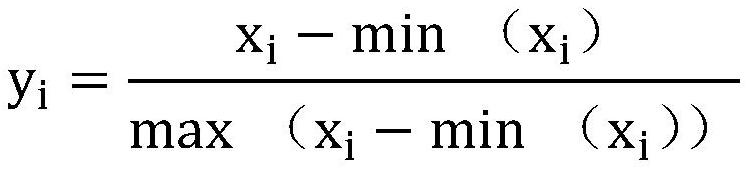An Intrusion Detection Method Based on Two-way Optimal Support Vector Machine of Taboo and Artificial Bee Colony
A technology of support vector machine and artificial bee colony, which is applied in the field of network security, can solve the problems of inability to solve the minimum feature subset search, low feature selection search efficiency, and difficulty in synchronizing parameter optimization with search and modeling, so as to improve the neighborhood. Search capability, speed up algorithm convergence, expand the effect of diversity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in combination with specific examples and with reference to the accompanying drawings.
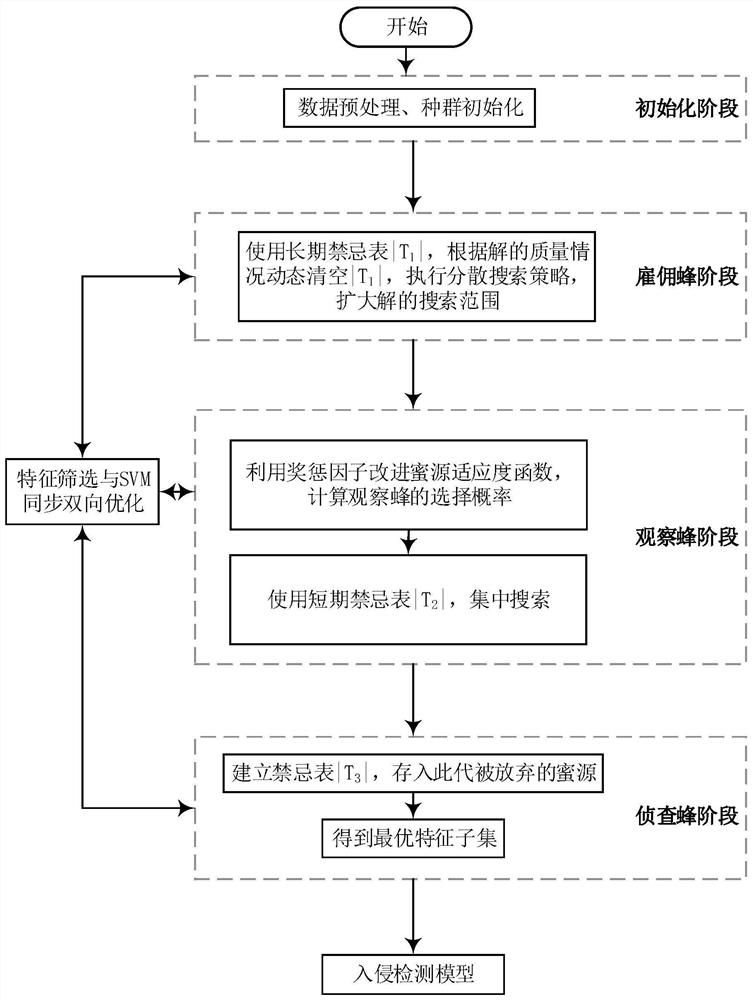
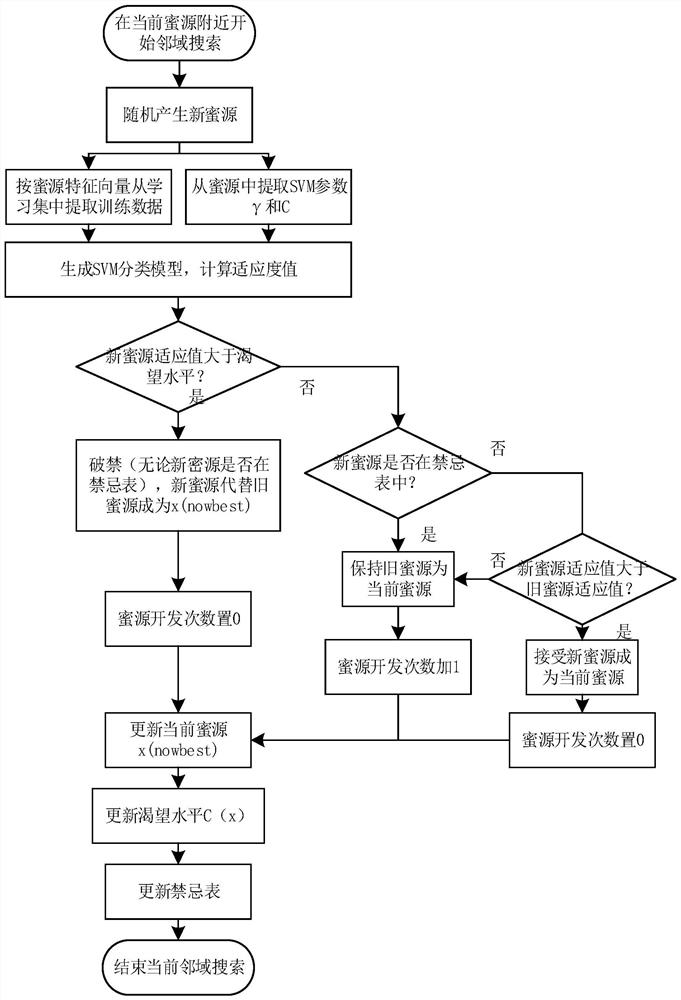
[0057] The present invention is based on the intrusion detection method of taboo and artificial bee colony bidirectional optimization support vector machine, firstly reconstructs the original artificial bee colony algorithm, the general idea is to encode the honey source and support vector machine parameters to be optimized synchronously, and use the random generation method Generate the initial solution of the nectar source, and execute the search strategy based on the taboo-artificial bee colony to find the optimal feature subset. Specifically, it includes introducing the first taboo table in the hired bee search stage, storing and memorizing the local optimal solutions found, and avoiding these local optimal solutions in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com