PPTP VPN password verification method and computer readable storage medium
A password verification and password technology, which is applied in the field of encryption, can solve the problem of increasing the geometric progression of the traversal time, and achieve the effect of reducing the traversal time and improving the verification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
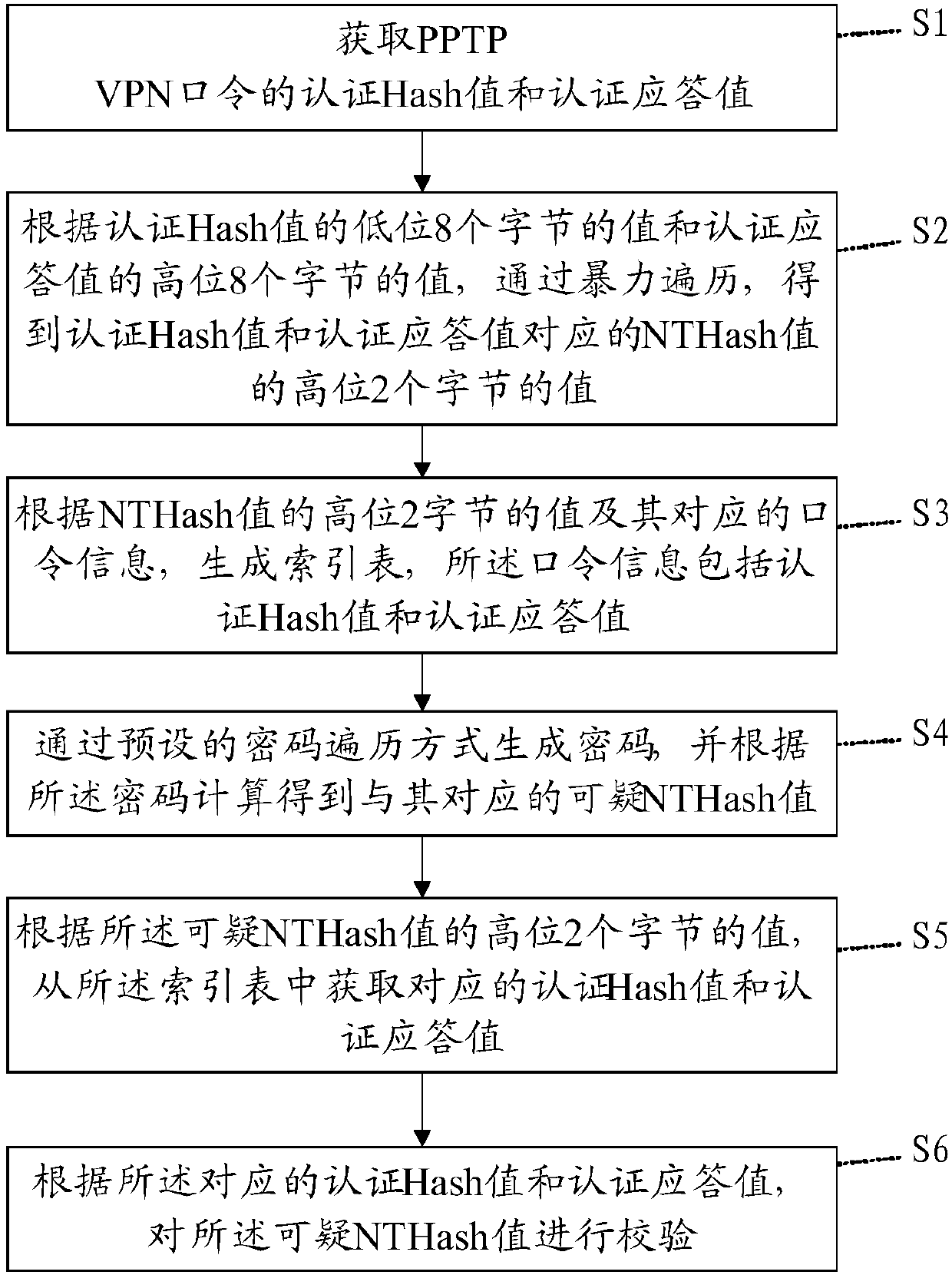
[0082] Please refer to figure 1 , Embodiment one of the present invention is: a kind of PPTP VPN password verification method, comprises the steps:
[0083] S1: Obtain the authentication Hash value and the authentication response value of the PPTP VPN password; from the plaintext information of the PPTP VPN password communication message, the authentication response value (ChallengeResponse) of 24 bytes can be obtained directly and the authentication Hash value (ChallengeResponse) of 20 bytes can be indirectly calculated ( ChallengeHash).
