Identity authentication method and authentication device
An authentication device and identity authentication technology, applied in the field of communications, can solve the problems of inconvenience, interception of personal account numbers and passwords, cumbersome input, etc., and achieve the effects of improving convenience, improving convenience, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
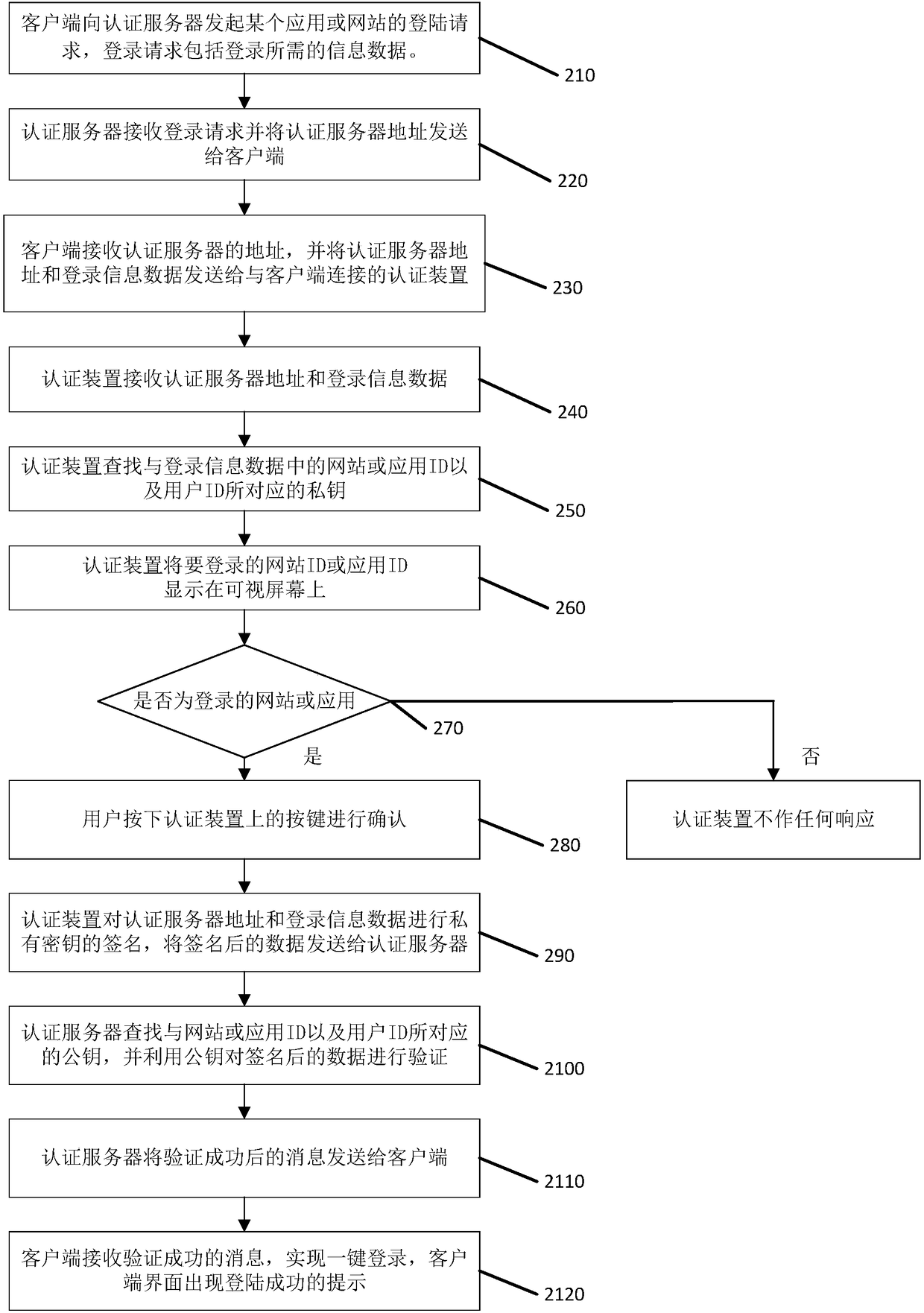
[0045] Such as figure 2 Shown is a login flowchart of a client, and its specific steps include:
[0046] Step S210: the client initiates a login request of an application or website to the authentication server, and the login request includes information data required for login.
[0047] As an embodiment, the login information data includes necessary information such as application or website ID and user ID, random numbers generated in response to the login request, and optional information such as personal security information questions.
[0048] Step S220: the authentication server receives the login request and sends the address of the authentication server to the client.
[0049] Step S230: the client receives the address of the authentication server, and sends the address of the authentication server and login information data to the authentication device connected to the client.
