A Time-based Network Hidden Channel Construction Method Based on Discrete Wavelet Transform
A technology of discrete wavelet transform and construction method, which is applied in the field of network information security, can solve problems such as changing, reducing hidden channel bandwidth, and difficulty in synchronizing communication parties, and achieves good robustness and good anti-detection effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] (1) Implementation process of covert communication
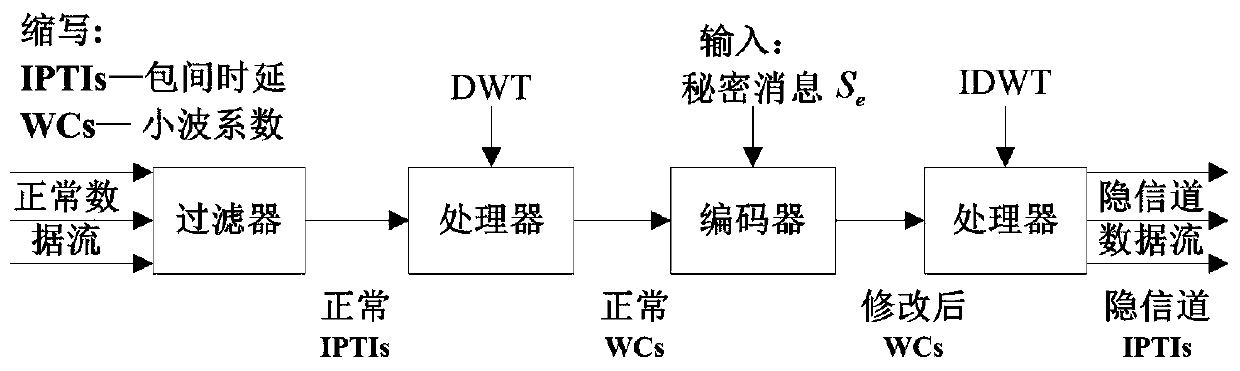
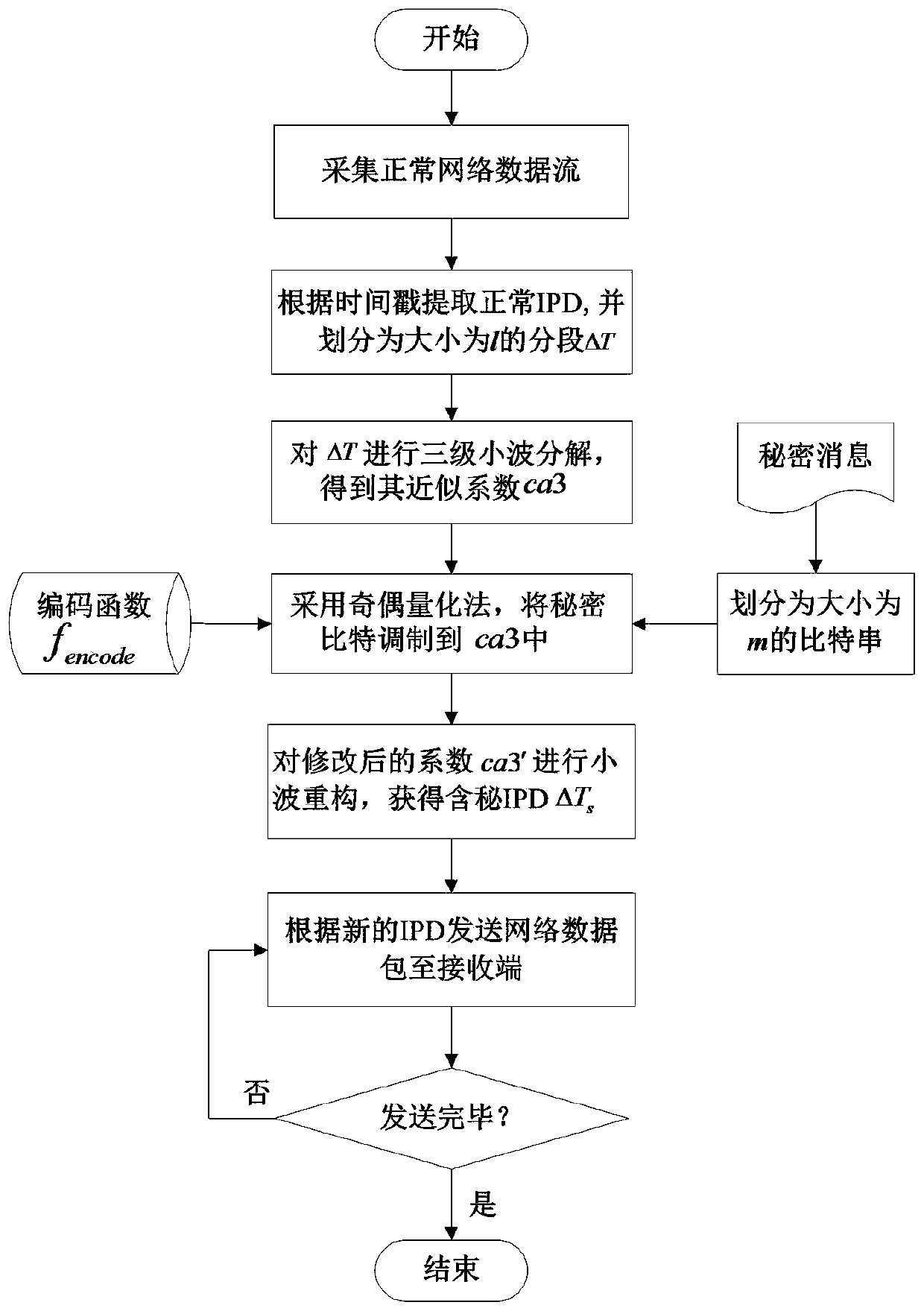
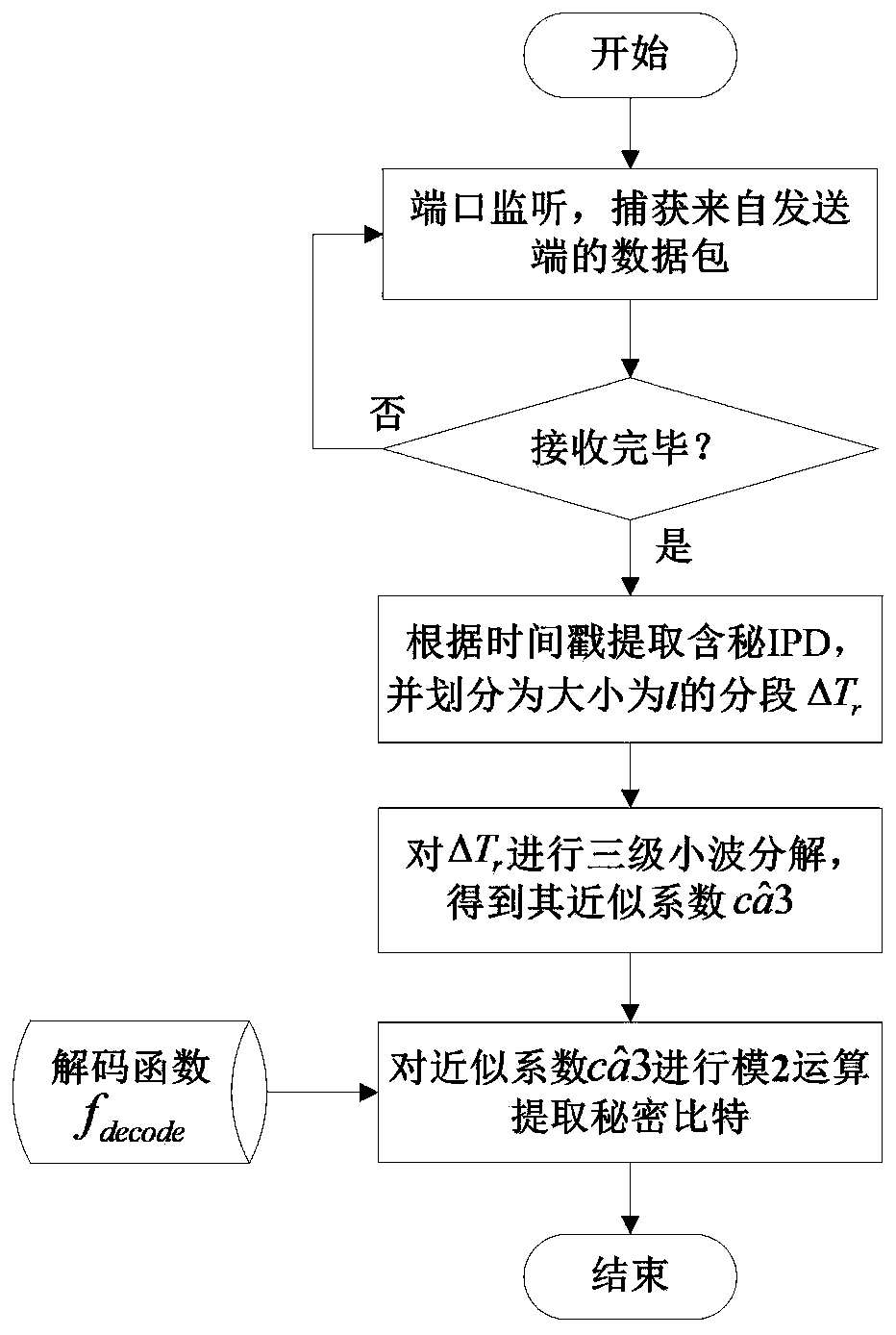
[0032] Utilize a kind of temporal covert channel method based on discrete wavelet transform (DWT) proposed by the present invention, the specific covert communication process of both sides is as follows:
[0033] ① Covert communication sender
[0034] Step 1: Under the Windows7 operating system, use Winpcap and Visual C++6.0 software to build an IPD-based covert channel communication platform to capture normal network communication data flow. In this embodiment, the P2P network application currently occupying the main data traffic——YY voice is selected as the carrier application of the covert channel. In different embodiments, other suitable carriers can be selected according to specific situations.
[0035] Step 2: Extract the normal inter-packet delay IPD through the time stamp, and divide the sequence into multiple segments whose length l is 500, record one of the IPD segments as ΔT={Δt 1 ,Δt 2 ,···,Δt 500}. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com