Android application permission overflow vulnerability detection and malicious behavior identification method
An application and vulnerability detection technology, applied in character and pattern recognition, program code conversion, decompilation/disassembly, etc., can solve the problems of code obfuscation, difficulty in effectively extracting typical features, and new unknown malware without killing, etc. Achieve the effect of reducing false positive rate, easy extraction and analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings.
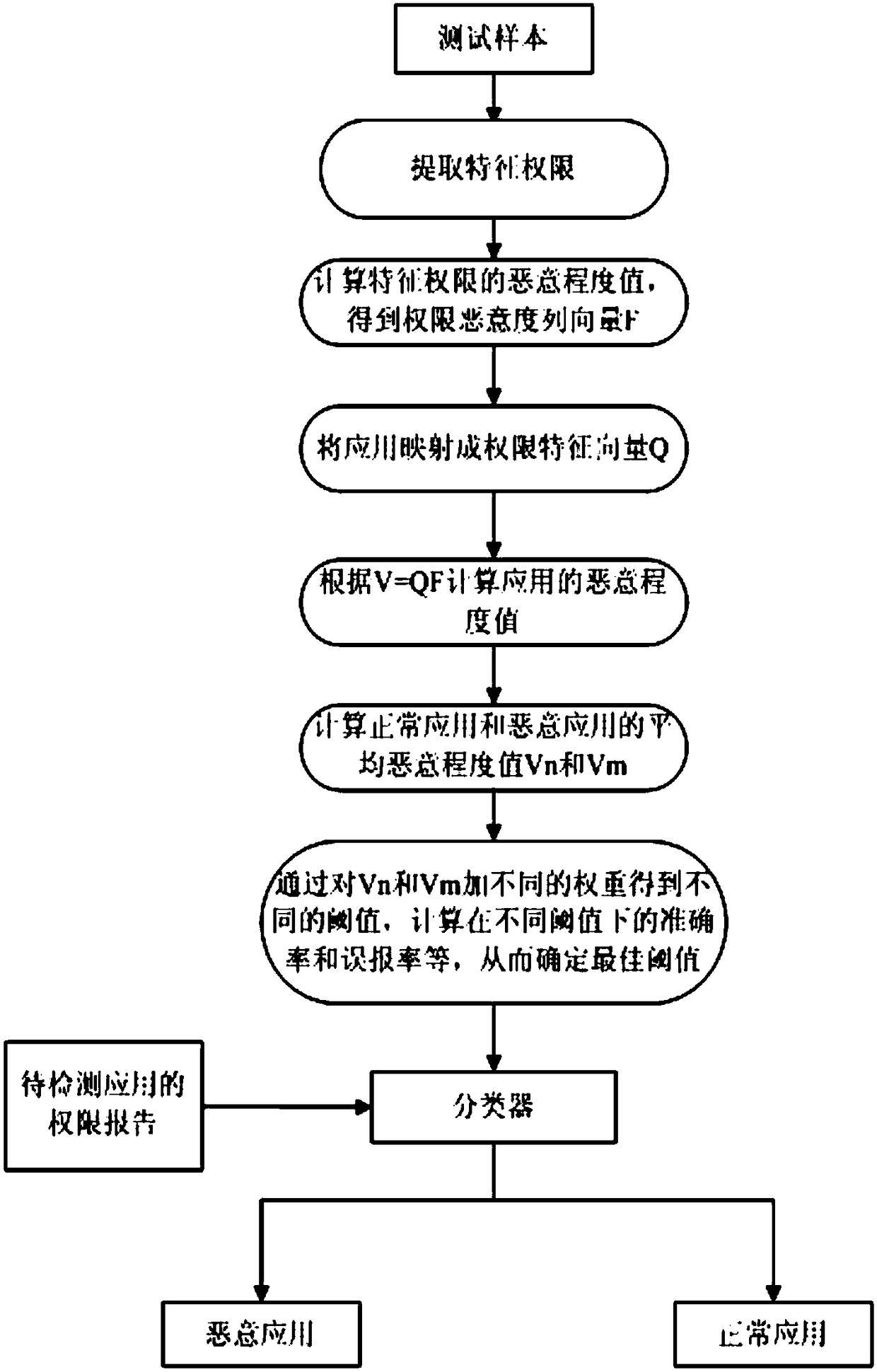
[0034] In a specific embodiment, the detection method specifically includes the following steps:
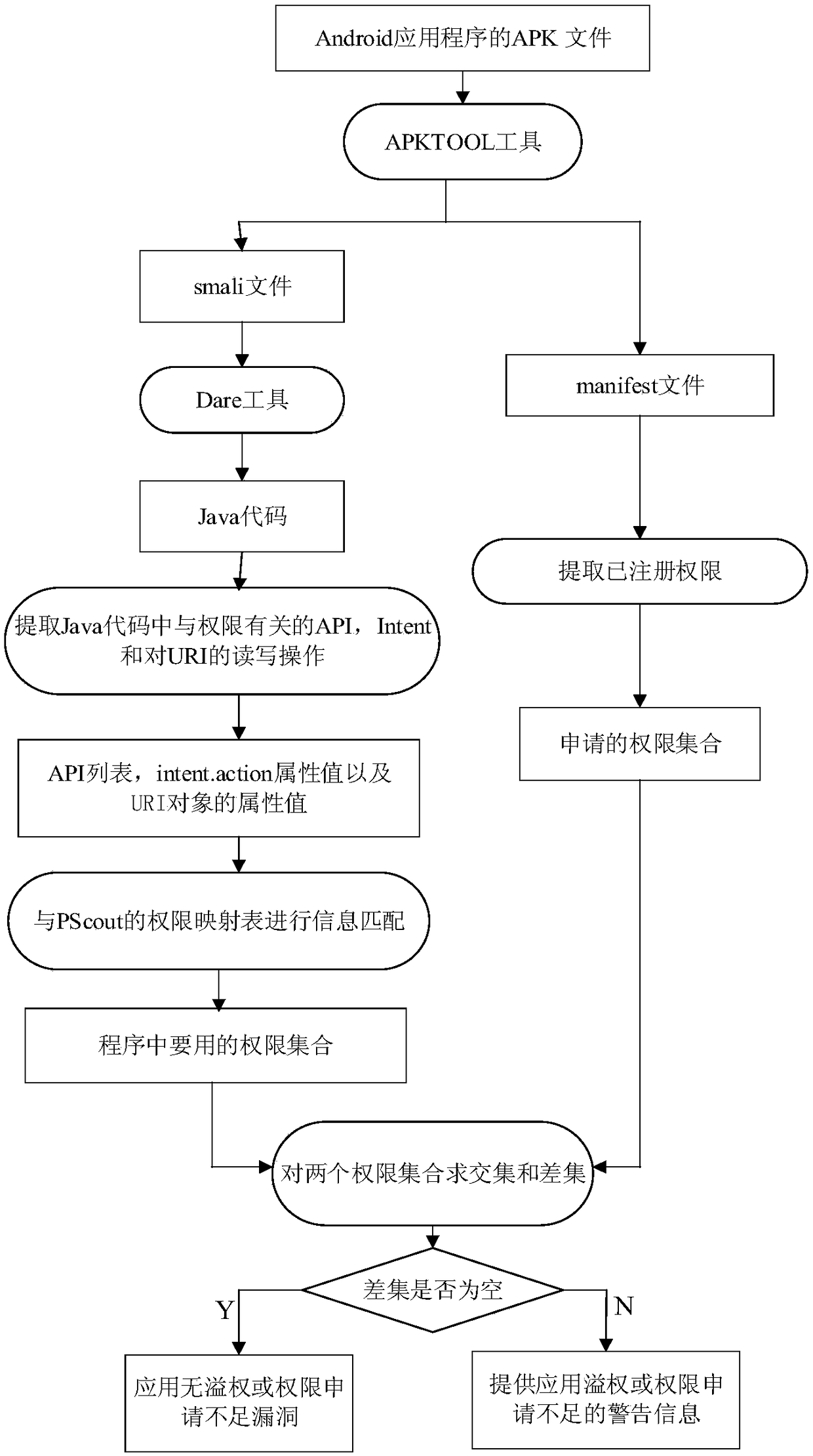
[0035] Step 1: Use APKTool and Dare to decompile the APK file to be tested to obtain a Java bytecode program, which is the basis for all subsequent analysis. Among them, APKTool translates the Android dex file into a smali file, and Dare converts the smali file format into a Java bytecode format for subsequent analysis.