[0050] As an embodiment, the terminal with the client is connected to the authentication d...
Embodiment 2
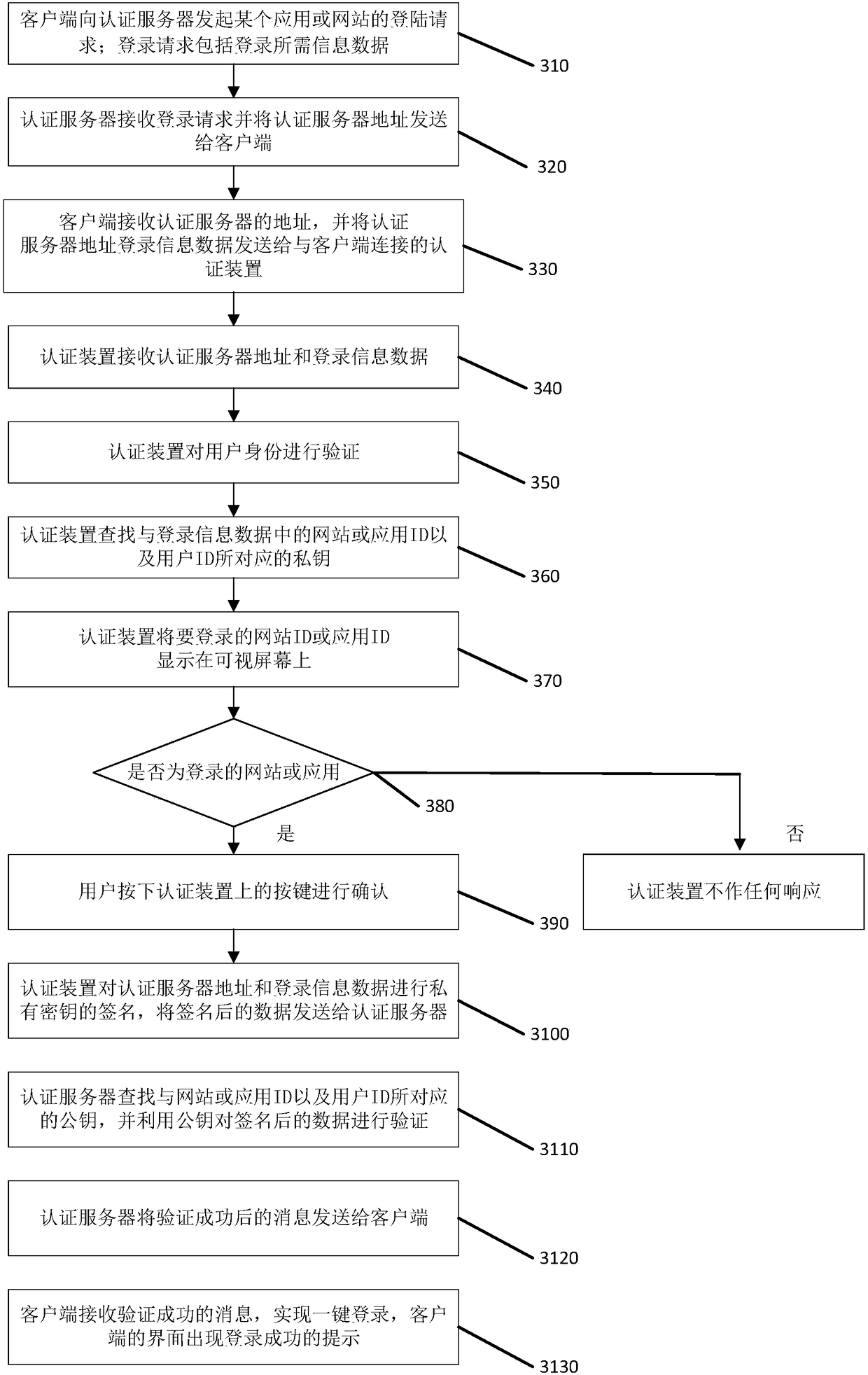
[0065] This embodiment provides an optimized client login solution, such as image 3 Shown is another client login flow chart, and its specific steps include:
[0066] Step S310: the client initiates a login request of an application or website to the authentication server; the login request includes information data required for login;
[0067] Step S320: the authentication server receives the login request and sends the address of the authentication server to the client. Specifically, the registered information data is the information data including the user's voice provided during registration.
[0068] Step S330: the client receives the address of the authentication server, and sends the address of the authentication server and login information data to the authentication device connected to the client.
[0069] As an embodiment, data transmission is performed between the client and the authentication device through a Bluetooth interface, WIFI and / or NFC.
[0070] Prefe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com