Home network connection authentication method and device, electronic equipment and storage medium
A network connection and home network technology, applied in the field of electronic equipment, storage media, devices, and home network connection authentication methods, can solve the problem of poor user experience, WiFi is vulnerable to attack and cracking, and routers have no network management and security protection, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
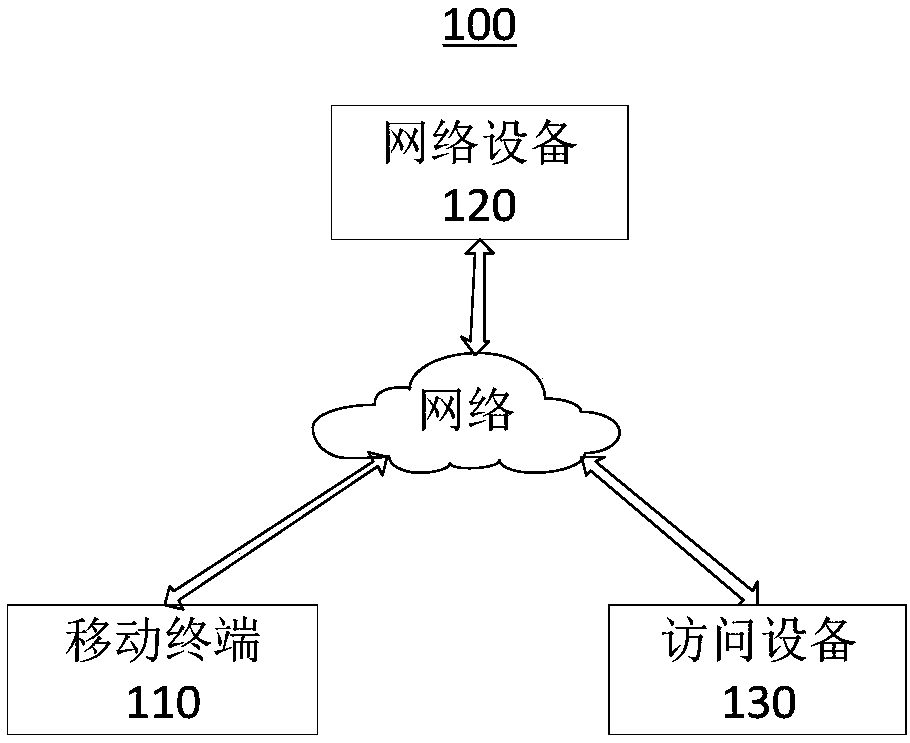
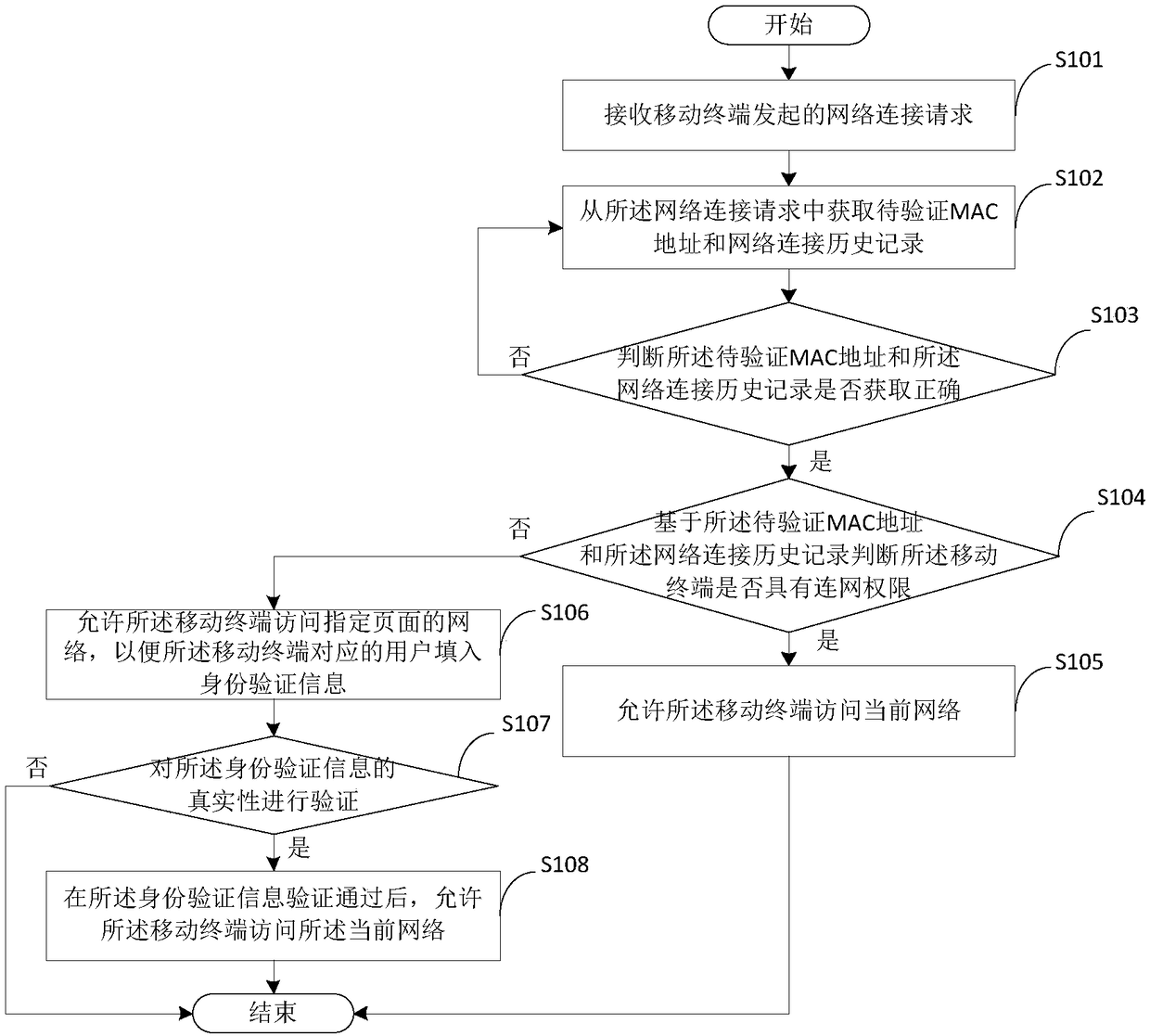
[0031] See image 3 , Is a home network connection authentication method applied to the above-mentioned network device 120 provided by an embodiment of the present invention. The following will combine image 3 Explain the steps involved.
[0032] Step S101: Receive a network connection request initiated by a mobile terminal.
[0033] When the mobile terminal turns on the WiFi broadcast and enters the range covered by the network of the home intranet, the network device can receive the WiFi broadcast information of the mobile terminal, that is, receive the network connection request initiated by the mobile terminal.
[0034] Step S102: Obtain the MAC address to be verified and the network connection history record from the network connection request.
[0035] The network device records and analyzes WiFi broadcast information (network connection request). Further, when the network device analyzes the network connection request, it obtains the MAC address to be verified and the network c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com