Suspicious domain name detection method and system
A domain name detection and domain name technology, applied in the transmission system, electrical components, etc., can solve the problems of high computer resource consumption, difficulty in automatically updating suspicious domain names, intercepting suspicious domain names, inability to audit and monitor DNS messages, etc., and achieve the effect of double verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to enable those skilled in the art to better understand the technical solution of the present invention, the suspicious domain name detection method and system provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
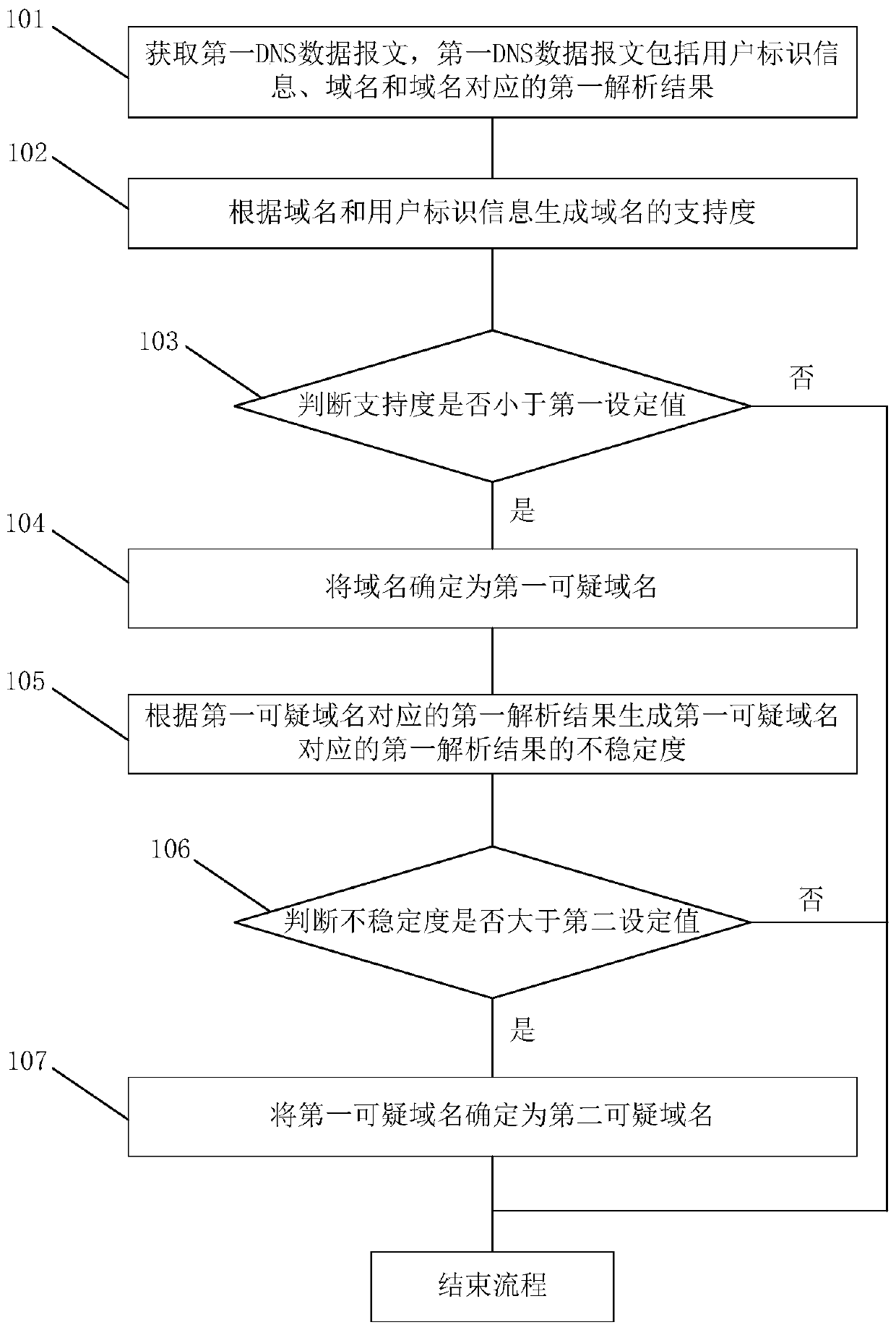
[0048] figure 1 It is a flowchart of a suspicious domain name detection method provided by Embodiment 1 of the present invention. As shown in the figure, the suspicious domain name detection method includes:
[0049] Step 101. Obtain a first DNS data packet, where the first DNS data packet includes user identification information, a domain name, and a first resolution result corresponding to the domain name.
