File encryption method, terminal and computer readable storage medium
A file encryption and terminal technology, applied in computer security devices, calculations, instruments, etc., can solve problems affecting user experience, threatening the privacy and confidentiality of files to be encrypted, and prolonging the display time of files to be encrypted, so as to avoid being leaked The possibility of saving users' time and ensuring privacy and confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
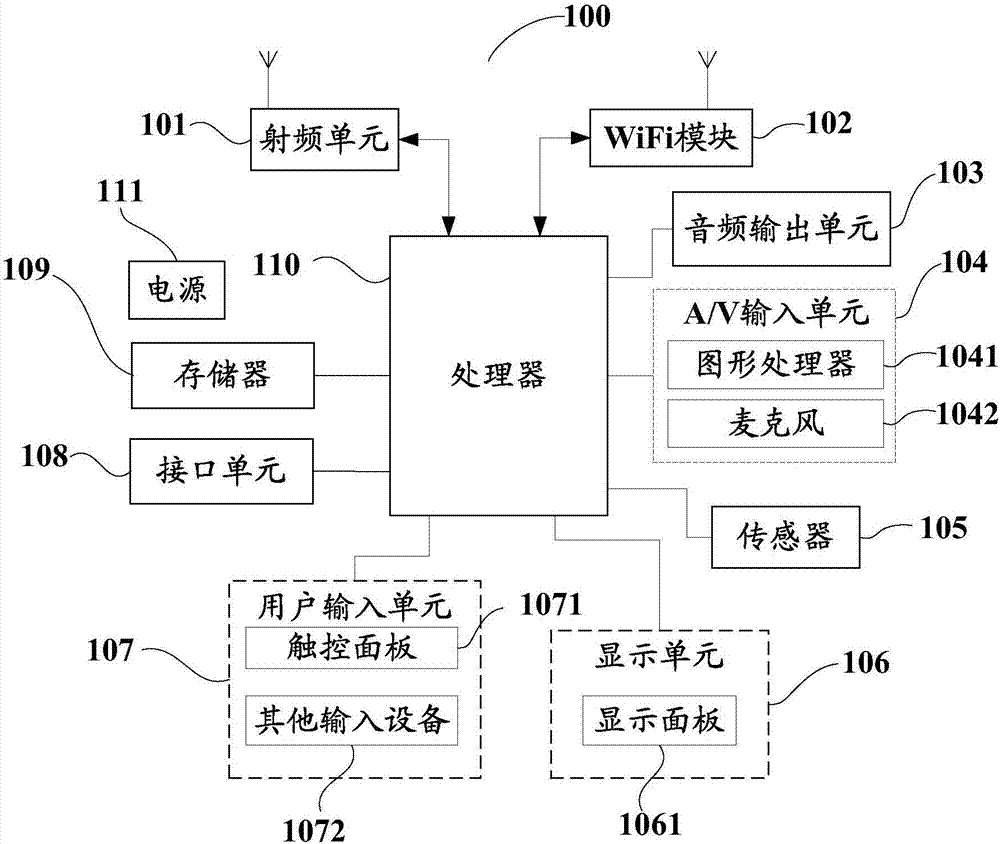
[0066] In order to simplify the file encryption process, improve user experience, and improve the privacy and confidentiality of files during the file encryption process, this embodiment provides a file encryption method. see figure 2 , figure 2 The basic flowchart of the file encryption method provided in this embodiment includes:
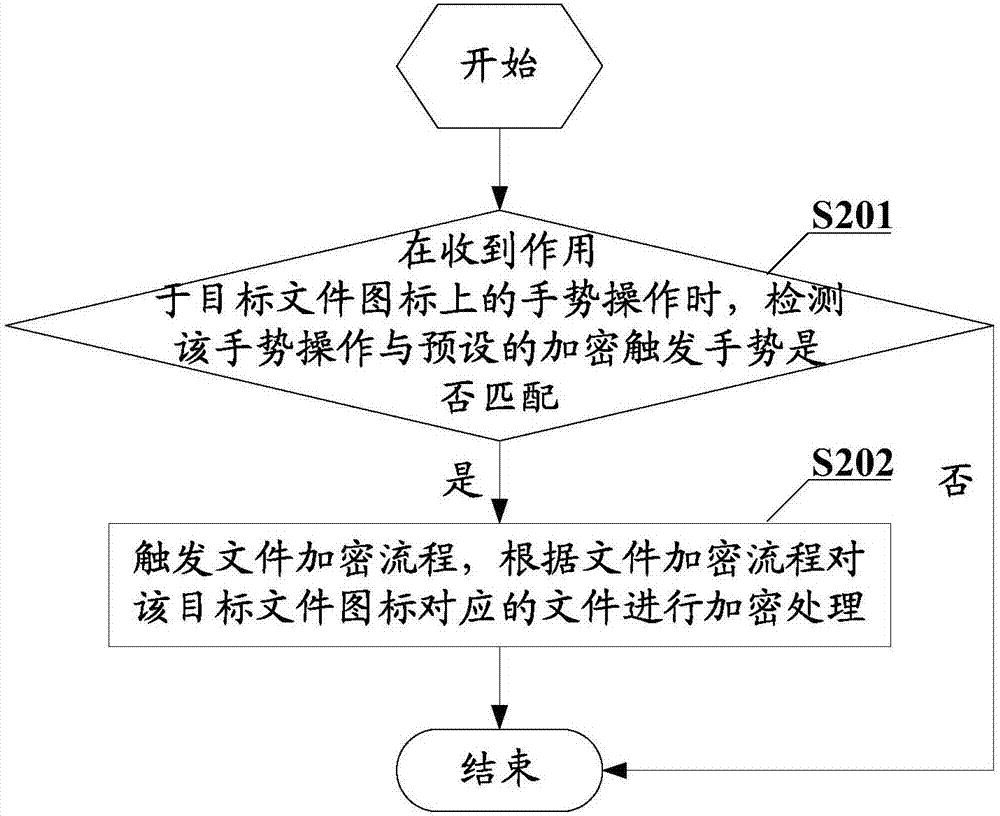
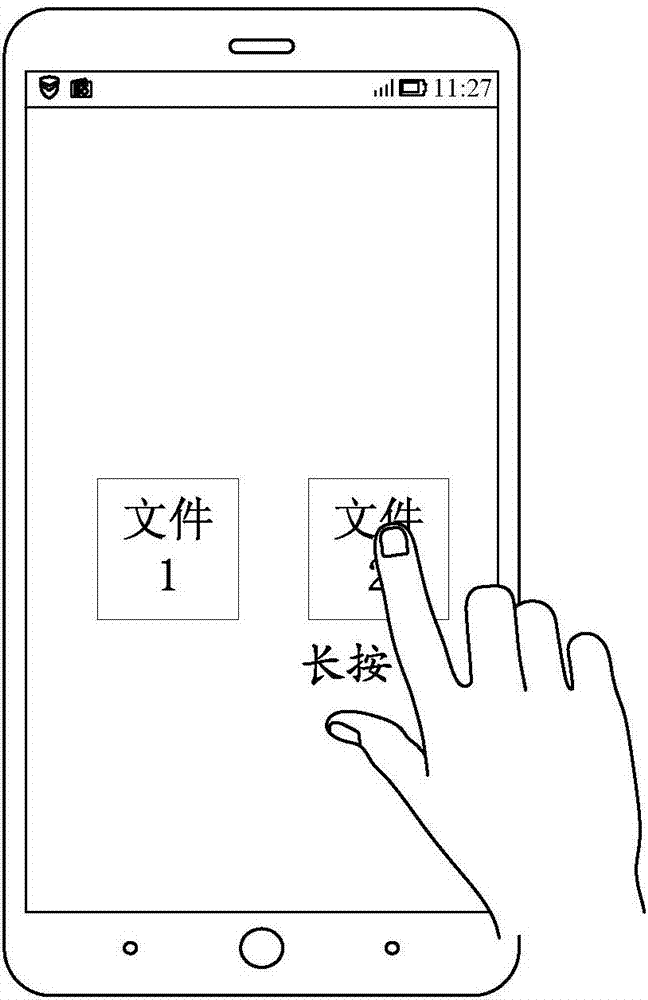
[0067] S201: When a gesture operation acting on the target file icon is received, check whether the gesture operation matches the preset encryption trigger gesture; if yes, go to step S202; otherwise, end.
[0068] In this embodiment, for the terminal, the collection of gesture operations can be realized through the touch screen installed on the terminal. After the touch screen collects the user's gesture operation track on the touch screen, the The collected gesture operation information is fed back to the processor, and the processor compares it with various preset gesture operations in the terminal, so as to obtain instruction information c...
no. 2 example
[0099]This embodiment is based on the first embodiment, taking a case where there is a user identity verification process, and the file encryption process includes providing and displaying an encryption confirmation interface as an example to further illustrate the present invention.