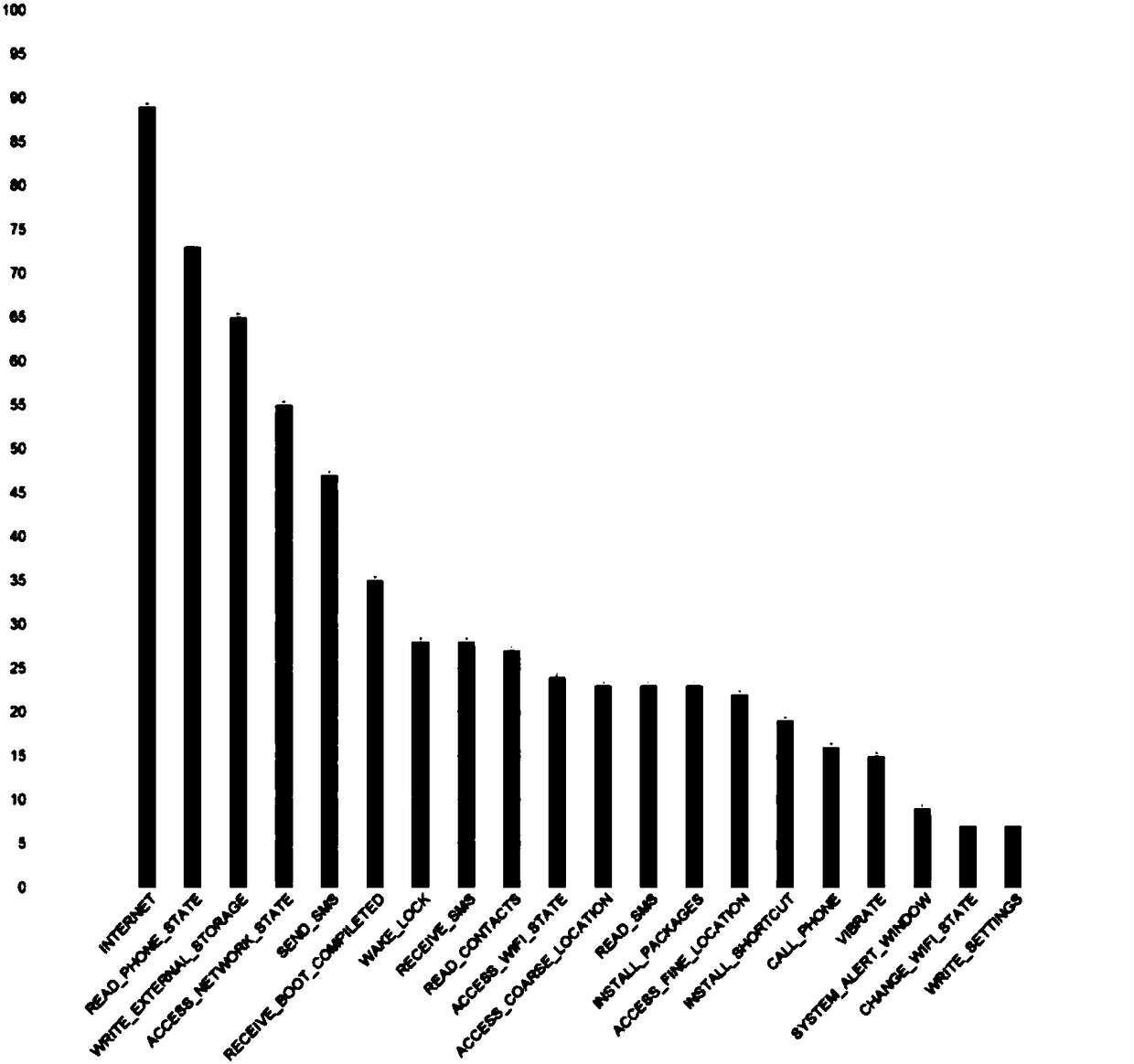
[0036] Step 2: Use string search to find all sensitive API calls in the program. "Sensitive API" refers to class methods that require permissions in the Android framework. Examples of sensitive APIs are shown in Table 1.
[0037] Table 1 Sensitive API and dependent permissions
[0038]
[0039] Step 3: The sending point of the Intent object refers to the code fragment in the program that sends the Intent object. The re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com