Online payment method and system thereof
An online payment and legal technology, applied in the Internet field, can solve problems such as low security, low code reusability, and unreasonable server design, so as to reduce labor and time costs and avoid security threats.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
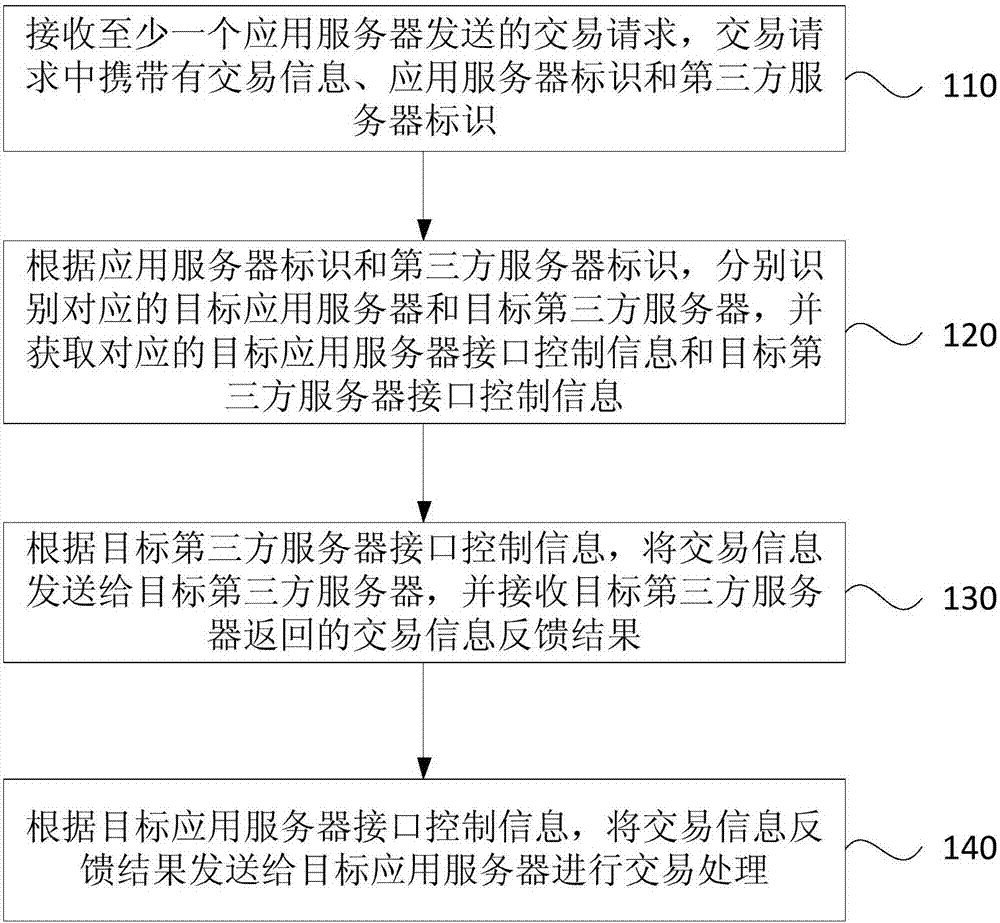
[0026] figure 1 It is a schematic flow chart of an online payment method provided in Embodiment 1 of the present invention. The method is suitable for online order processing. The method can be executed by an online payment system, and the online payment system can be implemented by software and / or hardware. Such as figure 1 As shown, the method includes:
[0027] Step 110: Receive a transaction request sent by at least one application server, where the transaction request carries transaction information, an application server identifier, and a third-party server identifier.
[0028] The payment system can receive transaction requests sent by one or more application servers connected to it, and transactions include: order payment, order refund, order refund progress query and other operations related to online transactions.
[0029] Among them, the transaction information carried in the transaction request includes: transaction time, order number, order status, product name, product...
