Authorizing method of form field value operating authorization
一种操作权限、字段值的技术,应用在数字数据认证、数字数据保护、电数字数据处理等方向,能够解决增加授权、无法显示操作者及操作时间、授权等问题,达到提高精细度、授权操作简单高效、提高授权效率的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] [Embodiment 1] In this embodiment, the fields to be controlled by operation authority are set first, and then the corresponding operation authority is set.
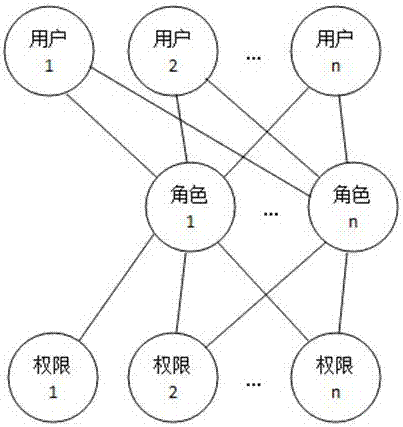
[0066] The form field value operation permission authorization method includes a form field value operation permission authorization step and a step of selecting an authorized person, and the order of the form field value operation permission authorization step and the step of selecting the authorized person is not in any order;
[0067] The operation permission authorization step of the form field value includes the following steps:
[0068] S1: Select a form to be authorized, and display the fields in the form that need to be controlled for operation permissions;
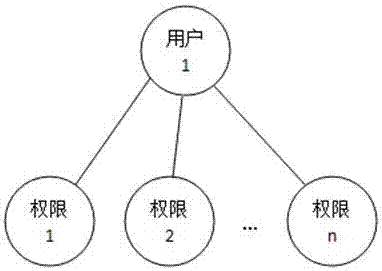
[0069] S2: Authorize the operation authority of the field value of each field respectively, and the operation authority includes one or both of viewing and modification.
[0070] After the setting is completed, the authorized person's permission to vi...
Embodiment 2
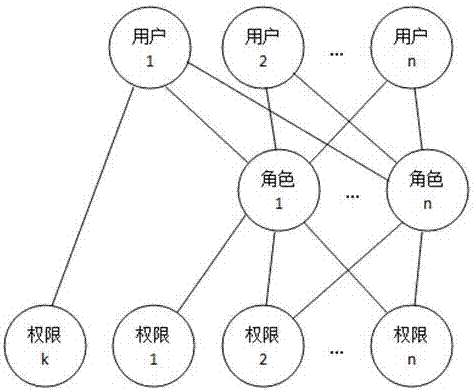
[0091] [Embodiment 2] In this embodiment, one or more can be selected when selecting the authorized person, and only one can be selected when selecting the form to be authorized. When there is one and only one authorized person is selected, and the form to be authorized is selected, the operator and operation time that recently authorized the field value of the form to the authorized person are displayed.
[0092] Such as Figure 5 As shown, when an authorized person is selected and the authorization form is selected, the operator and operation time of the recent form field value operation authority authorization are displayed, and the current field value operation authority status of the authorized person on the form is also displayed , modify and save it to get its new field value operation permission.
[0093] Such as Figure 6 As shown, when multiple authorized persons are selected and the authorization form is selected, the authorization operator and operation time of t...
Embodiment 3
[0098] [Example 3] In this example, for field values that do not have viewing authority, the display methods include:
[0099] (1) Display the field corresponding to the field value, but hide the field value with a hidden character, such as Figure 8 As shown, the fields "Phone" and "Contact" are displayed, but the contents of the fields are hidden with *;
[0100] (2) Neither the field value nor the field corresponding to the field value will be displayed.
[0101] Whether there is modification permission or not is also displayed differently. For example, display the field value without modification permission as gray shading, such as Figure 8 shown.
[0102] Specifically, a form includes basic fields and detailed fields, and the detailed fields are column names on the detailed list in the form. For example, in the order form, the basic fields include the order number, customer name, customer address, phone number, contact person, customer industry, etc.; the detailed ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com