Network user behavior risk assessment method based on AHP
A network user and risk assessment technology, applied in the direction of electrical components, transmission systems, etc., can solve problems such as inestimable harm, and achieve the effect of solving general and uncertain problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
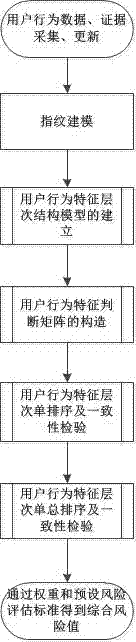
[0060] Such as figure 1 , the AHP-based network user behavior risk assessment method is to decompose the overall user behavior risk layer by layer according to the actual application requirements and functional characteristics, decompose the comprehensive and general user behavior risk into several behavior risk attributes, and then divide the behavior risk attributes Continue to refine it into behavioral risk evidence that can be directly measured by software and hardware, and obtain a comprehensive risk value.
[0061] AHP-based network user behavior risk assessment method, which includes the following steps:
[0062] S1: Preprocessing of network user behavior data;
[0063] S2: fingerprint modeling;
[0064] S3: Obtain the comprehensive risk value.
[0065] The preprocessing of network user behavior data includes network user behavior data collection, label classification and analysis;
[0066] The network user behavior data collection objects include a user information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com