Method and system for detecting interest packet flooding attack in content center network
A content-centric network, flooding attack technology, applied in the field of interest packet flooding attack detection in content-centric networks, can solve the problems of high algorithm complexity, inappropriate attacker attack forms, etc., to reduce false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] In order to enable those skilled in the art to better understand the purpose, technical solutions and beneficial effects of the present invention, a complete description will be given below in conjunction with specific embodiments and accompanying drawings.
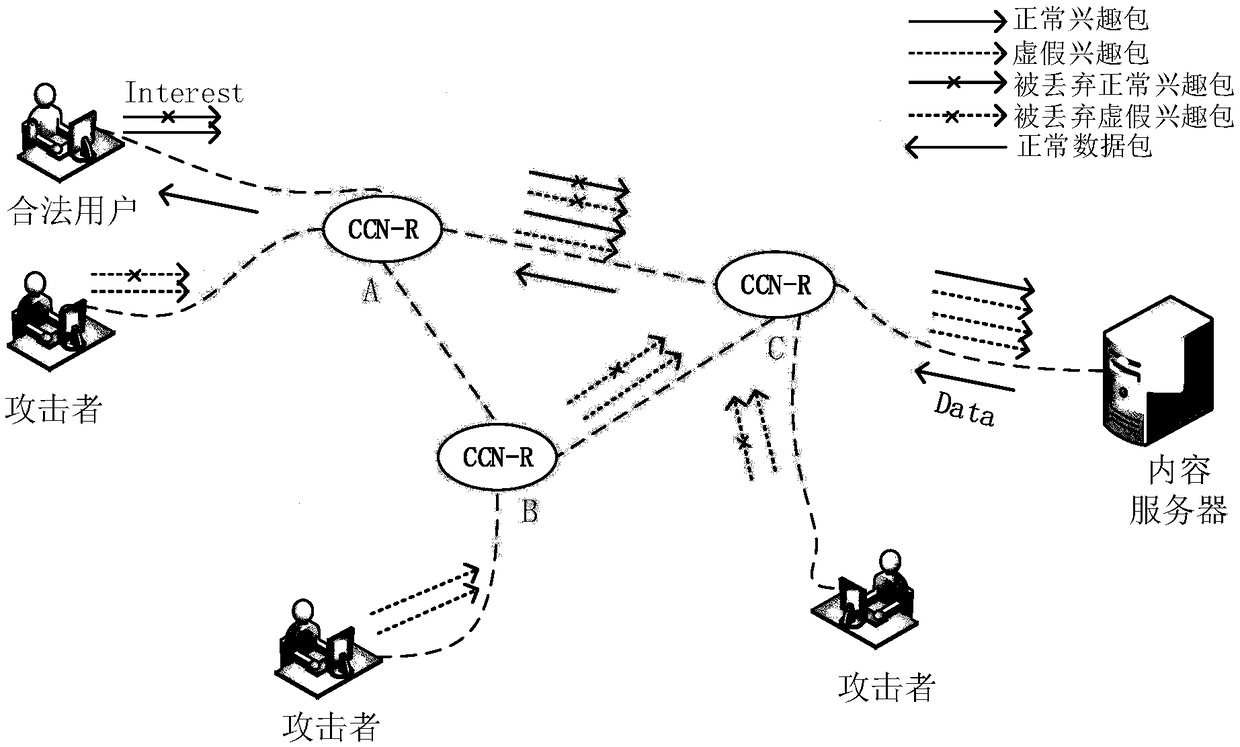
[0047] The invention provides an attack schematic diagram of an interest packet flood attack in a content-centric network. Such as figure 1 As shown, in the content-centric network, when the attacker sends a large number of false interest packets to the network, the router in the network is full of the space of its pending interest table PIT. At this time, the router will directly send the normal interest requested by the legitimate user The packet is discarded so that the legitimate user does not get a response with the corresponding packet.
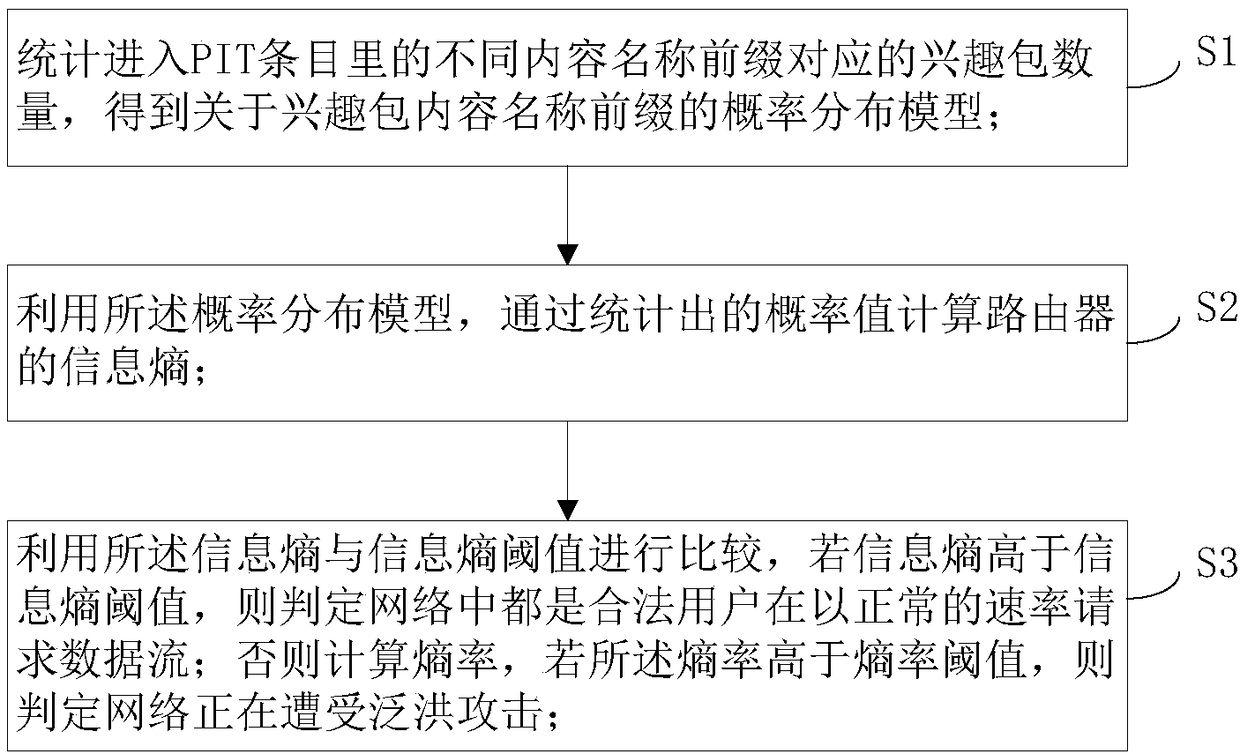
[0048] A flowchart of a method for detecting interest packet flooding attacks in a content-centric network provided by the present invention. Such as figure 2 As shown, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com