Embodiment 2
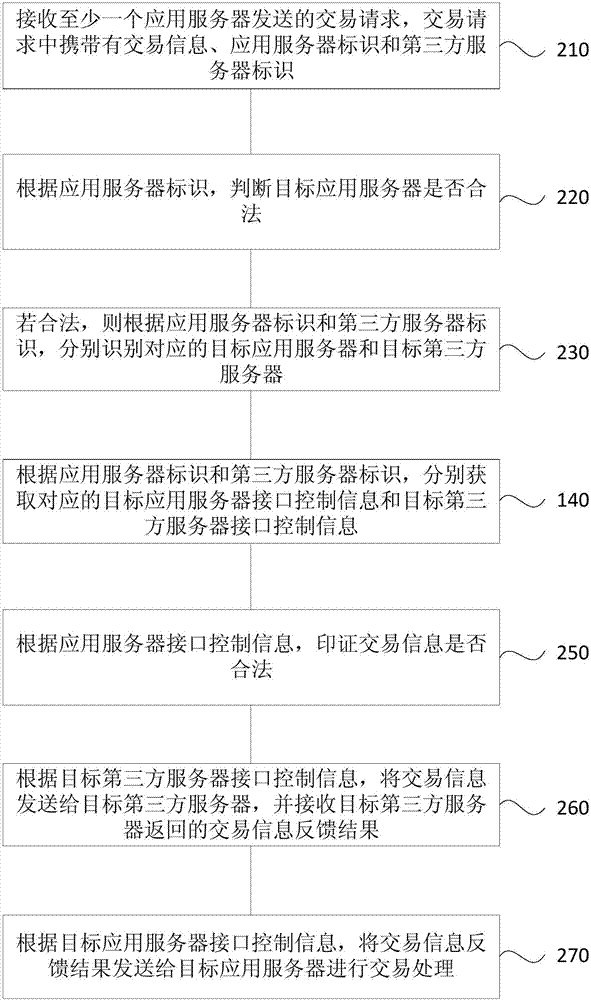
[0037] figure 2 It is a schematic flowchart of an online payment method provided in the second embodiment of the present invention. The embodiment of the present invention specifically optimizes step 120 on the basis of the above-mentioned embodiment 1, and the method includes:
[0038] Step 210: Receive a transaction request sent by at least one application server, where the transaction request carries transaction information, an application server identifier, and a third-party server identifier.
[0039] Step 220: Determine whether the target application server is legal according to the application server identifier.
[0040] The application server has a unique identification identifier, and verifying the legitimacy of the application server according to the identifier of the application server is to prevent malicious requests from damaging the system. When the identification of the application server matches the identification of the application server pre-assigned by the paymen...
Embodiment 3
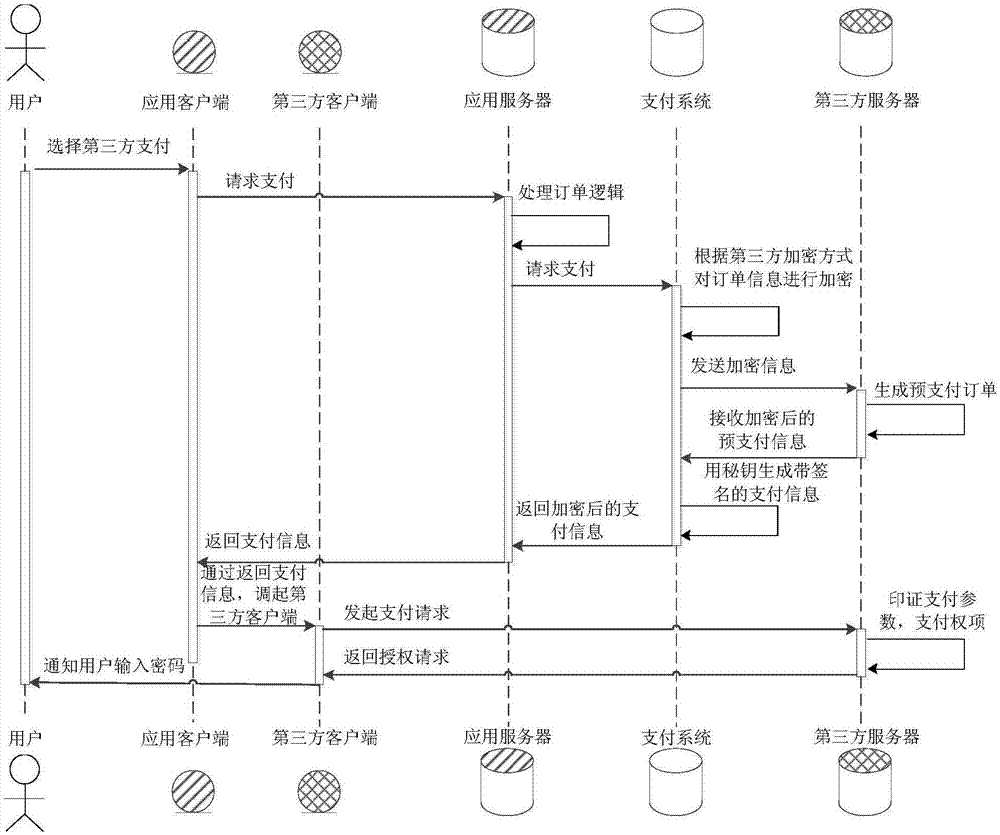
[0058] Image 6 It is a structural block diagram of an online payment system provided in the third embodiment of the present invention. Such as Image 6 As shown, the system includes:
[0059] The transaction request receiving module 610 is configured to receive a transaction request sent by at least one application server, and the transaction request carries transaction information, an application server identifier, and a third-party server identifier;
[0060] The interface control information acquisition module 620 is configured to identify the corresponding target application server and the target third-party server according to the application server identifier and the third-party server identifier, and obtain corresponding target application server interface control information and target third-party server interface control information ;
[0061] The transaction information processing module 630 is configured to send transaction information to the target third-party server ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com