Communication method of terminal equipment equipped with encryption system and third-party application installing method
An encryption system and terminal equipment technology, which is applied in the field of secure communication, can solve problems such as failure of encryption methods, easy transplantation of encryption libraries, and inability to carry out encrypted communication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
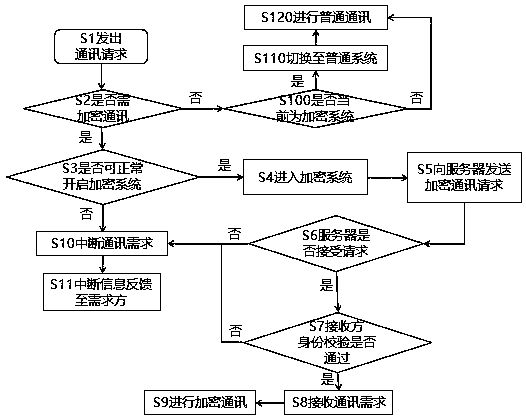
[0054] This embodiment will take a mobile phone as an example. The mobile phone has a common system and an encryption card that can be plugged and connected with the mobile phone. An encryption system is built in the encryption card. In the method, it is also necessary to provide an encryption system server; please refer to figure 1 , what is described is a communication method of a terminal device with an encryption system, and the communication method includes the following steps:
[0055] S1 user sends a communication request;
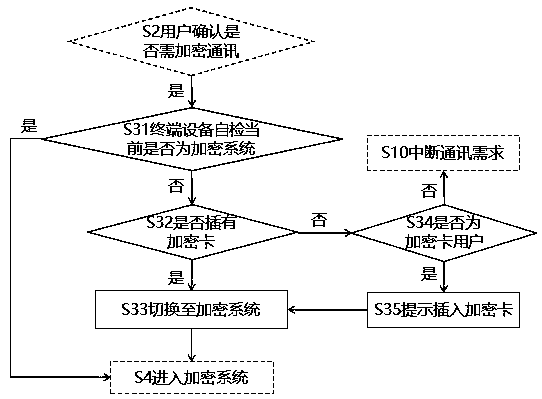
[0056] S2 user confirms whether encrypted communication is required,
[0057] If so, enter S3, if not, enter S100;
[0058]Whether the S3 terminal device can normally enable the encryption system,
[0059] If yes, enter S4; if not, enter S10;
[0060] S4 enters the encryption system;
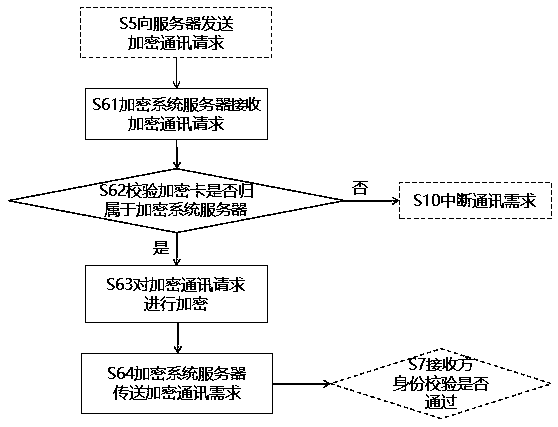
[0061] The S5 terminal device sends an encrypted communication request to the encryption system server;
[0062] Whether the S6 encryption system server accepts...
Embodiment 2
[0103] Before proceeding to the description of Embodiment 2, it should be reminded that since Embodiment 2 and Embodiment 1 have the same or similar parts in the authentication of encrypted card users, in the description of Embodiment 2, this part is Without going into details, please refer to the content of Embodiment 1 for understanding.
[0104] According to the second embodiment of the present invention, a third-party application installation method for a terminal device with an encryption system is also provided, please refer to Figure 5 , the installation method includes the following steps:
[0105] S01 Issue a third-party application installation request;
[0106] S02 The user confirms whether encryption is required for installation,
[0107] If so, enter S03, if not, enter S200;
[0108] S03 Whether the terminal equipment can normally open the encryption system,
[0109] If yes, enter S04; if not, enter S08;
[0110] S04 Enter the encryption system;
[0111] S0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com