[0084] S2: According to the value of the lower 8 bytes of the authentication Hash value and the value of the upper 8 bytes of the authentication response value, through brute force traversal, obtain the upper 2 characters of the NTHash value corresponding to the authentication Hash value and the authentication response value The value of the section; since the high-order 2 bytes of the NTHash value are used as an encryption key after a spe...
Embodiment 2
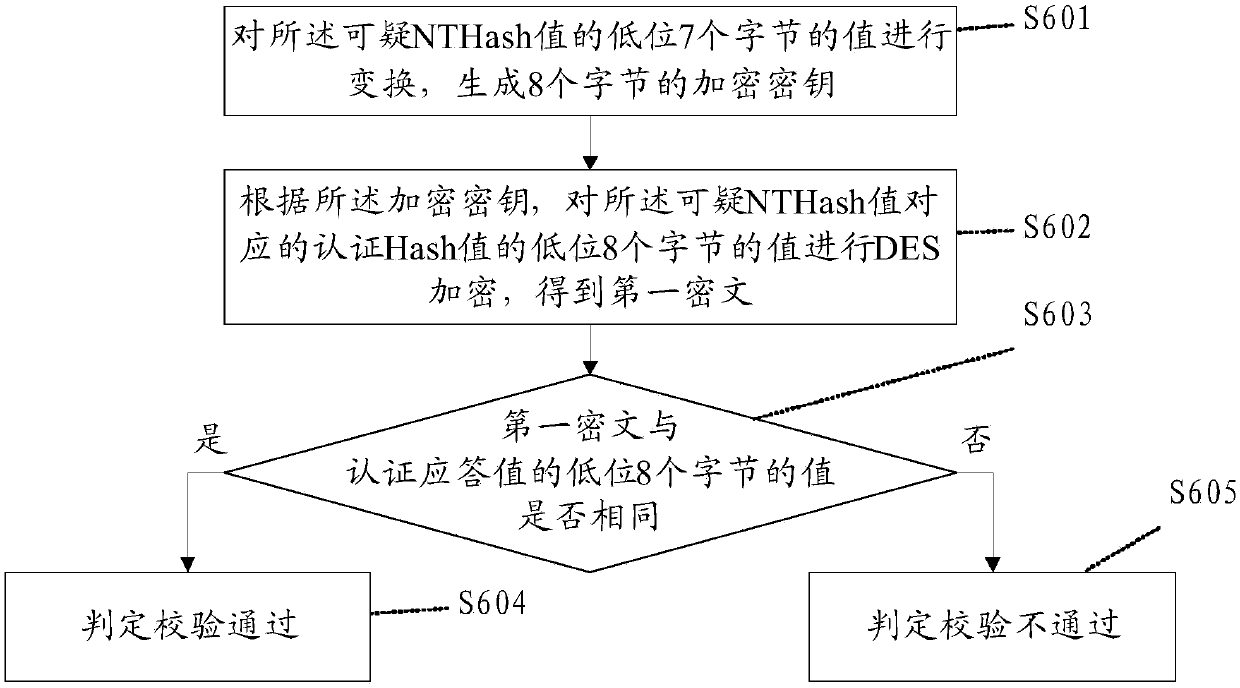
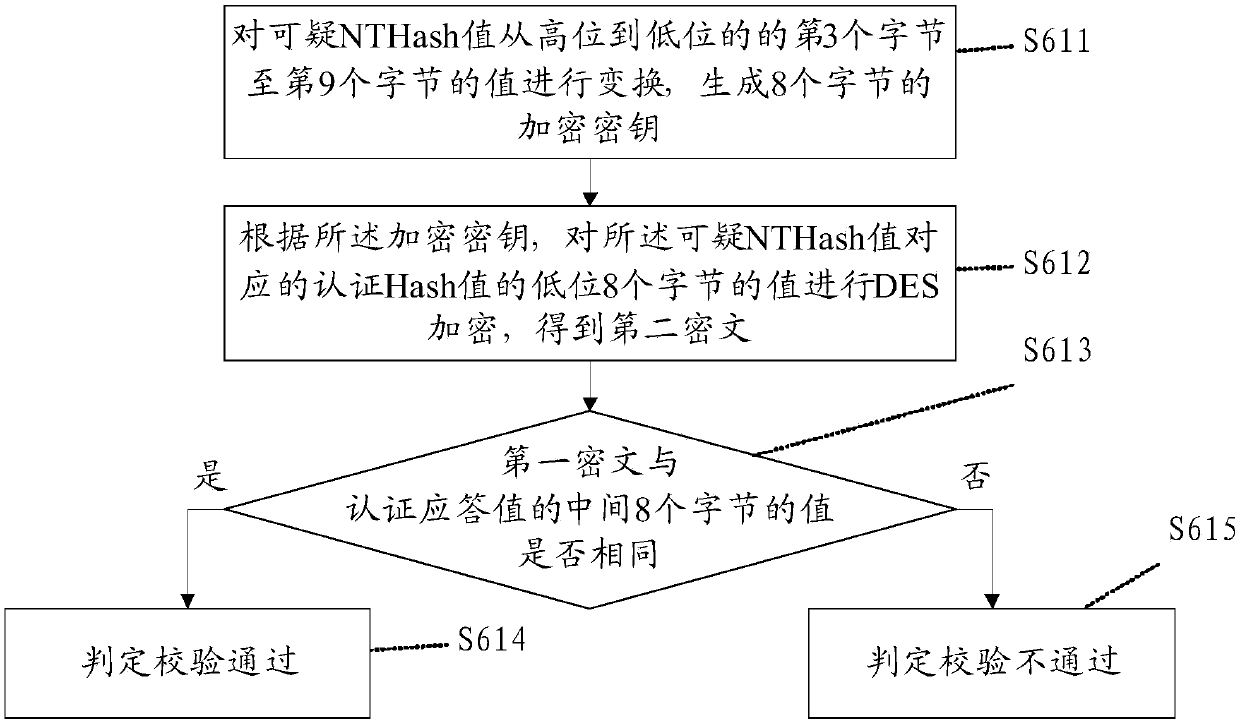
[0110] This embodiment is a further extension of steps S3, S5 and S6 in the first embodiment.
[0111] Such as Figure 4 As shown, the step S3 includes the following steps:
[0112] S301: Construct a first index table, a second index table, and a third index table, where the index addresses in the first index table and the second index table are first index addresses, and the values of the first index addresses are respectively 0 -65535, the index address in the third index table is the second index address.
[0113] S302: Store the password information in the third index table, and obtain the second index address corresponding to the password information; that is, store the password information in the space of the second index address in the third index table, and each second index address Only one set of password information is stored in the space.
[0114] S303: In the first index table, set the flag bit stored in the first index address that matches the value of the u...
Embodiment 3
[0145] This embodiment is a computer-readable storage medium corresponding to the above-mentioned embodiments, on which a computer program is stored, and when the program is executed by a processor, the following steps are implemented:
[0146] Obtain the authentication Hash value and authentication response value of the PPTP VPN password;
[0147] According to the value of the lower 8 bytes of the authentication Hash value and the value of the upper 8 bytes of the authentication response value, through brute force traversal, obtain the upper 2 bytes of the NTHash value corresponding to the authentication Hash value and the authentication response value value;
[0148] According to the value of the upper 2 bytes of the NTHash value and its corresponding password information, an index table is generated, and the password information includes an authentication Hash value and an authentication response value;
[0149] Generate a password through the preset password traversal met...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com