A method for realizing LTE-WLAN converged network access authentication protocol
An access authentication and converged network technology, which is applied in the field of network convergence and realizes the LTE-WLAN converged network access authentication protocol, and can solve the problems of failing to implement mutual authentication between UE and home network, being vulnerable to man-in-the-middle attacks, and being vulnerable to attacks, etc. Achieve the effect of protecting user identity, reducing bandwidth consumption, and ensuring correctness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
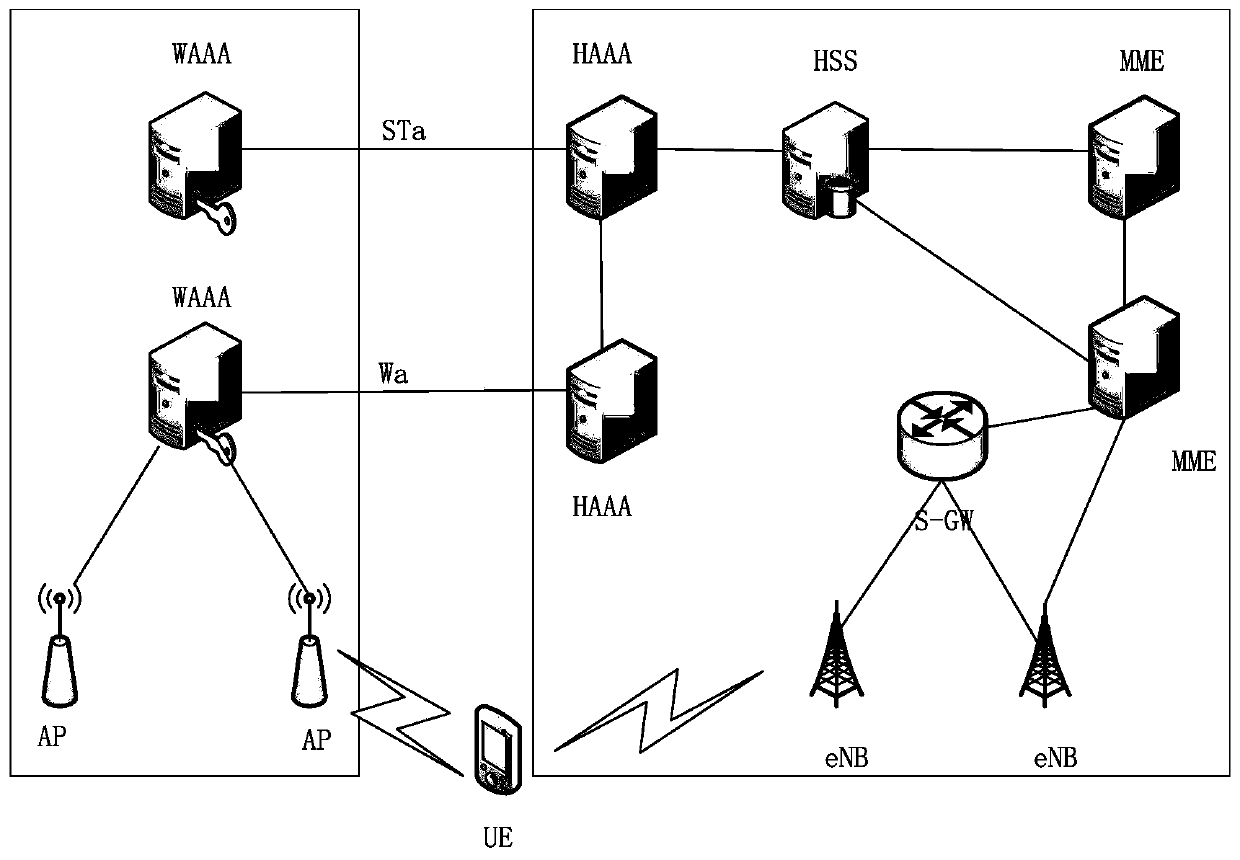
[0018] With the rapid development of the mobile Internet and the explosive growth of mobile data traffic, the integration of LTE and WLAN networks has become a research hotspot at this stage. At this stage, when users switch between WLAN and LTE networks, services will be interrupted, and WLAN access After the integration of the LTE core network and the LTE network, users will realize seamless switching between networks without service interruption, and WLAN can also play a role in offloading traffic. In the converged network, user access authentication is the premise. Existing authentication needs to continuously upgrade equipment, the cost is too high, and a large amount of computing power is required; some EAP-AKA protocols are also vulnerable to man-in-the-middle attacks, and UE Mutual authentication with the home network is only a one-way authentication, which is vulnerable to attacks. Aiming at the present technical situation, the present invention proposes a more effici...
