A way to implement quantum-safe ipsecvpn
A quantum and secure technology, applied in key distribution, can solve the problem of not considering the quantum security of data encryption, not considering quantum security, etc., and achieve the effect of good compatibility and application flexibility, good application prospects, and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
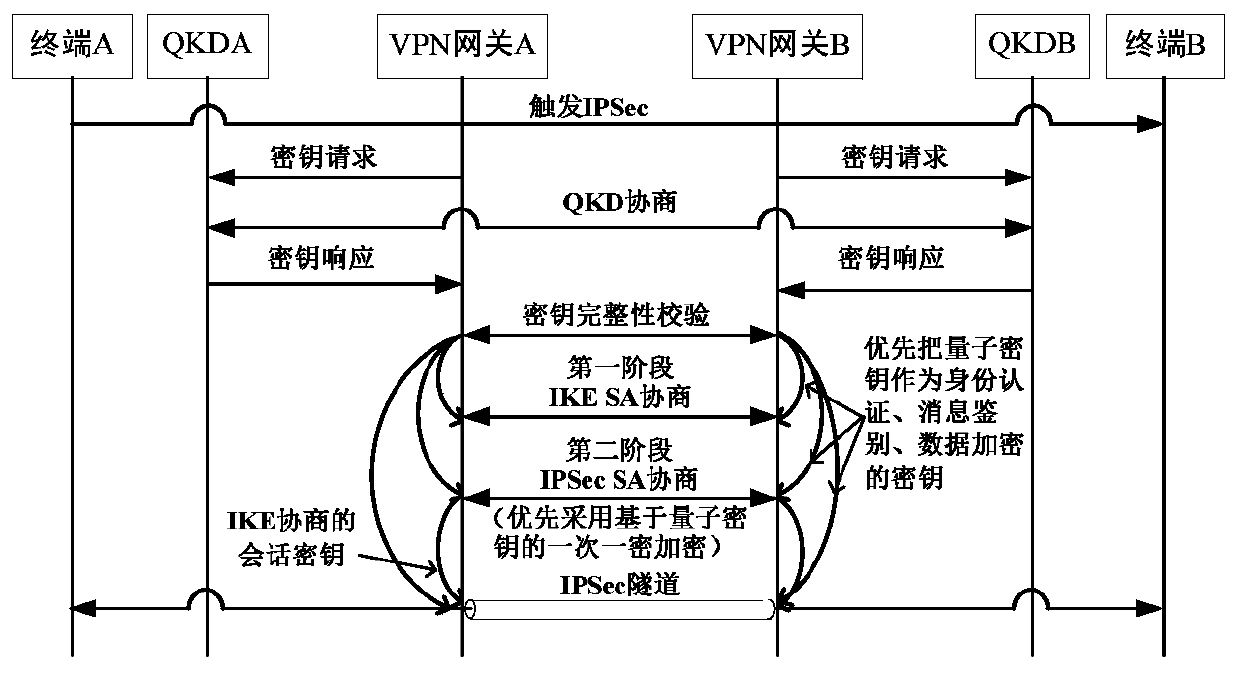
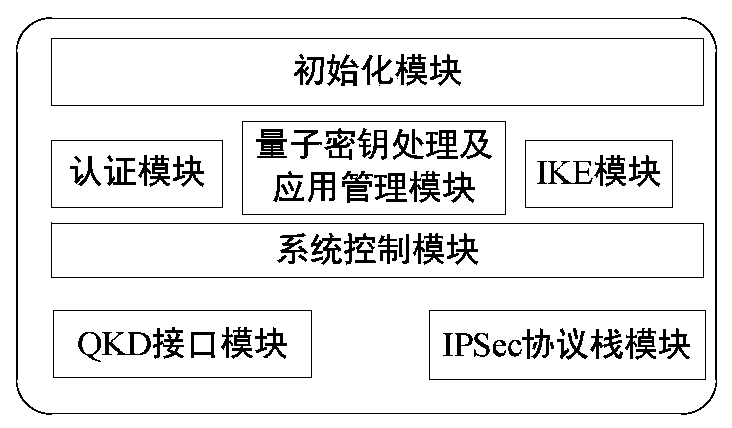
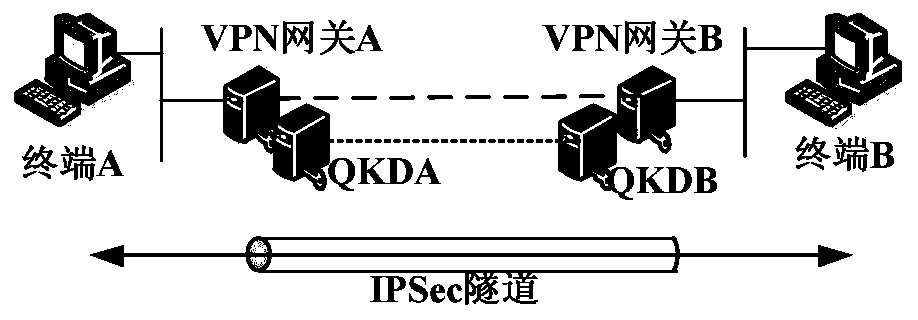
[0030] A method of implementing quantum-safe IPSec VPN, such as Figure 1 to Figure 3 shown, including the following:
[0031] VPN gateway A and VPN gateway B are respectively configured with QKD terminals or quantum key security access interfaces.
[0032]Step 1: Terminal A sends the data flow that triggers the IKE process to terminal B; VPN gateway A and VPN gateway B send instructions to negotiate quantum keys to QKDA and QKDB respectively; QKDA and QKDB perform identity authentication based on the pre-shared key, and then perform Quantum key negotiation: According to the key parameter requirements of the possible encryption algorithm, the negotiated quantum key is divided and arranged, and used as the pre-shared key and HMAC algorithm between VPN gateway A and VPN gateway B respectively shared secret key and shared session key;
[0033] Step 2: VPN gateway A and VPN gateway B negotiate an IKE phase 1 session. VPN gateway A and VPN gateway B perform identity authenticatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com