Internet of things intrusion detection method based on finite state automaton and detection system
A finite automaton and intrusion detection technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems of low performance of IoT terminal equipment, inability to use complex cryptographic algorithms, and insufficient single-point computing power.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] In order to further illustrate the technical means and effects adopted by the present invention to achieve the intended purpose, the specific implementation, structural features and effects of the present invention will be described in detail below in conjunction with the accompanying drawings and examples.
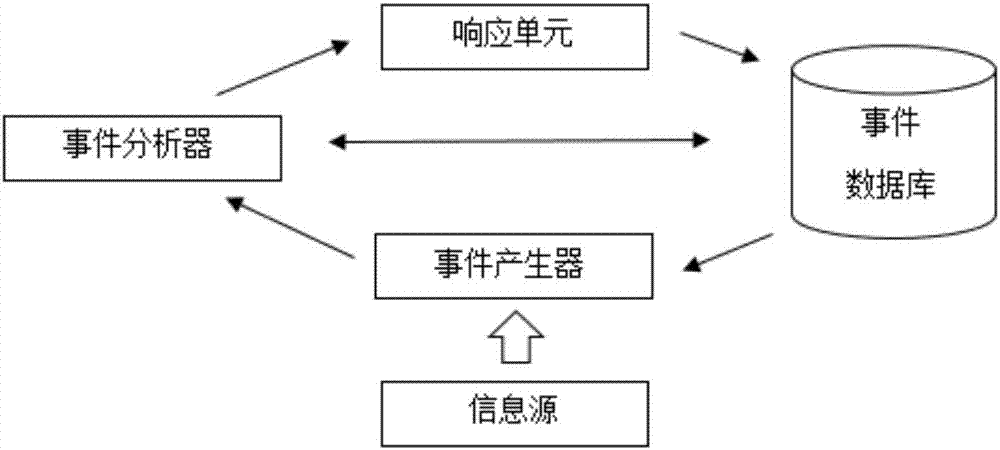
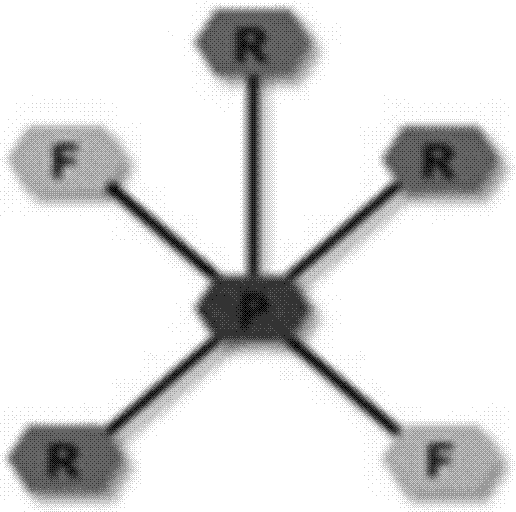
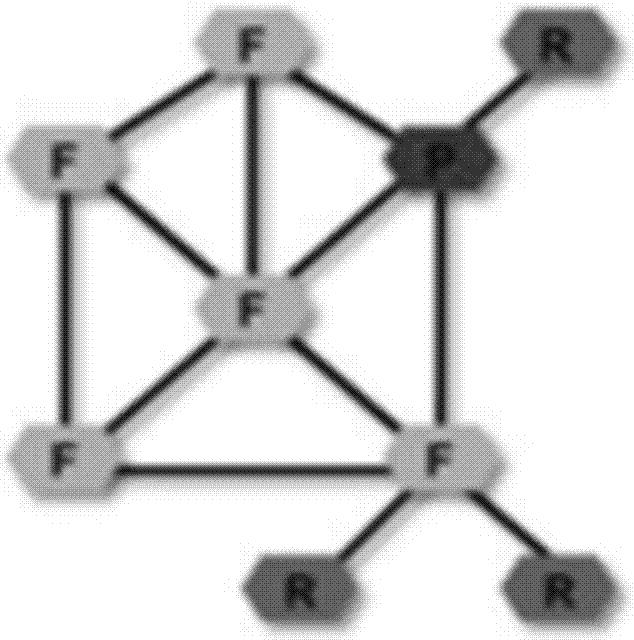
[0069] In the Internet of Things, a large number of sensors, RFID tag devices, CCTV network cameras and other sensing devices with simple computing and storage capabilities will be used, which will greatly expand the network boundaries of the current Internet and provide information collection and information for future networks. function of the service. However, these sensing devices may work in an unsafe environment, and due to the limitation of their computing power, they cannot use complex cryptography mechanisms to protect themselves, and are easily interfered, captured, deciphered, or even tampered with and embedded in malicious attack programs by opponents, r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com