Data storage method for non-volatile storage space in chip and trusted chip
A non-volatile storage and data technology, applied in digital data processing, data processing input/output process, and key distribution, can solve the problems of poor accuracy of original data and achieve the effect of ensuring correctness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0046] According to an embodiment of the present invention, a method embodiment of a method for storing data in a non-volatile storage space in a chip is also provided.
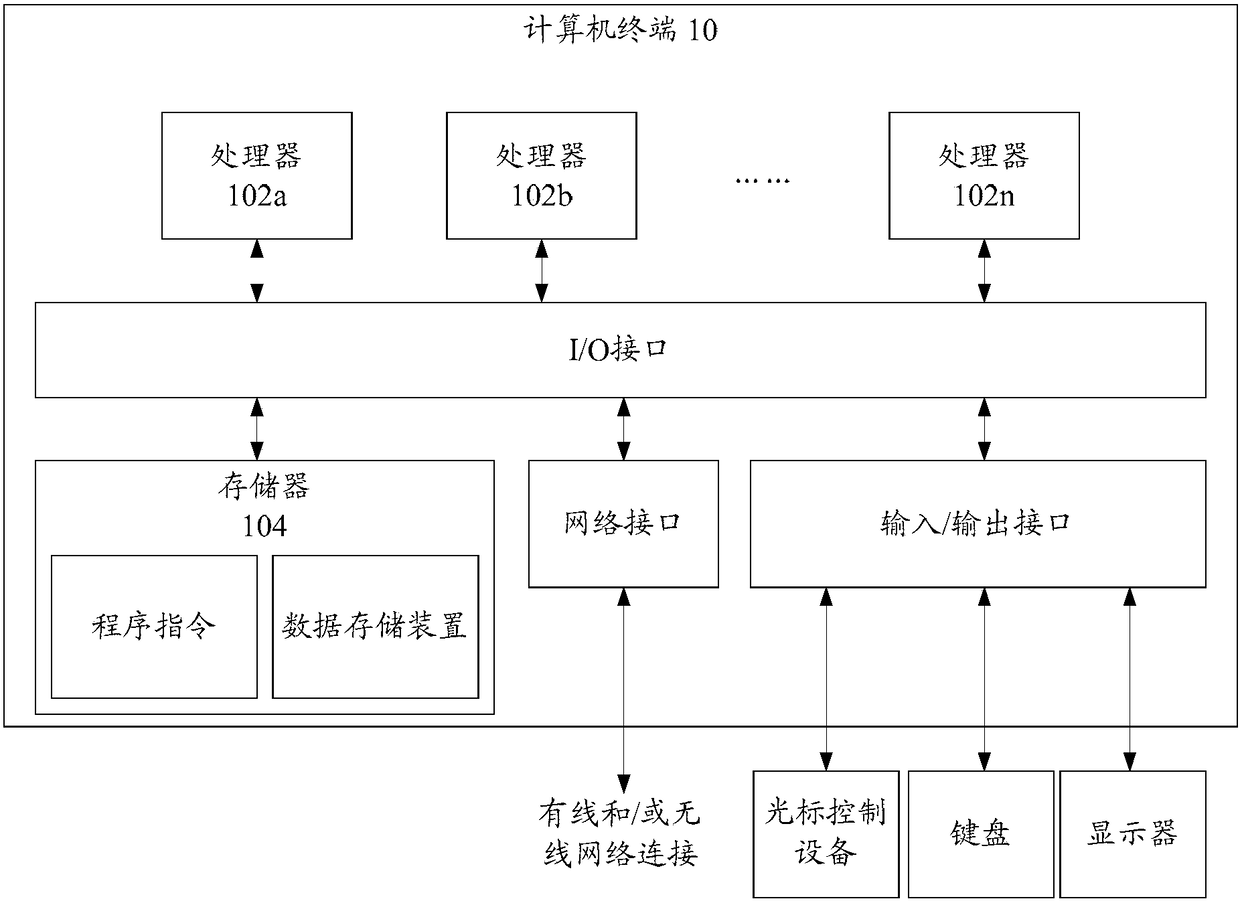
[0047] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. figure 2 It shows a hardware structure block diagram of a computer terminal (or mobile device) for realizing the data storage method of the non-volatile storage space in the chip. Such as figure 2 As shown, the computer terminal 10 (or mobile device 10) may include one or more (shown by 102a, 102b, ..., 102n in the figure) processor 102 (the processor 102 may include but not limited to a microprocessor MCU or a processing device such as a programmable logic device FPGA), a memory 104 for storing data, and a transmission module 4 for communication functions. In addition, it can also include: a display, an input / output interface (I / O inter...
