Method for managing lock in cluster, lock server and client
A management method and client technology, which is applied in the field of lock management in the cluster, can solve the problems that the lock server does not know the client, is in the write lock waiting state, and client B cannot apply for the write lock, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
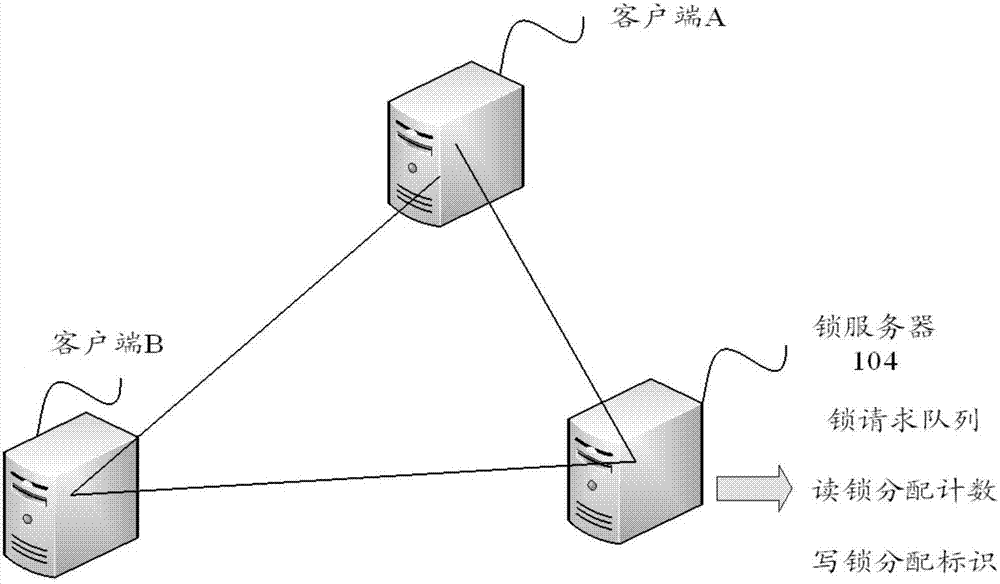
[0080] Such as figure 2 As shown, the cluster in the embodiment of the present invention includes a lock server, client A and client B, and client A and client B communicate with the lock server using the RDMA protocol respectively, wherein the lock server memory stores the lock request queue, read lock Allocation count and write lock allocation identifier, see the description below for details.
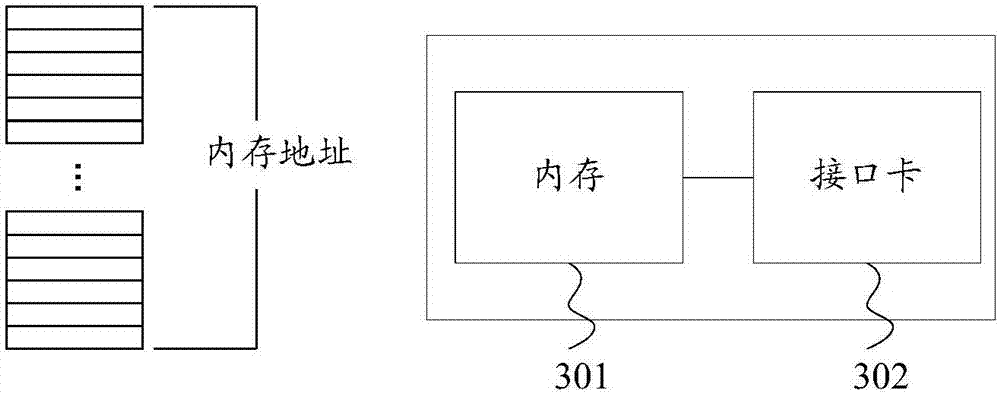
[0081] Such as image 3 As shown, the lock server includes a memory 301 and an interface card 302, wherein the interface card 302 can be a network interface card (Network Interface Card, NIC) supporting the Ethernet protocol (Ethenet), or an interface card based on the InfiniBand protocol or other RDMA-capable An interface card that implements a protocol for remote direct access to memory. The memory 301 in the embodiment of the present invention may be a dynamic random access memory (Dynamic Random Access Memory, DRAM), a dual-inline-memory-modules (DIMM), a semiconductor memory (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com