Hardware-Trojan-horse detection method based on side-channel analysis
A technology for hardware Trojan detection and side channel analysis, applied in the protection of internal/peripheral computer components, instrument, platform integrity maintenance, etc., can solve problems such as low efficiency and poor reliability, and achieve the effect of improving detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be described in detail below in conjunction with the implementations shown in the drawings, but it should be noted that these implementations are not limitations of the present invention, and those of ordinary skill in the art based on the functions, methods, or structural changes made by these implementations Equivalent transformations or substitutions all fall within the protection scope of the present invention.
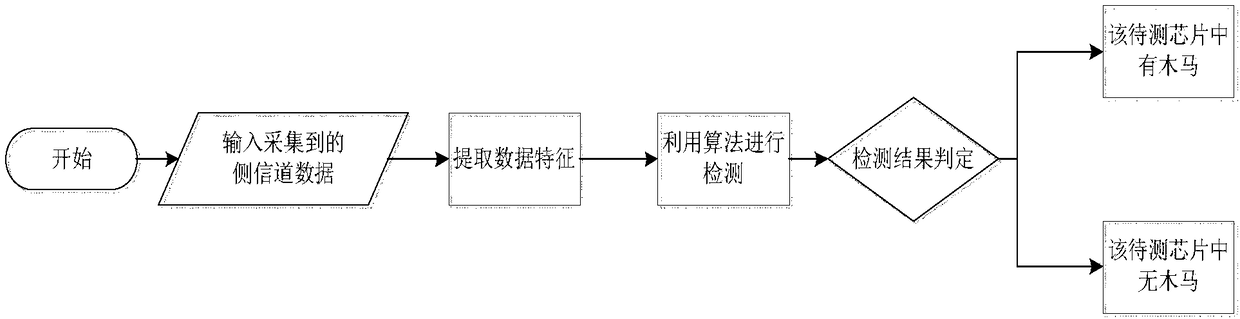
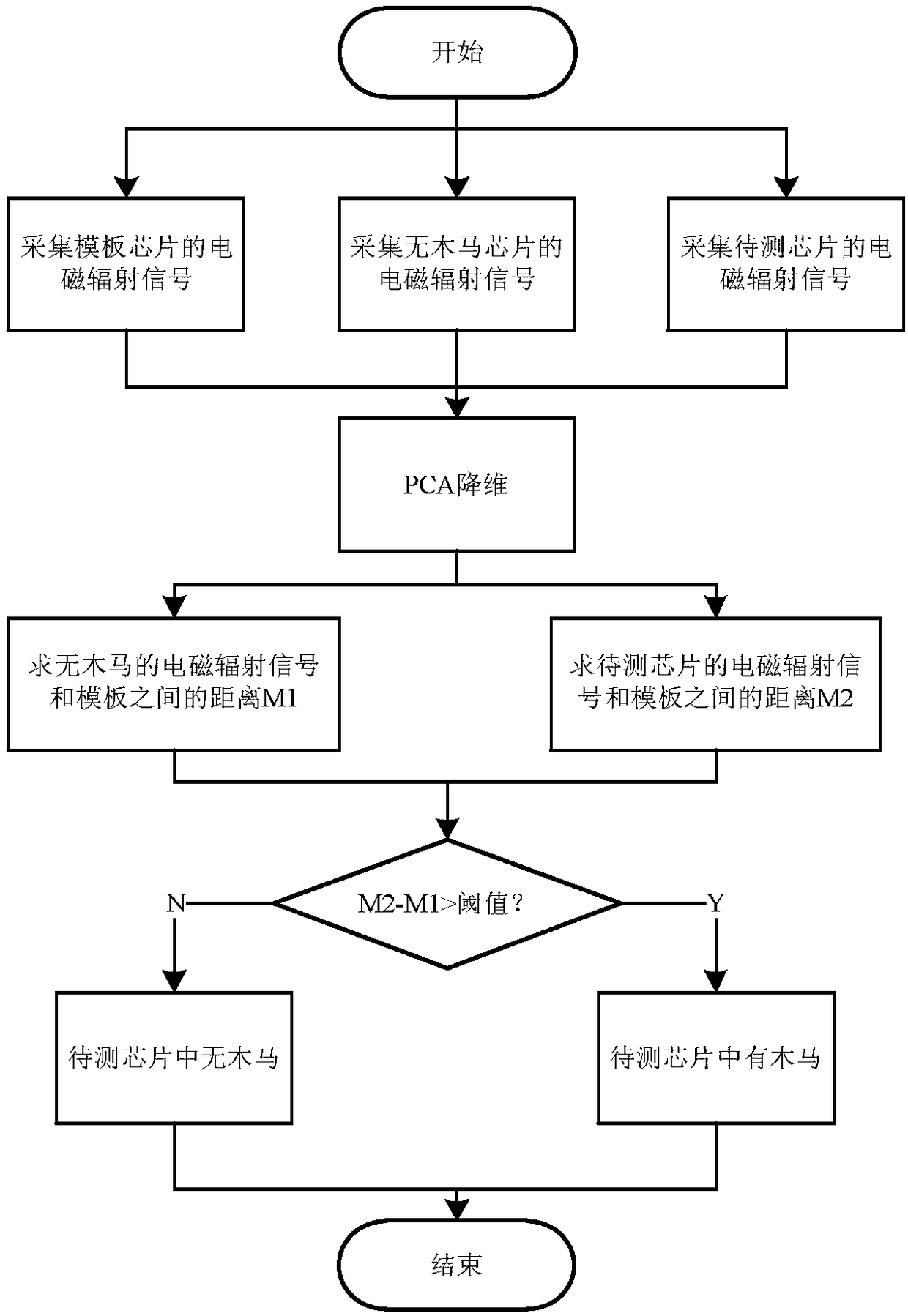
[0030] Such as figure 1 As shown, this embodiment provides a hardware Trojan detection method based on side channel information, and the detection steps include: data collection-data preprocessing-data analysis-drawing a conclusion. Specifically include:
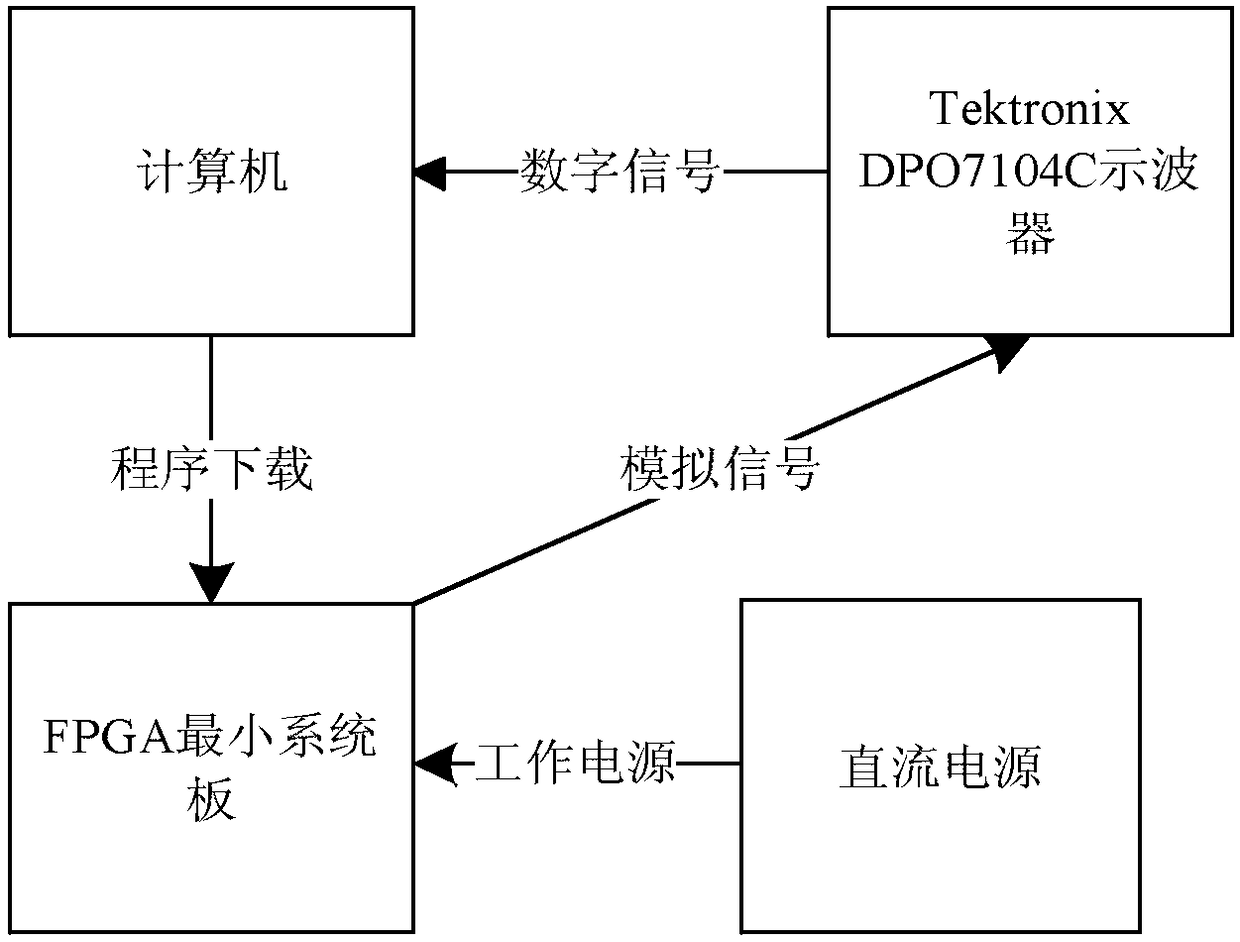
[0031] First build a chip electromagnetic leakage signal acquisition and detection platform, and then use Principal Component Analysis (PCA, Principal Component Analysis) method to reduce the dimension (data acquisition and preprocessing) of the collected electromagnetic signal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com