Method for implementing core role-based access control based on attribute-based encryption
A technology of role access control and attribute-based encryption, applied in the field of information security, can solve problems such as low efficiency and inability to implement fine-grained RPA strategies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
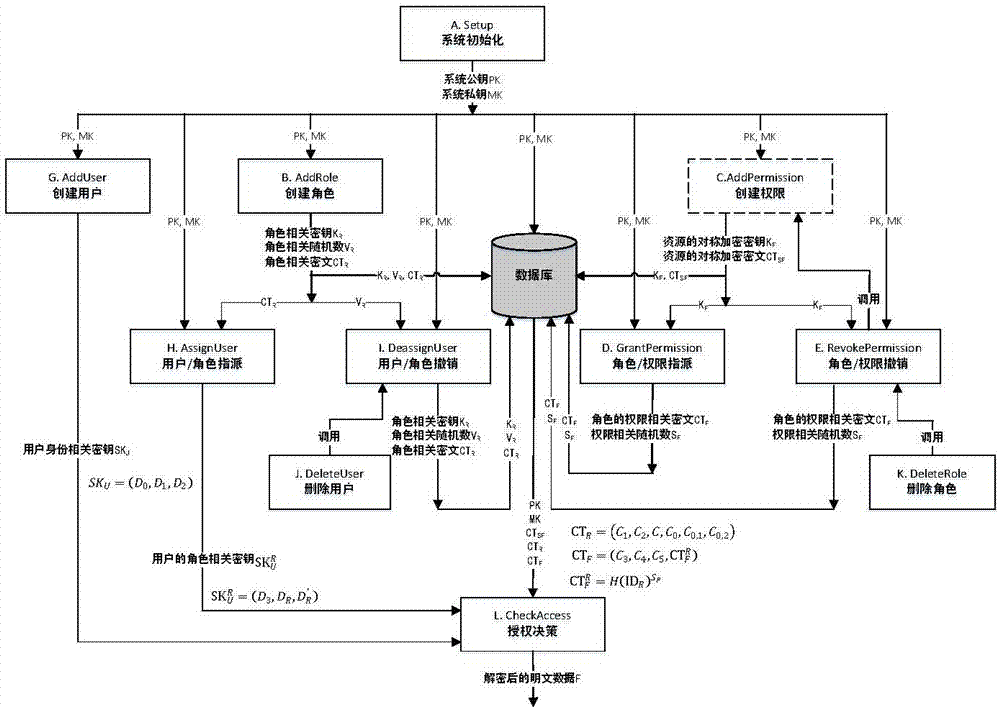
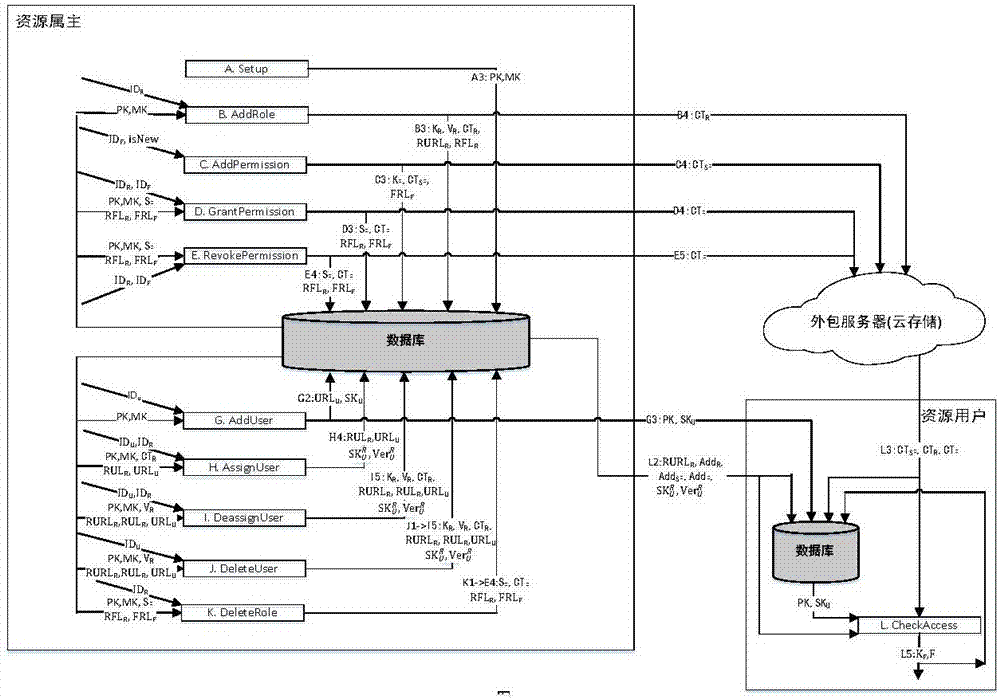
[0086] Embodiment 1, will figure 1 The shown method of using attribute-based encryption to implement the core role access control model is used to implement the core RBAC access control in the outsourcing service environment (cloud storage), and the structure of the formed system is as follows figure 2 As shown, the system includes three types of entities: resource owner, resource user, and outsourced server (cloud storage server). The outsourced server downloads the relevant ciphertext, obtains the key information from the resource owner, and finally decrypts to obtain the plaintext of the resource.
[0087] (1) Resource owner, responsible for system initialization (A——Setup), creation of roles (B——AddRole), creation of permissions (C——AddPermission), role / permission assignment (D——GrantPermission), role / authorization revocation (E——RevokePermission), create user (G——AddUser), user / role assignment (H——AssignUser), user / role revocation (I——DeassignUser), delete user (J——Dele...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com