Anomaly detection method and device
An anomaly detection and anomaly technology, applied in the field of communication, which can solve the problem of few identifiable patterns and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
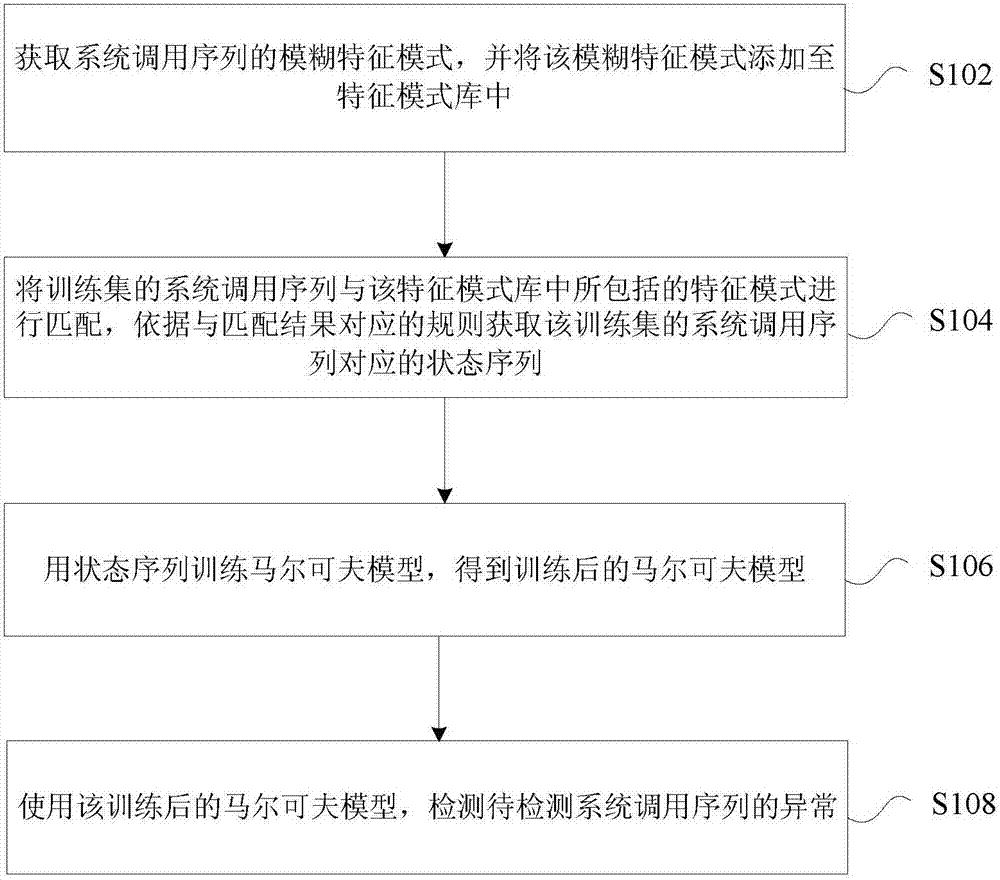
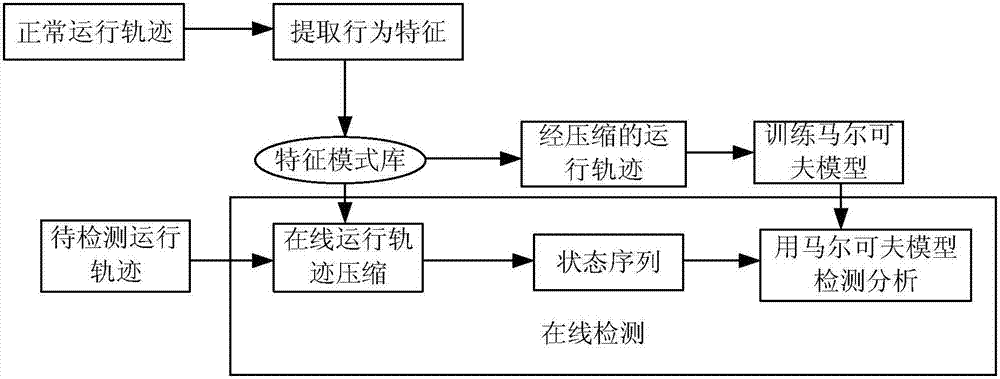
[0038] In this embodiment, an anomaly detection method is provided, figure 1 is a flow chart of anomaly detection according to an embodiment of the present invention, such as figure 1 As shown, the process includes the following steps:
[0039] Step S102, obtaining the fuzzy feature pattern of the system call sequence, and adding the fuzzy feature pattern to the feature pattern library;
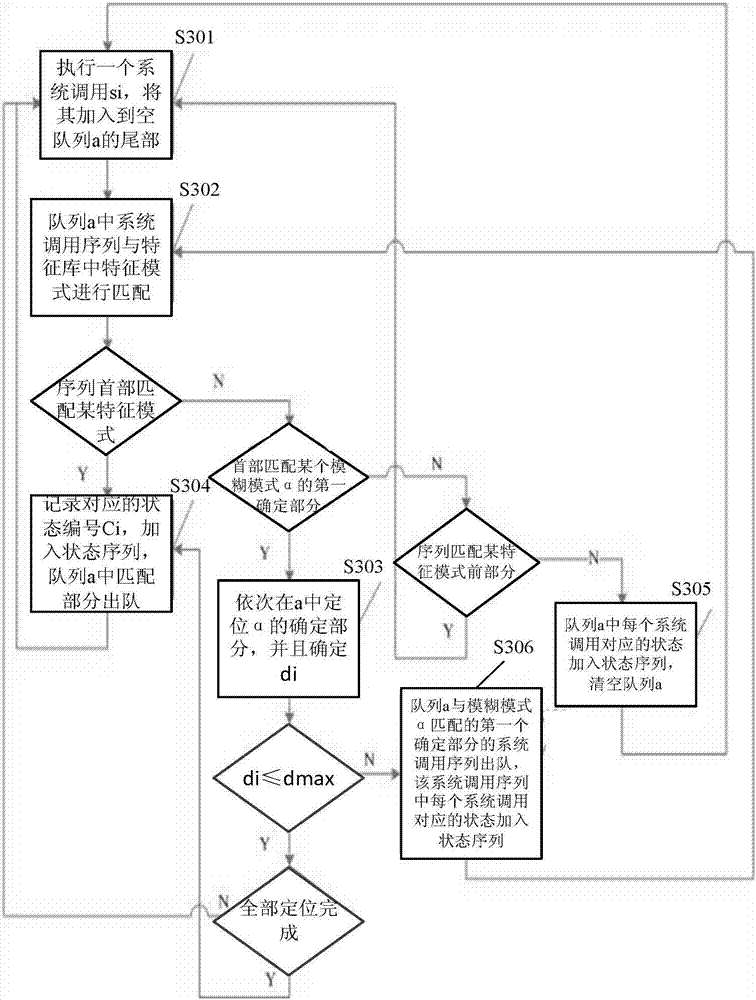
[0040] It should be noted that the aforementioned fuzzy feature mode is a feature mode including a definite mode and a fuzzy mode. Wherein, the definite pattern refers to a feature pattern formed in a definite order through multiple system calls. For example, if the system call sequence l∈C, and l is composed of a group of system calls in a definite order, then l is a definite pattern, and C is a characteristic pattern library, which is a set composed of characteristic patterns; the fuzzy pattern represents a class of system The characteristic pattern of the call sequence, for example, if ...
Embodiment 2
[0105] In this embodiment, an abnormality detection device is also provided, which is used to implement the above embodiments and preferred implementation modes, and what has been described will not be repeated. As used below, the term "module" may be a combination of software and / or hardware that realizes a predetermined function. Although the devices described in the following embodiments are preferably implemented in software, implementations in hardware, or a combination of software and hardware are also possible and contemplated.
[0106] Figure 4 is a structural block diagram of an abnormality detection device according to an embodiment of the present invention, such as Figure 4 As shown, the device includes:
[0107] 1) The first processing module 42 is used to obtain the fuzzy feature pattern of the system call sequence, and add the fuzzy feature pattern to the feature pattern library, wherein the fuzzy feature pattern is a feature pattern including a definite patt...
Embodiment 3
[0151] The embodiment of the invention also provides a storage medium. Optionally, in this embodiment, the above-mentioned storage medium may be configured to store program codes for performing the following steps:
[0152] S1. Obtain the fuzzy feature pattern of the system call sequence, and add the fuzzy feature pattern to the feature pattern library, where the fuzzy feature pattern is a feature pattern including a definite pattern and a fuzzy pattern, and the definite pattern represents that a plurality of system calls A feature pattern formed in a definite order, the fuzzy pattern representing a feature pattern of a type of system call sequence;
[0153] S2, matching the system call sequence of the training set with the feature patterns included in the feature pattern library, and obtaining the state sequence corresponding to the system call sequence of the training set according to the rules corresponding to the matching result;
[0154] S3, using the state sequence to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com