A method for obtaining evidence, server and firewall
A server and cloud server technology, applied in the field of communication security, can solve problems such as low processing efficiency and inability to respond to all users efficiently, and achieve the effect of improving accuracy and improving the efficiency of forensics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
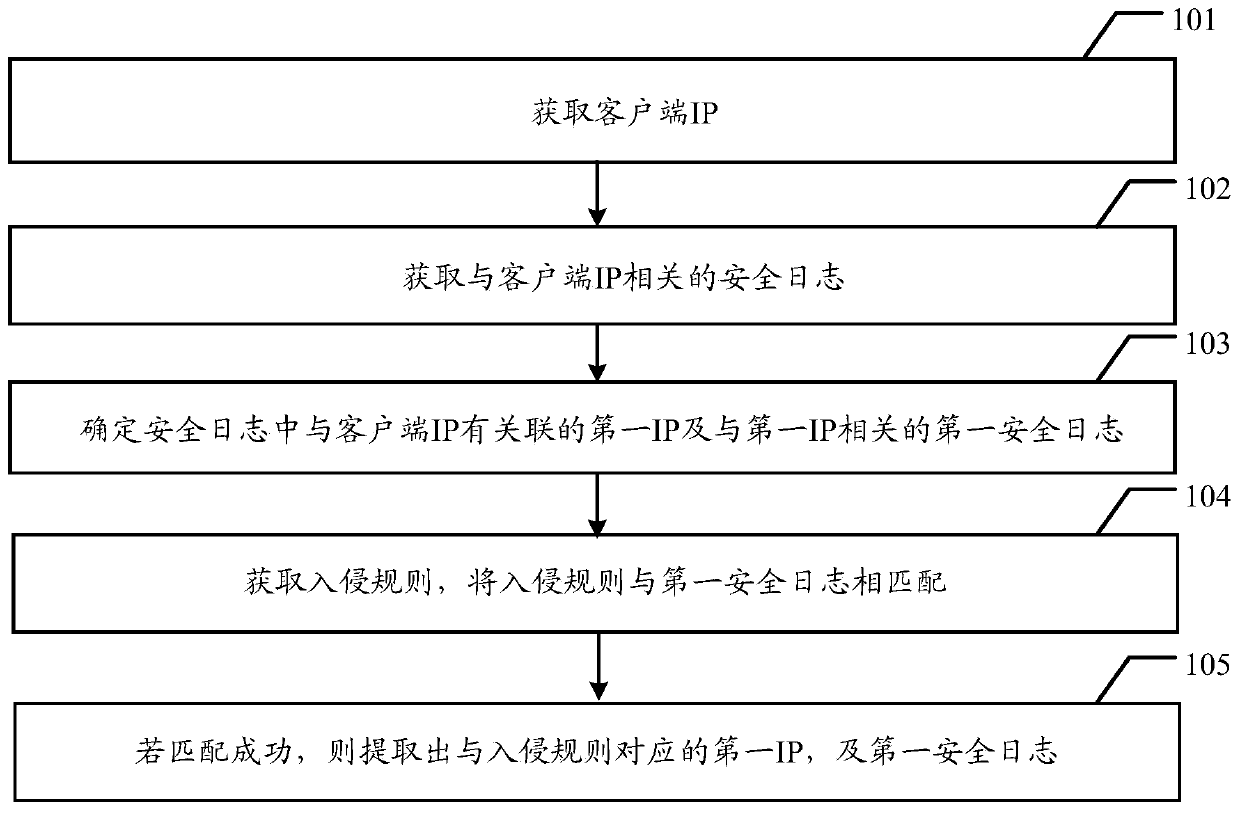
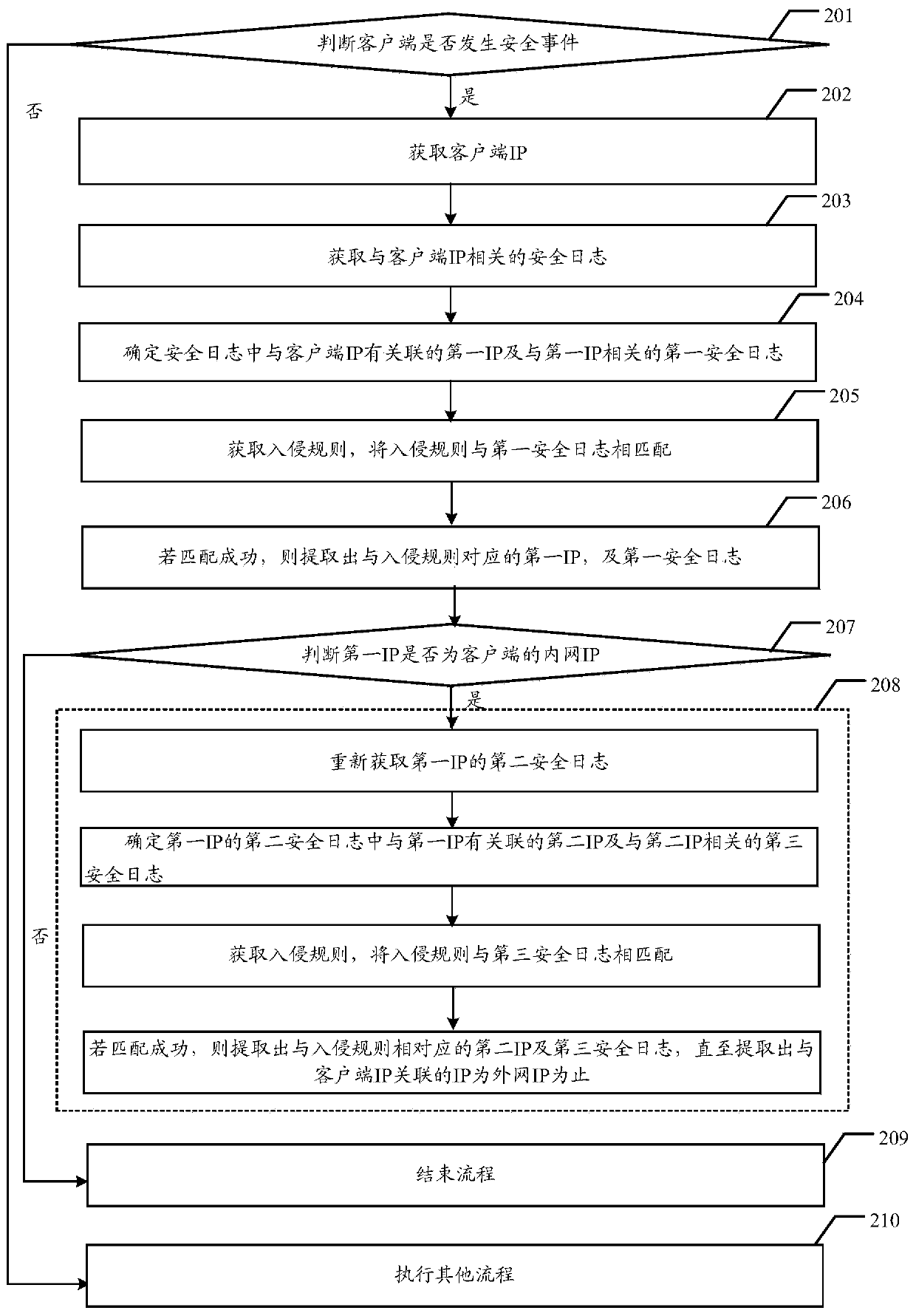
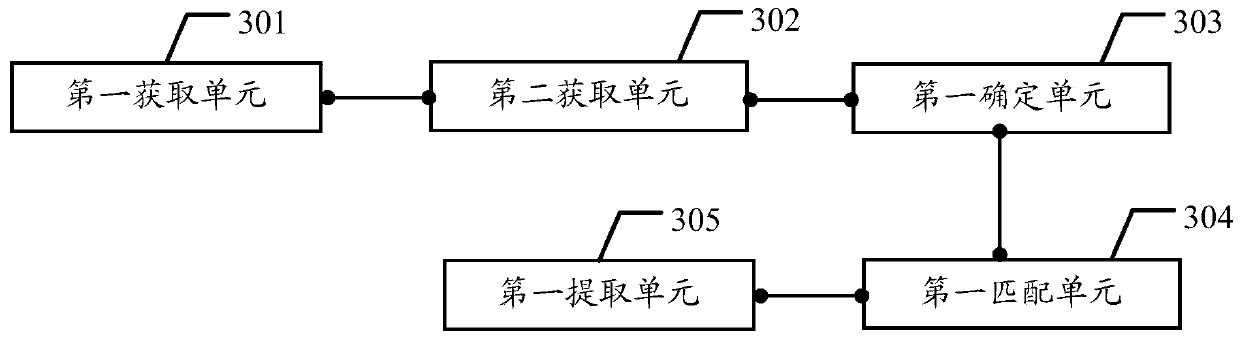
[0065] The embodiment of the present invention provides a method for obtaining evidence, a server, and a firewall, which are used to automatically read the client IP and the security log related to the client IP according to the security log association method, and use the security log to determine the security log related to the client IP. The associated first IP and the first security log associated with the first IP are then used to extract the first IP and the first security log corresponding to the intrusion rule by using the intrusion rule matching method, so as to achieve the purpose of automatic forensics.
[0066] Because the present invention can automatically read the security log through the server, and use the intrusion rules to automatically compare the first IP and the first security log related to the first IP, without manual comparison, thereby improving the accuracy of evidence collection and the efficiency of evidence collection.
[0067] With the rapid deve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com