Embodiment 2
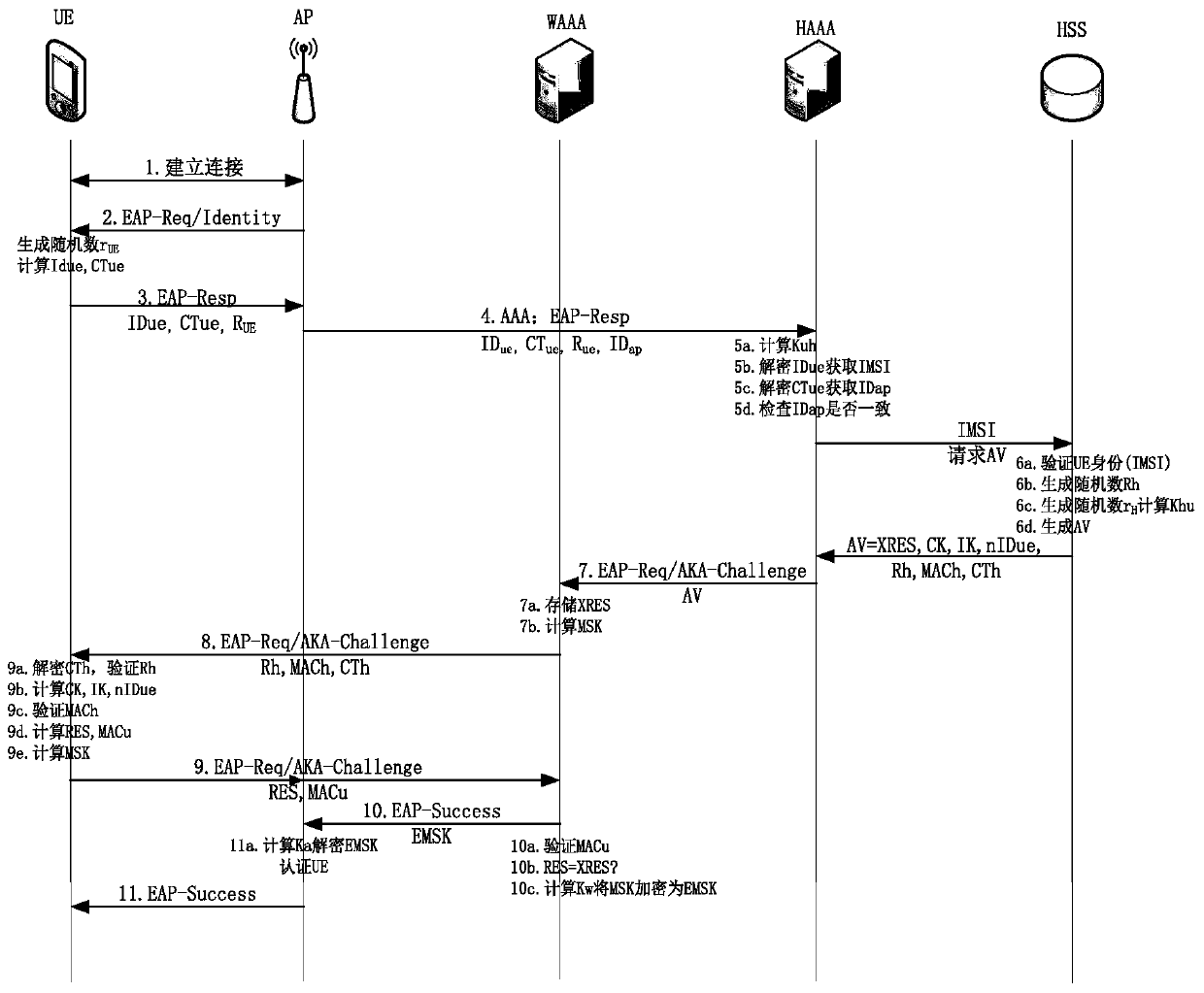
[0025] The method for realizing the LTE-WLAN converged network access authentication protocol is the same as in embodiment 1, wherein in the identity authentication phase of the UE, the identity authentication process includes the following steps:
[0026] (2a) The user UE establishes a connection with the access point AP;
[0027] (2b) The AP sends an EAP-Identity Request message to the UE;
[0028] (2c) UE generates random number r UE Used to generate a temporary key K UH , used to encrypt the IMSI, the encrypted result is IDue, and the UE generates a cryptographic token (cryptographic token) CTue to encrypt the identity of the connected AP, and the UE sends the EAP data packet {IDue, CTue, R UE} to AP;
[0029] (2d) The AP sends the received EAP packet {IDue, CTue, R UE} and own IDap are sent to HAAA via WAAA;
[0030] (2e) HAAA calculates K UH = d H *R UE , with K UH Decrypt the IMSI from the IDue, and decrypt the IDap from the CTue at the same time, verify wh...
Embodiment 3
[0039] The method for realizing the LTE-WLAN converged network access authentication protocol is the same as in embodiment 1-2, and IDue in step (2c) is the temporary ID of the current UE, which is k UH The result of encrypting the IMSI is calculated as follows:
[0040] R UE = r UE * U E R UE '=r UE * U H
[0041] k UH =dE*R UE '
[0042] IDue={IMSI}_k UH
[0043] where (U E , d E) is the shared key pair of UE and HSS, r UE is a random number generated by the user UE, which is used to randomly generate the symmetric key R UE and R UE ’, for key k UH generation of k UH It is the encryption key used to encrypt the IMSI.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com