Embodiment 2
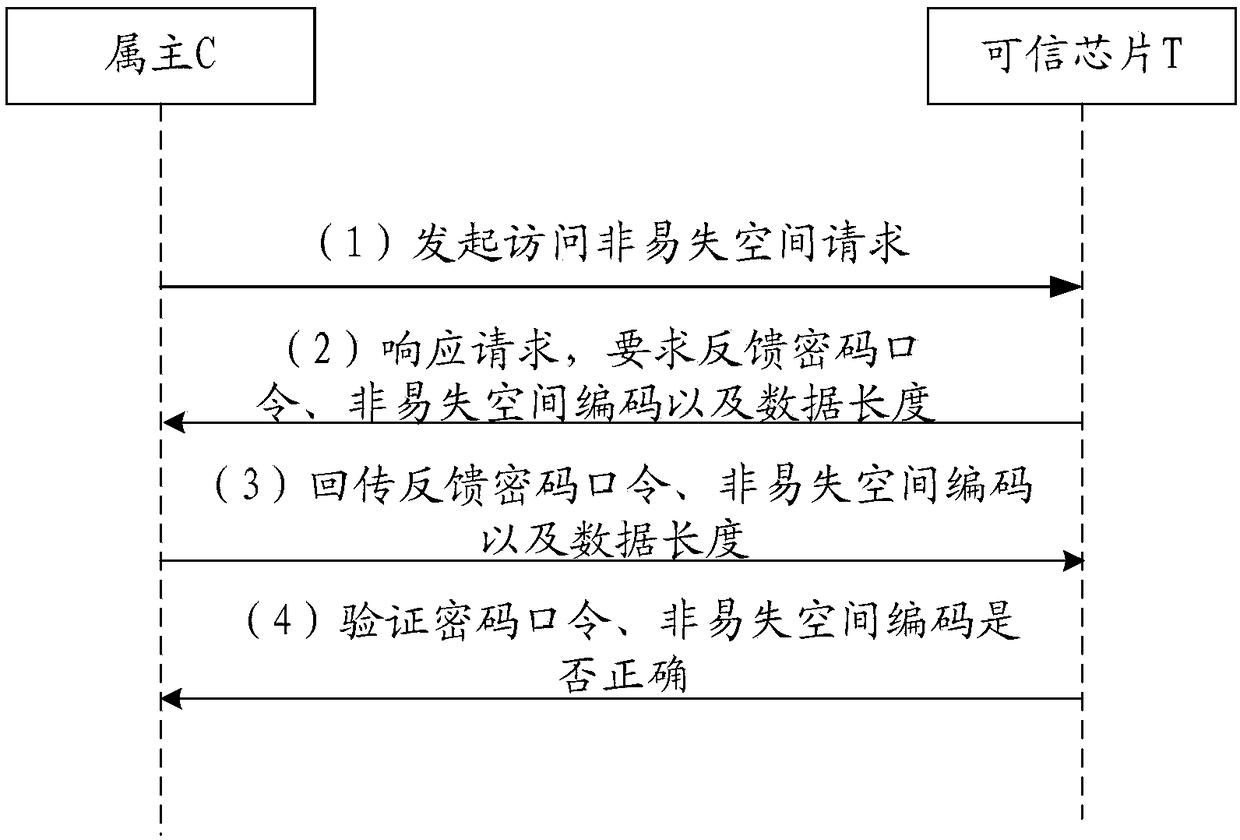
[0099] According to an embodiment of the present invention, an embodiment of a method for acquiring data stored in a chip is also provided.
[0100] This application provides Figure 7 Shown is the method of fetching data stored in the chip. Figure 7 is a flowchart of a method for acquiring data stored in a chip according to Embodiment 2 of the present invention. Including the following steps:
[0101] Step S702, receiving an access request for accessing the non-volatile storage space of the chip;
[0102] Step S704, responding to the access request, obtaining the verification information and the length of data to be requested;
[0103] Step S706, in the case that the verification information is passed, it is judged whether the length of the data to be requested is within the storage address range of the owner data preset in the non-volatile storage space;
[0104] Step S708, if the length of the requested data is within the storage address range of the owner data, the co...
Embodiment 3
[0124] According to an embodiment of the present invention, an embodiment of a trusted chip is also provided.
[0125] This application provides Figure 8 A schematic diagram of the structure of the trusted chip shown. Figure 8 is a schematic structural diagram of a trusted chip according to Embodiment 3 of the present invention, and the trusted chip includes: a memory 801 . in,
[0126] The memory 801 includes a non-volatile storage space, wherein the attributes of the non-volatile storage space at least include: parameters used to characterize the storage of owner data in the non-volatile storage space, and the storage address range of the owner data; Wherein, the storage address range of the owner data is used to represent the maximum data length allowed to request data from the chip.
[0127] In the technical solution defined by the above-mentioned memory 801, the storage mode of the above-mentioned non-volatile storage space can adopt big-endian mode and little-endian...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com