A method for detecting and mitigating ddos attacks on industrial sdn networks
An attack detection, industrial network technology, applied in the field of network security, can solve problems such as difficult research results in industrial SDN networks, industrial network network characteristics, real-time requirements, reliability requirements are not considered, importing data packets, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0098] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
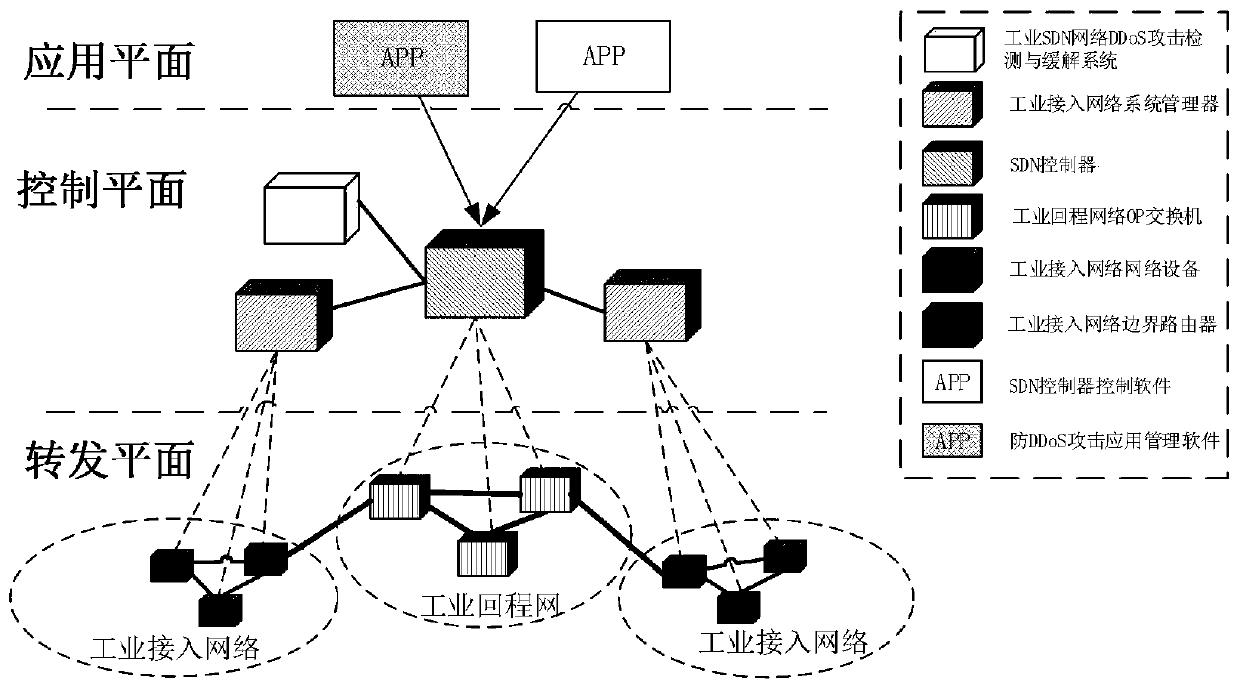
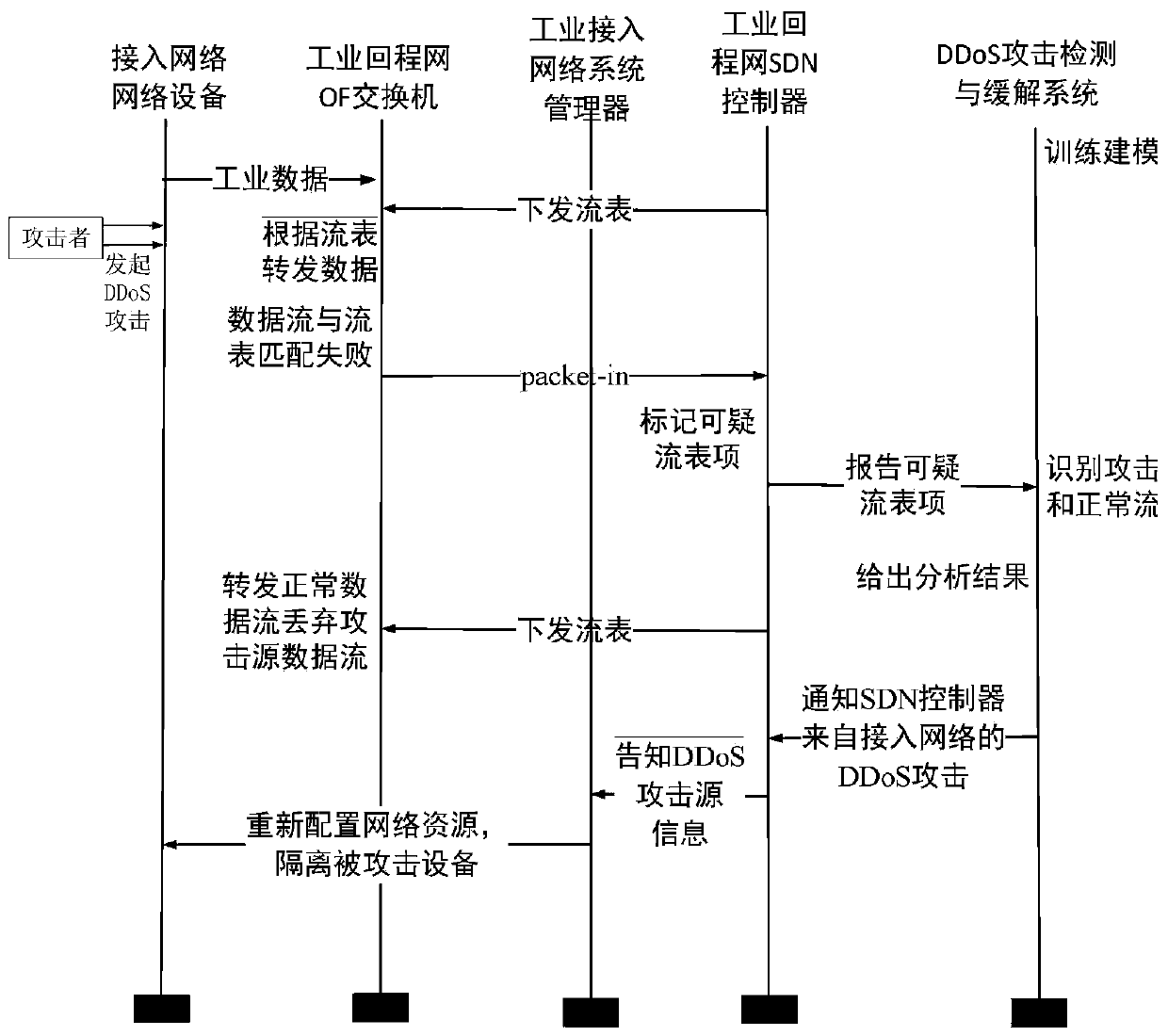
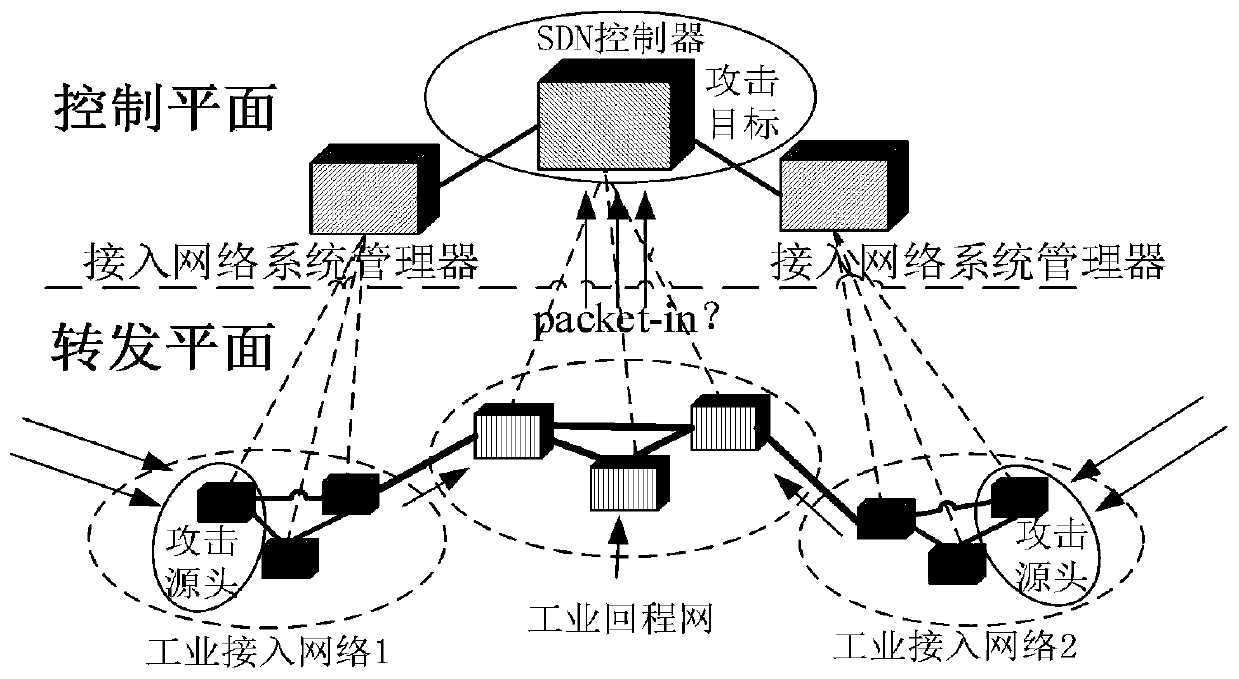
[0099] Aiming at the typical SDN-based industrial backhaul network architecture, an industrial network DDoS detection and mitigation architecture under the SDN-based joint scheduling architecture is proposed, such as figure 1 As shown, it includes application plane, control plane and forwarding plane.
[0100] The application plane includes SDN controller control software and anti-DDoS attack application management software.
[0101] ●SDN controller control software: the user configures the SDN controller through this software.
[0102]● Anti-DDoS attack application management software: It can support security personnel to formulate corresponding defense strategies according to the characteristics of network DDoS attacks to ensure safe operation of the network.
[0103] The control plane includes SDN controller, industrial access network ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com