Anti-attack and defense method based on LSTM (Long Short Term Memory) detector
A detector and detection rate technology, applied in the direction of neural learning methods, instruments, biological neural network models, etc., can solve the problems of poor detection effect, increased detection rate, low safety, etc., to achieve accurate measurement values and detection results, increase The effect of detection rate, strong robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further described below in conjunction with the accompanying drawings.
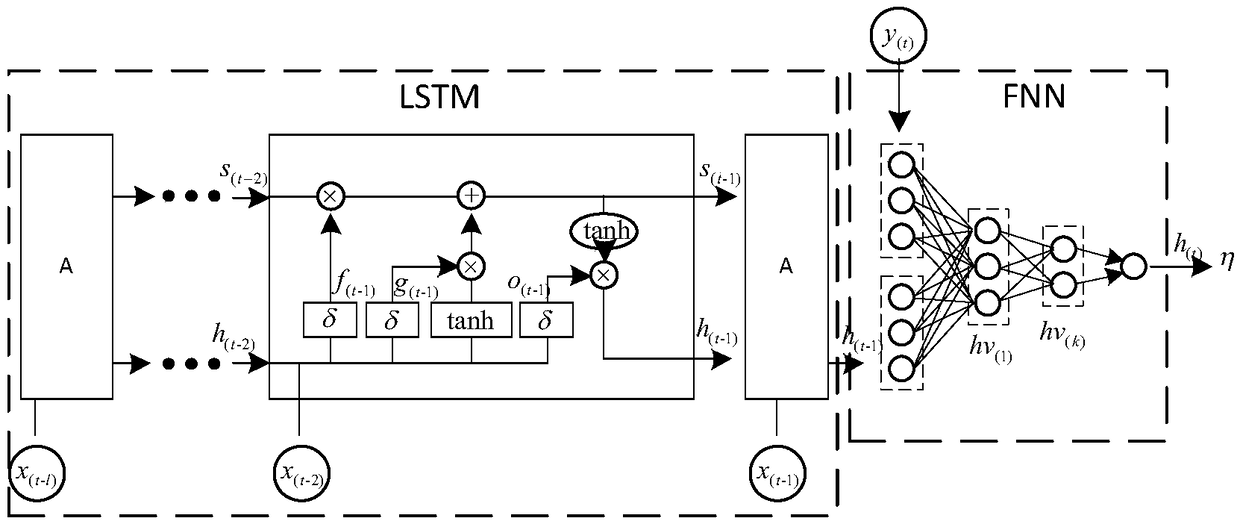
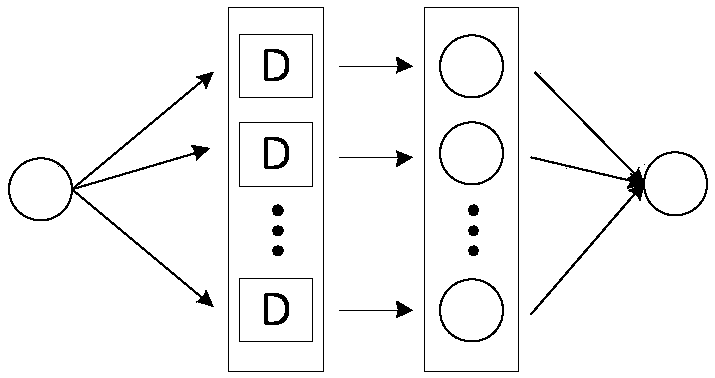
[0049] refer to Figure 1 ~ Figure 3 , an LSTM detector-based adversarial attack defense method, comprising the following steps:
[0050] 1) Generate a set of adversarial sample detectors, the process is as follows:
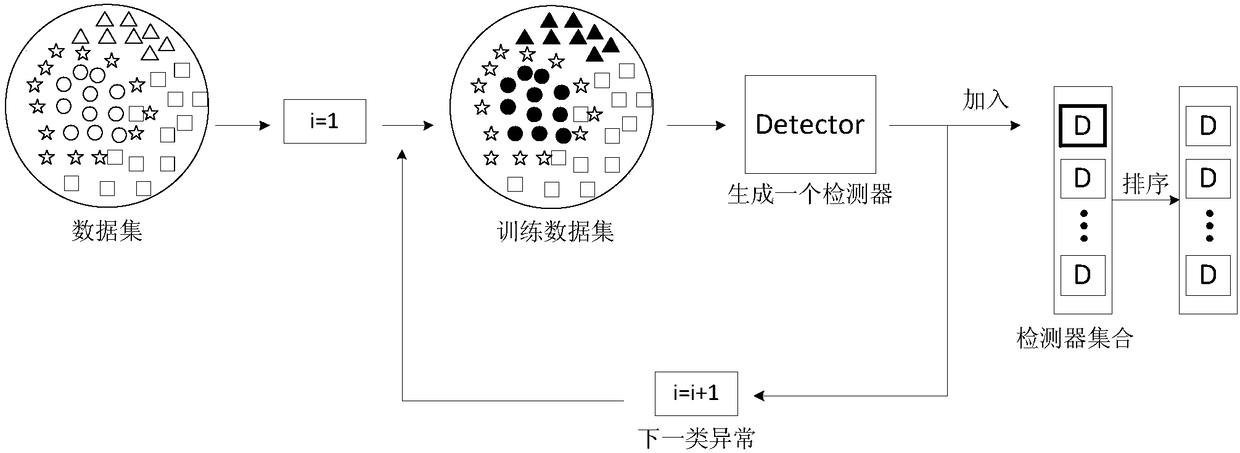
[0051] 1.1) Intercept the time series data with a sliding window of length l as the original training data set X={x (1) ,x (2) ,...},x (t) ={y (t) ,u (t)},y (t) Indicates the measured value at time t, u (t) Indicates the control value at the moment, where the normal sample is denoted as X', and the adversarial sample is denoted as i represents the i-th type of adversarial samples, there are w kinds of adversarial samples, let i=1; figure 1 The middle data set represents the original training data set, the circle represents normal data, and the other shapes represent adversarial sample data obtained from different attacks;
[0052] 1.2) Since th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com