User authentication method and device
A technology for user identity and verification methods, applied in the direction of user identity/authority verification, etc., can solve problems such as affecting user experience, difficult identification, theft of money or virtual property, etc., to improve system security, ensure verification accuracy, and improve user experience. The effect of experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
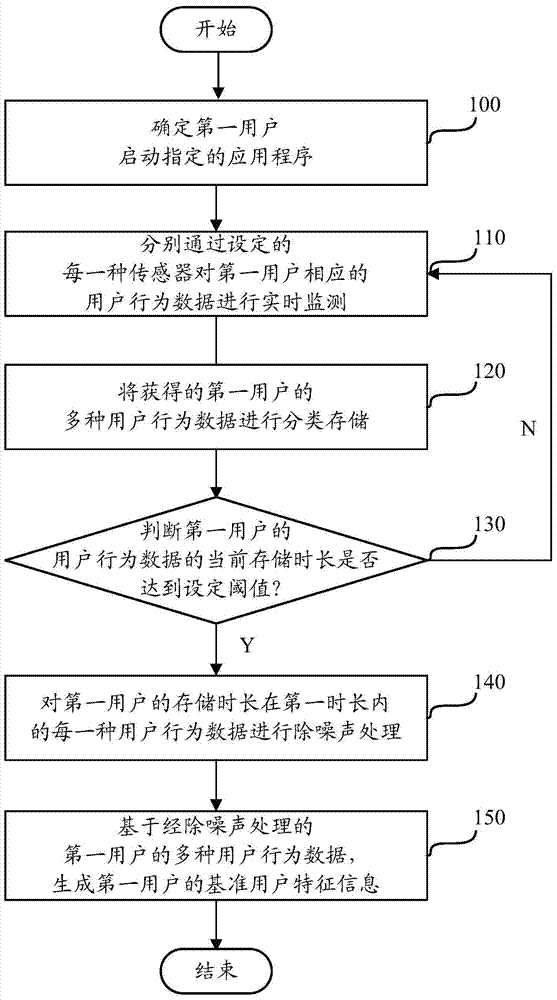
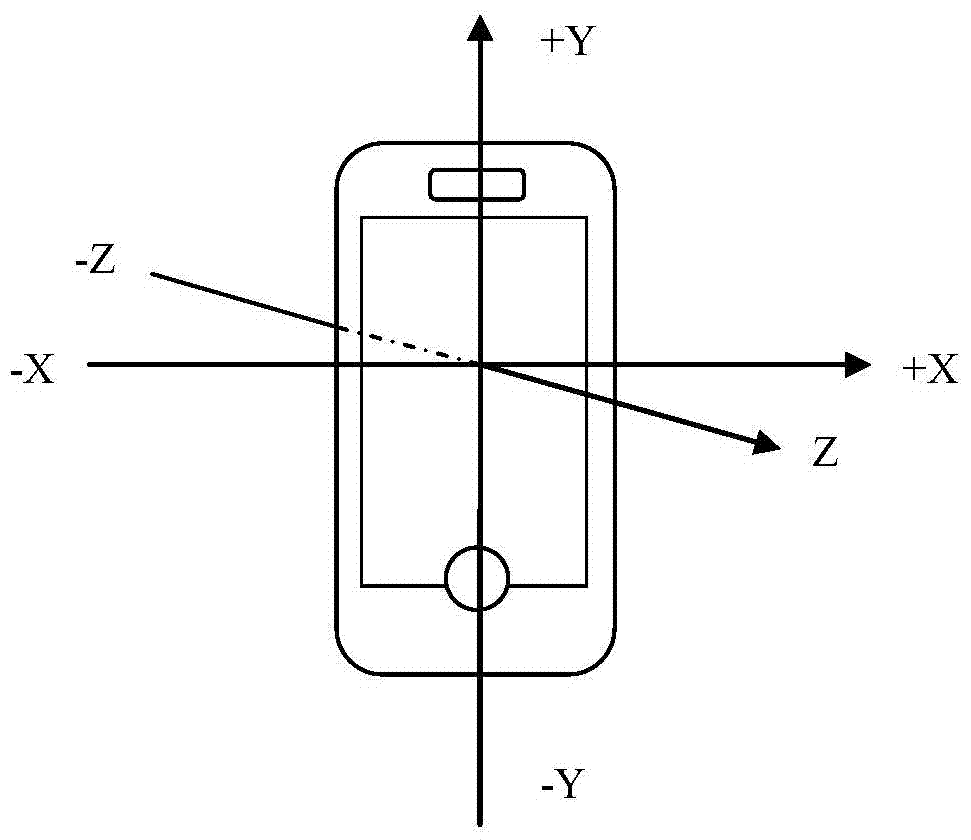
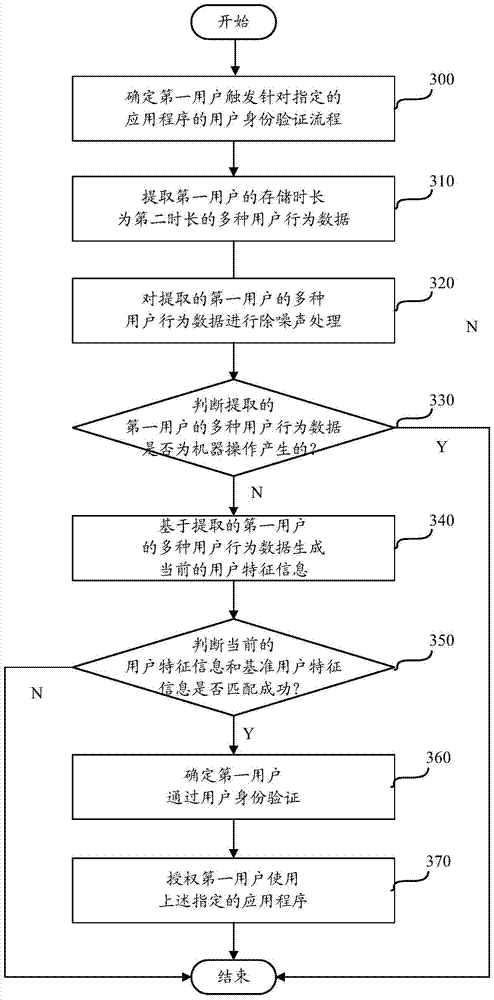
[0074] In order to reduce the operation complexity of the verification process and ensure the verification accuracy, in the embodiment of this application, various sensors are used to collect user behavior data in real time in advance, and then the user identity verification device uses a specific algorithm to collect The various collected user behavior data are integrated into the benchmark user characteristic information, so that when the user triggers the user identity verification process, the user identity verification device can generate current user characteristic information based on the user behavior data collected in the second period, and pass the current According to the matching degree of the user characteristic information and the benchmark user characteristic information, it is judged whether the user authentication is successful.
[0075] Preferred embodiments of the present application will be described in further detail below in conjunction with the accompanyi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com