage disks, and a unified data security server performs file encryption, decryption, distribution and storage, and data access is realized through the browser where the terminal is located. The files are stored on the network disk through the security server. When the user downloads or uploads the file, the application system accesses the file from the network disk through the security server.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com