[0100] The default encryption trigger gesture is set as the icon long press gesture, and the terminal adopts screen fingerprint recognition technology.
[0101] see Figure 12 , Figure 12 It is a detailed flow chart of a file encryption method provided in the second embodiment of the present invention. The file encryption method includes:
[0102] S1201: Obtain the fingerprint of the finger performing the gesture operation while receiving the long press operation acting on the target file icon;
[0103] S1202: Detect whether the fingerprint is a registered fingerprint; if so, go to step S1203; otherwise, exit the file encryption process.
[0104] It should be understood that when the termina...
no. 3 example
[0111] This embodiment also provides a terminal, see Figure 13 As shown, it includes a processor 131, a memory 132 and a communication bus 133, wherein:
[0112] The communication bus 133 is used to realize connection and communication between the processor 131 and the memory 132;
[0113] The processor 131 is used to execute one or more programs stored in the memory 132, so as to realize the following steps:
[0114] When receiving a gesture operation acting on the icon of the target file, detect whether the gesture operation matches the preset encryption trigger gesture; if they match, trigger the file encryption process, and perform file encryption on the file corresponding to the target file icon according to the file encryption process Encryption processing.
[0115] In this embodiment, for the terminal, the collection of gesture operations can be realized through the touch screen installed on the terminal. After the touch screen collects the user's gesture operation t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com