Wireless radio frequency equipment, authentication server and authentication method
An authentication server, radio frequency technology, applied in the field of authentication server and authentication, radio frequency equipment, can solve the problems of inability to meet the requirements of user security, poor authentication security, etc., to prevent counterfeiting of radio frequency equipment, improve the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
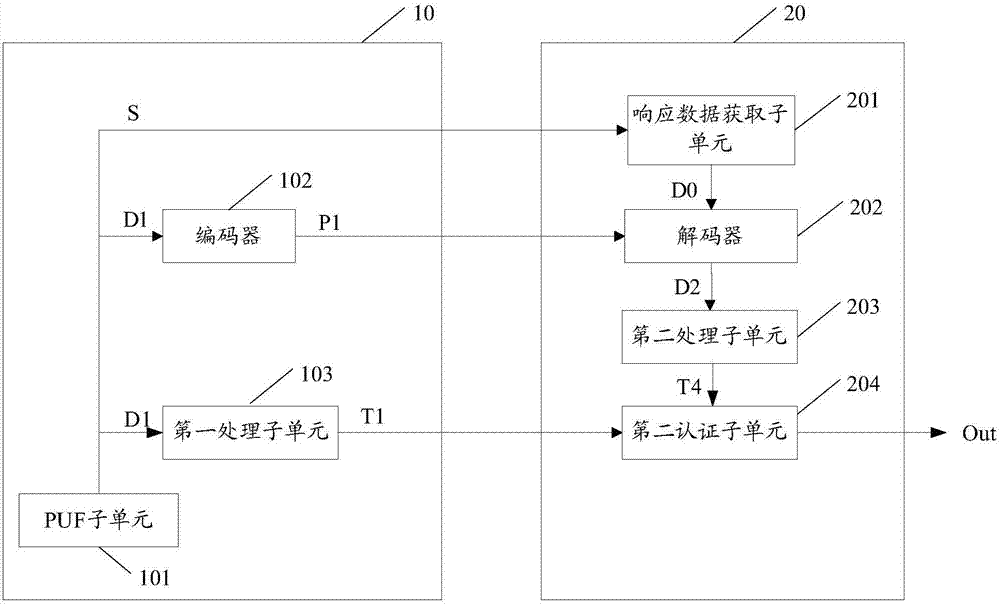
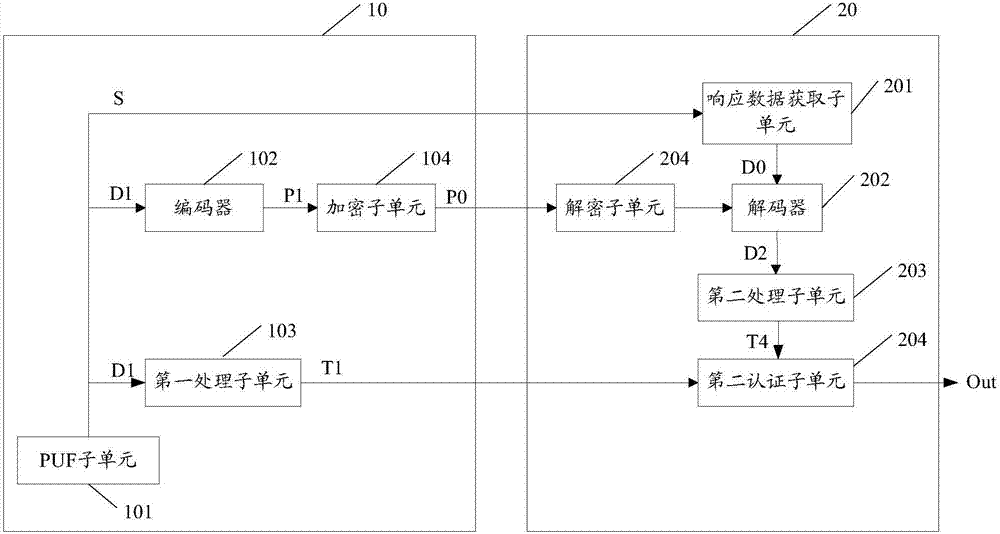
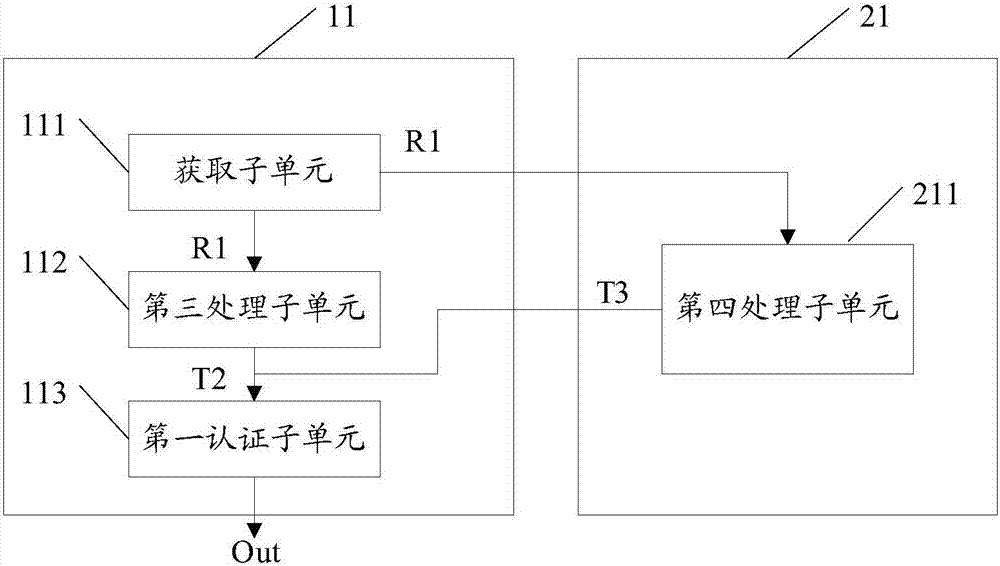
[0045] In a wireless radio frequency device equipped with a PUF unit, the response exists when the PUF unit is powered on, and disappears when the power is turned off. Therefore, using the PUF unit for authentication can prevent physical attacks such as probes and electronic scanning. In addition, since each PUF unit will inevitably produce many individual differences during its manufacturing process, the physical difference comes from uncontrollable factors in the manufacturing process, so no matter how the PUF unit is designed, the difference between the PUF unit and the PUF unit There will always be some slight differences between them. Even if the design, packaging, and manufacturing processes are completely consistent, it is impossible to replicate two identical PUF units. Therefore, the PUF unit is naturally unique and unclonable, and can resist Attacks such as replay attacks, side channel attacks, and malicious attacks.
[0046] At present, in the process of mutual auth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com