[0050] Step 102, generating the support degree of the domain name according to the domain name and user identification information.
[0051] Step 103 , judging whether the support degree is less than the first set value, if yes, execute step 104 , if not, end the process.
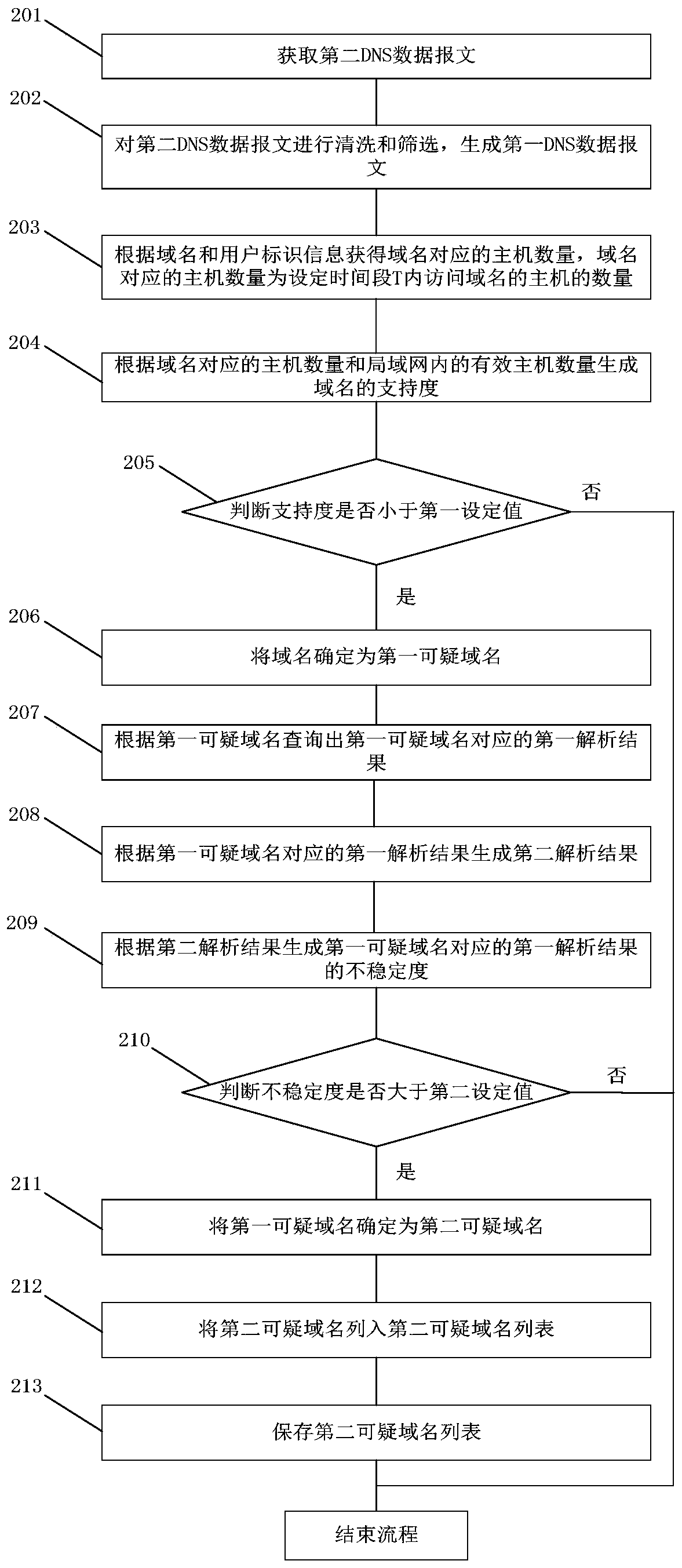
[0052] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com