Authentication method of writing behavior characteristics based on wrist-worn electronic devices
A technology of electronic equipment and authentication methods, applied in digital data authentication, electrical digital data processing, instruments, etc., can solve problems such as observation attacks and guessing attacks, theft of unlocking methods, and incomplete security, achieving robustness and The effect of fault tolerance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
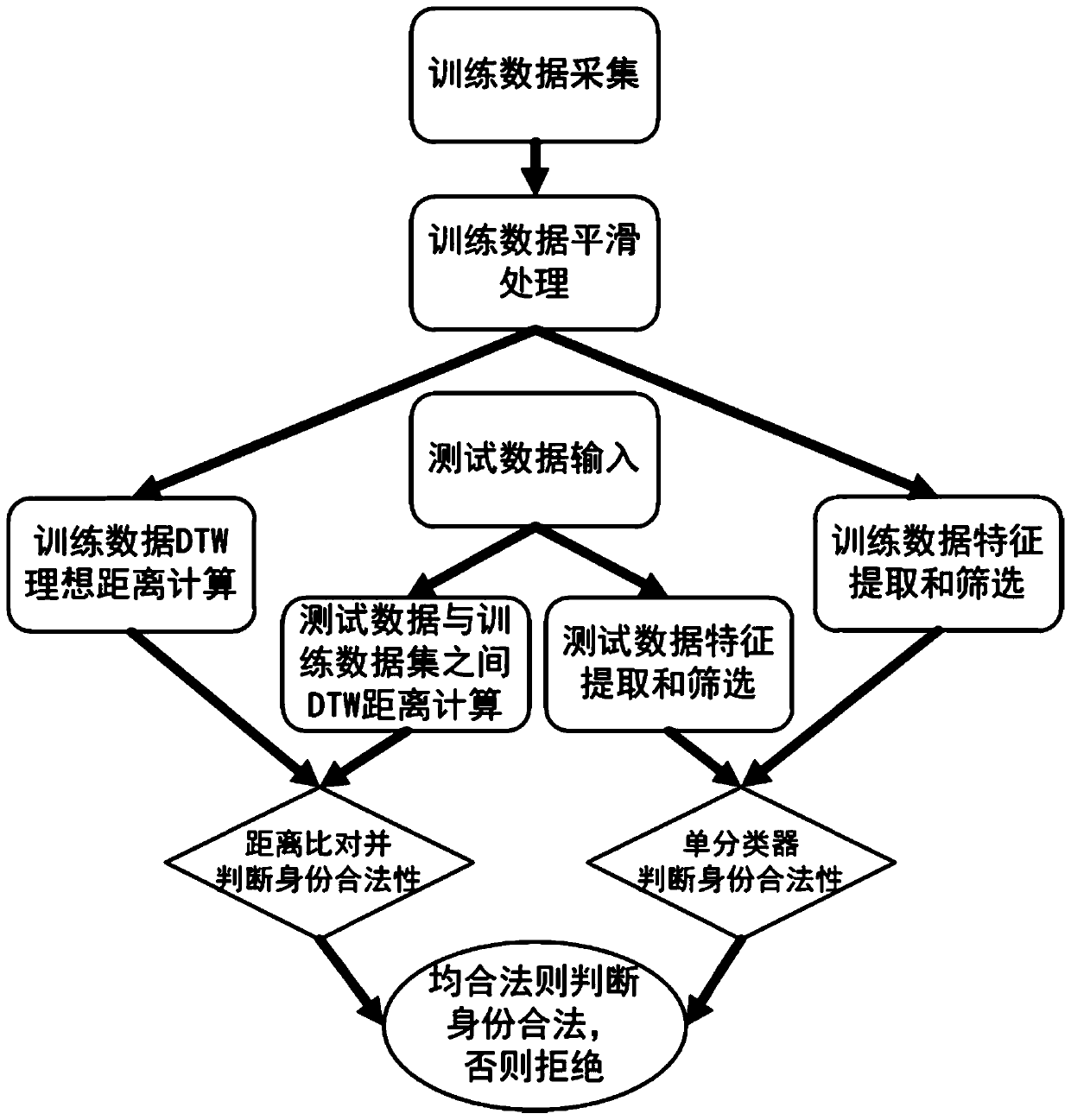
[0058] see figure 1 , the present invention is based on a writing behavior feature authentication method of a wrist-worn electronic device, which can be used to unlock the electronic device and realize the security protection of the electronic device or entity (such as a safe). The present invention includes two parts of user identity model construction and user identity authentication, and the specific implementation steps are as follows:
[0059] S1. The user identity model construction part includes the following steps:
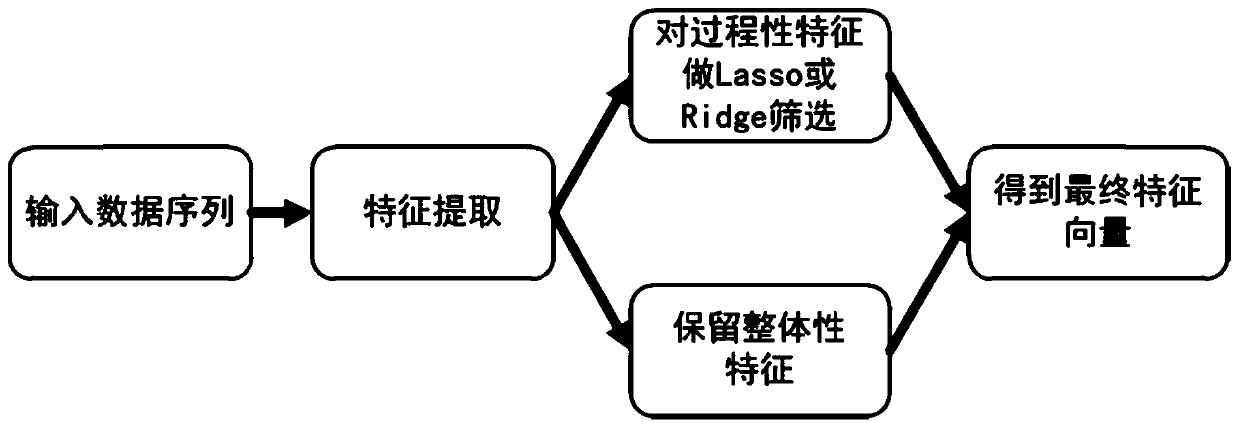
[0060] S1.1. When the user first starts training the system, let the user write the same word, Chinese character, signature or pattern with the same habit, and use the accelerometer and gyroscope to collect and record the user's writing data to form an identity model construction The required writing behavior training data set; the format of the writing data is: {time, x-axis acceleration, y-axis acceleration, z-axis acceleration, x-axis angular velocity,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com