Multi-intelligent-device identity authenticating method in combination with wearable device
A technology of wearable devices and smart devices, applied in the direction of digital data authentication, etc., can solve the problems of not being able to protect user privacy and property security, user physiological information leakage, etc., and achieve the effect of high safety and reliability, accuracy and reliability improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0032] The multi-smart device identity authentication method combined with the wearable device of the present invention includes the following links:
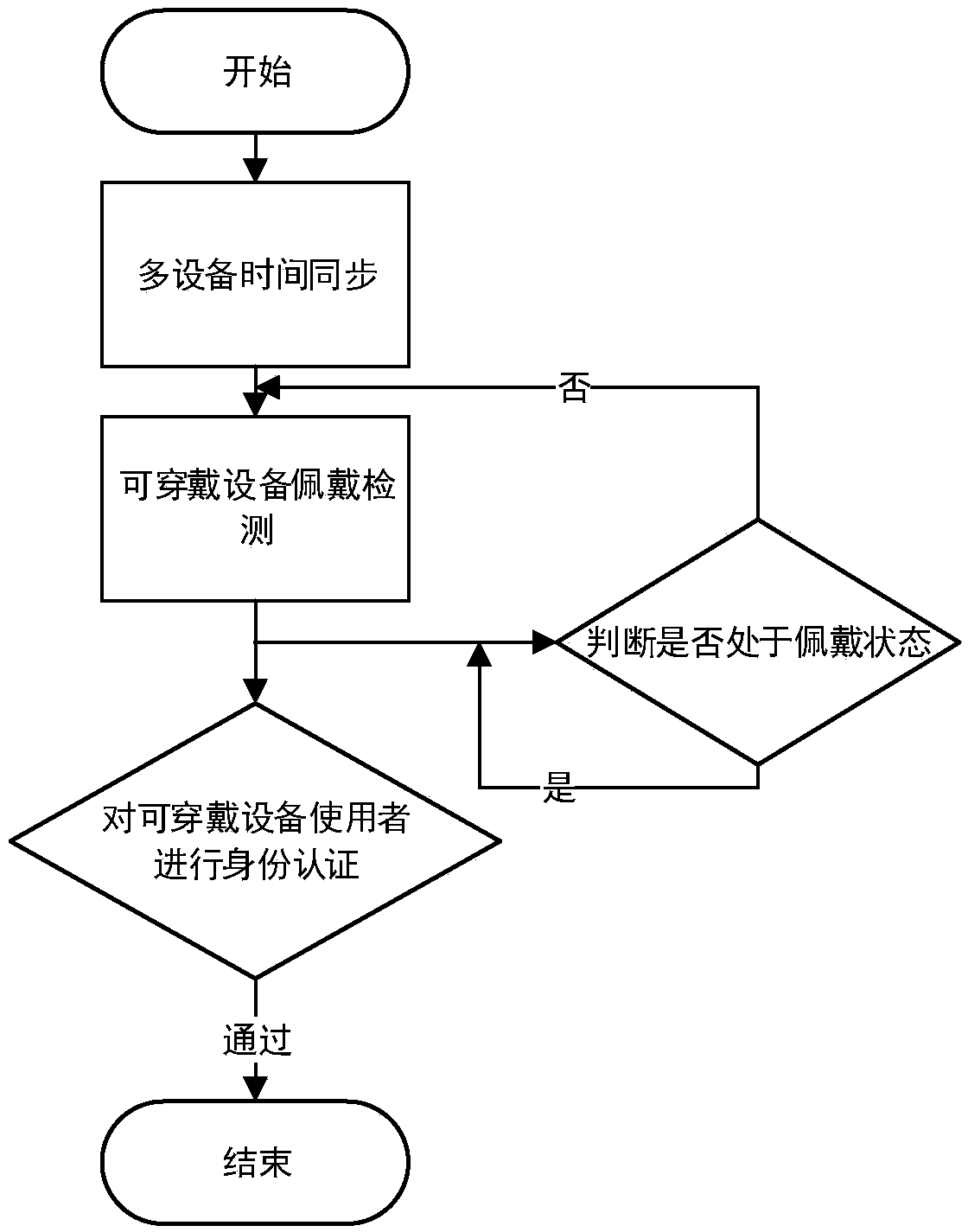
[0033] Link 1: Time synchronization between multiple devices and trusted status setting of smart bracelets;
[0034] The smart terminal and the smart bracelet align their respective time systems synchronously and set them to the same time stamp system.
