Data safety ferrying system and matched method thereof
A technology of data security and ferry system, applied in digital data protection, data exchange through path configuration, optical fiber transmission, etc. free embarrassing effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
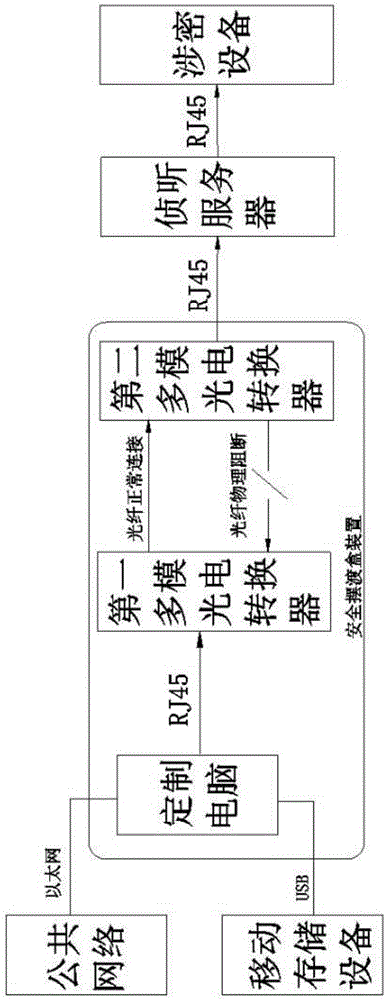
[0030] like figure 1 A data security ferry system shown includes a security ferry box device, an interception server, and secret-related equipment. The security ferry box device is provided with an Ethernet interface for connecting to a public network, and the secure ferry box device is also provided with an Ethernet interface for connecting to a public network. The USB interface of the mobile storage device, the output terminal of the safety ferry box device is connected to the interception server, and the interception server is connected to the confidential equipment;
[0031] The safety ferry box device includes a customized computer, a first multi-mode photoelectric converter and a second multi-mode photoelectric converter. The mode photoelectric converter is connected through optical fiber, the optical fiber that the first multimode photoelectric converter sends data to the second multimode photoelectric converter is connected normally, and the optical fiber that the seco...
Embodiment 2
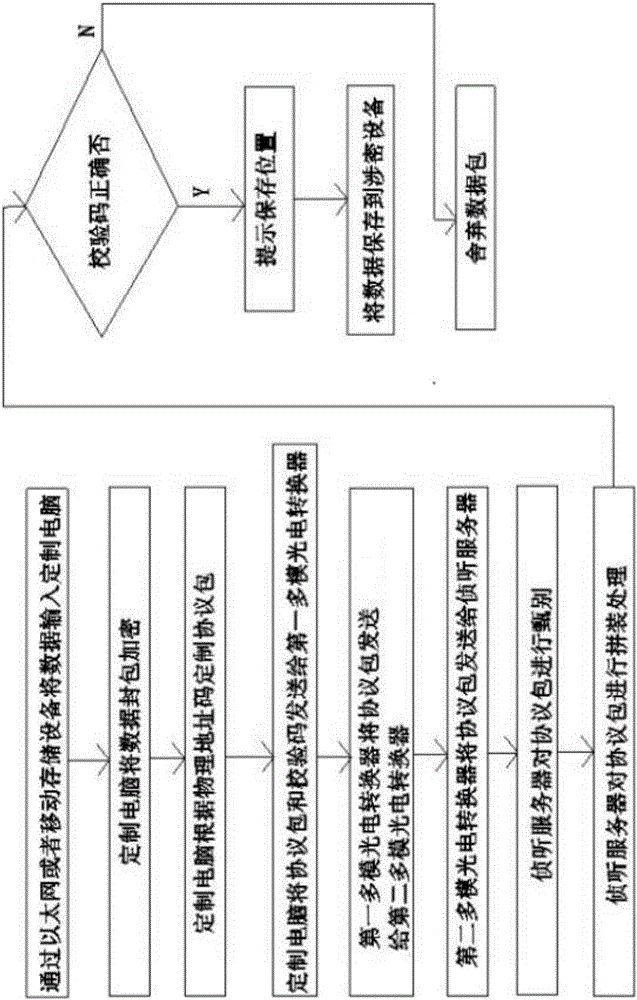
[0035] like figure 2 As shown, the data security ferry method supporting a data security ferry system is realized by a data security ferry system described in Embodiment 1, including the following steps:
[0036] Step 1: The user enters the data into the customized computer through Ethernet or mobile storage device;
[0037] Step 2: The customized computer automatically encrypts the data packet to generate a data packet;
[0038] Step 3: Customize the computer to customize the data packet into a protocol packet with reference to the physical address code, and generate a check code;
[0039] Step 4: The customized computer sends the protocol packet and check code to the first multimode photoelectric converter;
[0040] Step 5: the first multimode photoelectric converter sends the protocol packet to the second multimode photoelectric converter through an optical fiber;
[0041] Step 6: the second multimode photoelectric converter sends the protocol packet to the listening se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com