Method for implementing efficient and safe transmission of data between cloud computing servers
A cloud computing server and secure transmission technology, applied in the field of information security, can solve problems such as inability to achieve eCK security and low protocol efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
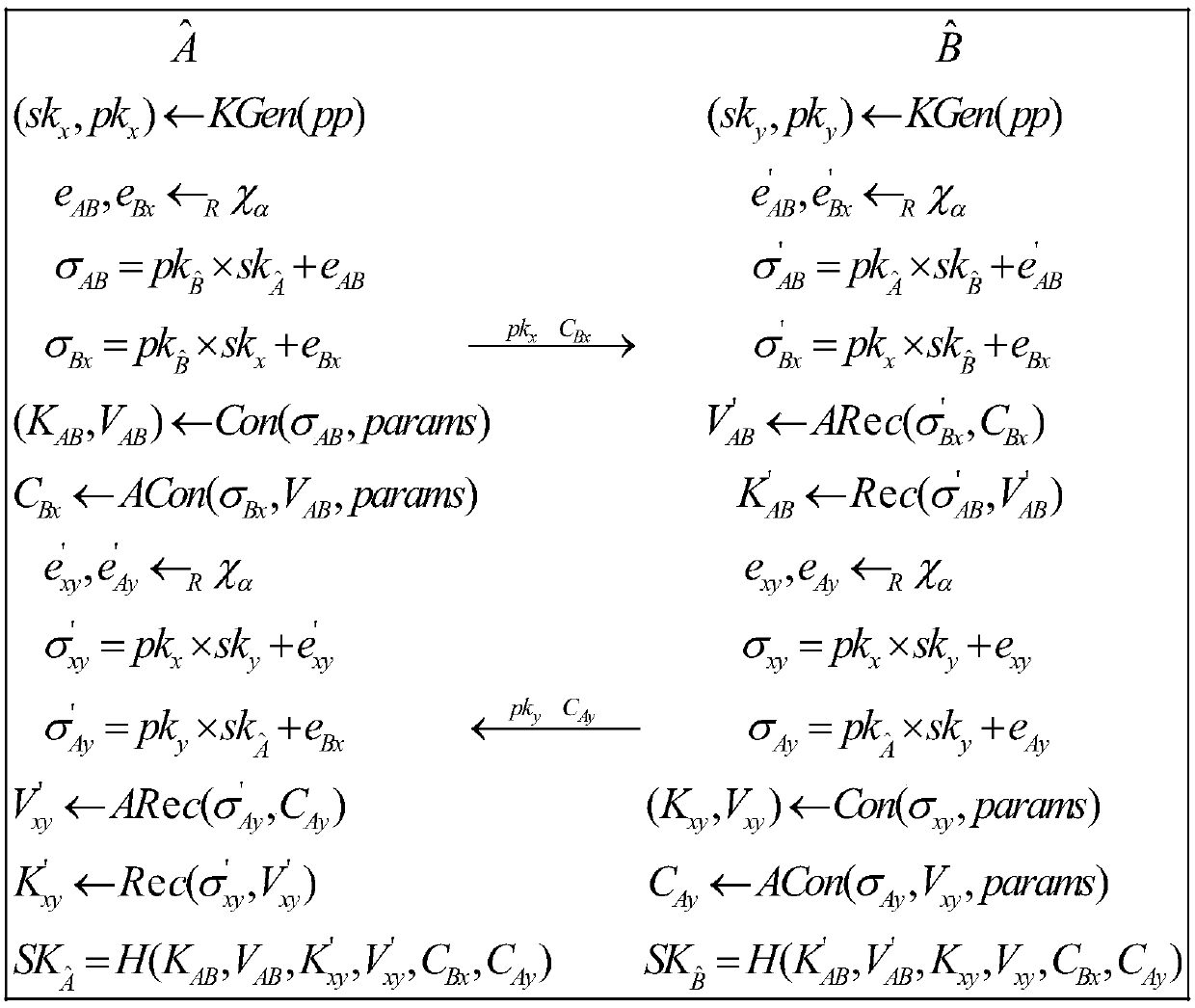
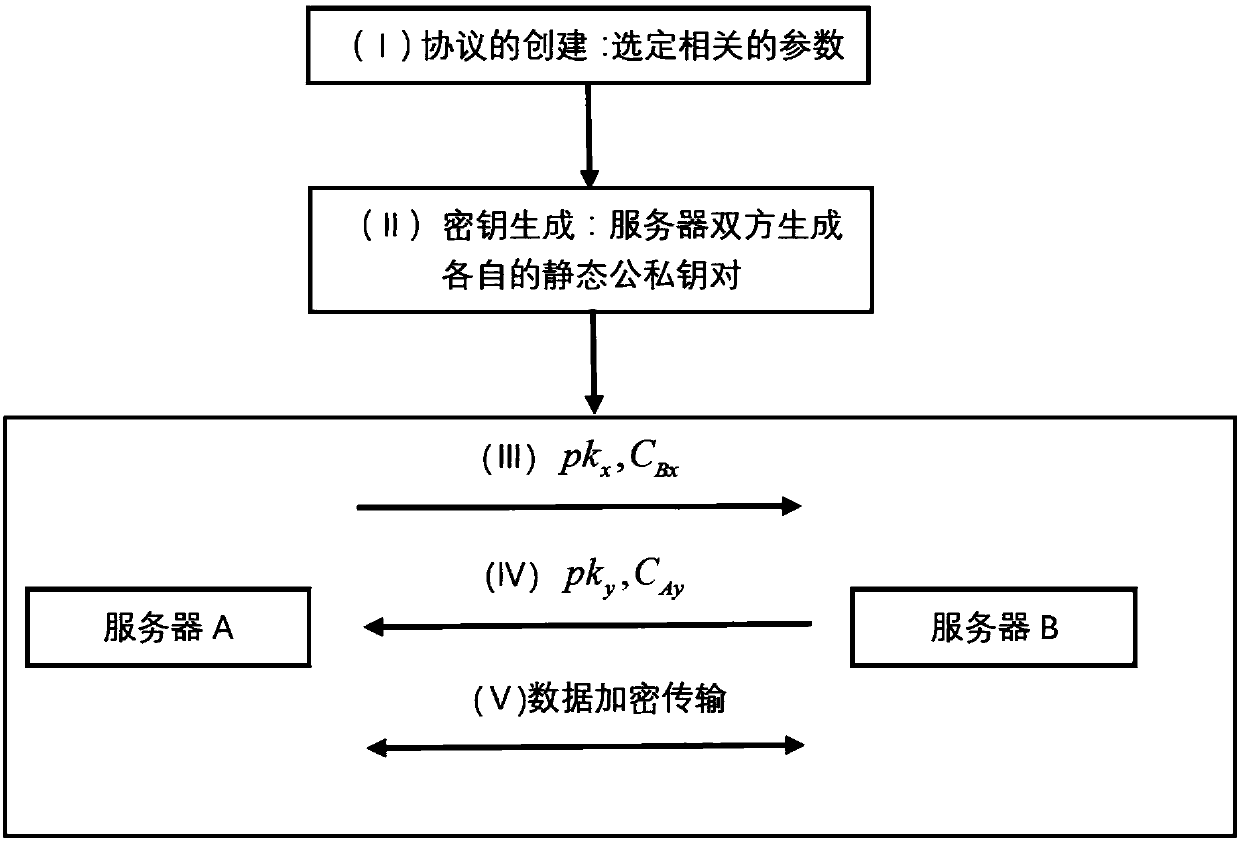
[0060] The most widely used authentication key agreement between cloud computing servers is constructed based on traditional number theory puzzles. The invention constructs an anti-quantum attack authentication key agreement agreement among cloud computing servers based on the ideal lattice. Compared with many current authentication key exchange protocols based on ideal lattice, the present invention requires less transmission bandwidth, and is highly efficient and safe.
[0061] The present invention uses the technology of symmetric key consensus (Key Consensus with Noise, OKCN) and asymmetric key harmony (Asymmetric Key Consensus with Noise, ACKN) proposed by Zhao et al. The OKCN and AKCN algorithms are briefly introduced below.
[0062] In the algorithm OKCN, params=(q, m, g, d, aux) is the algorithm parameter, where q, m, g, d are positive integers, and satisfy m≤2, g≤q, aux=(q', α, β) Specifically, q'=lcm(q,m), lcm( ) is the function of taking the least common multiple,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com