[0035] The user pairs and connects the smart terminal with the smart bracelet, and the smart bracelet judges the use according to the signal of wearing the lock buckle and the collected physiological signals such as the user's heartbeat, skin electricity, body temperature, and the signals of the gyroscope, accelerometer and other motion sensors Whether the person wears a smart bracelet:
[0036] 1) If the fastening signal of wearing a lock is detected, and at the same time, one or more physiological signals such as heartbeat, skin electricity, and body temperature of the user ...
Embodiment 2
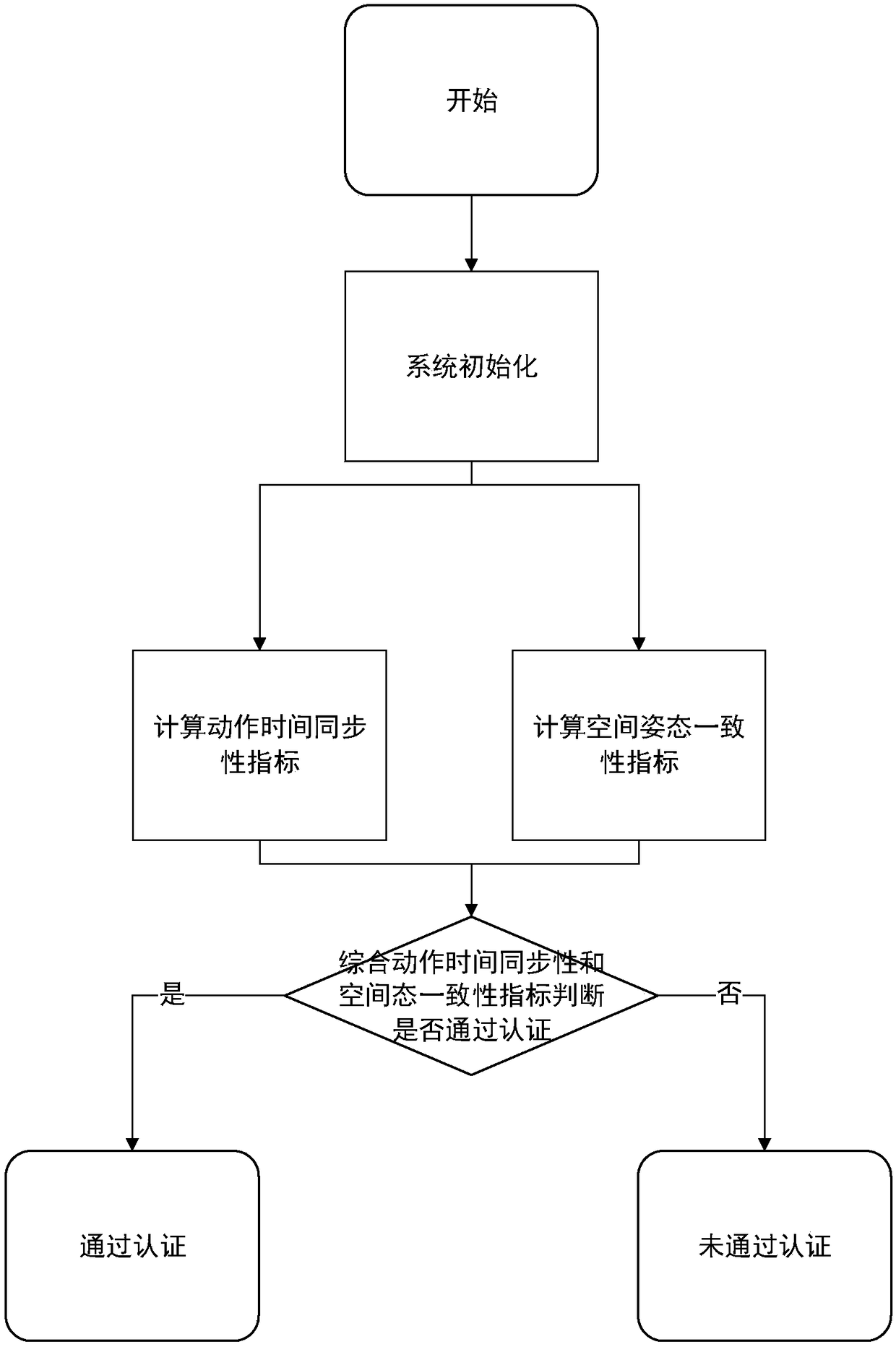
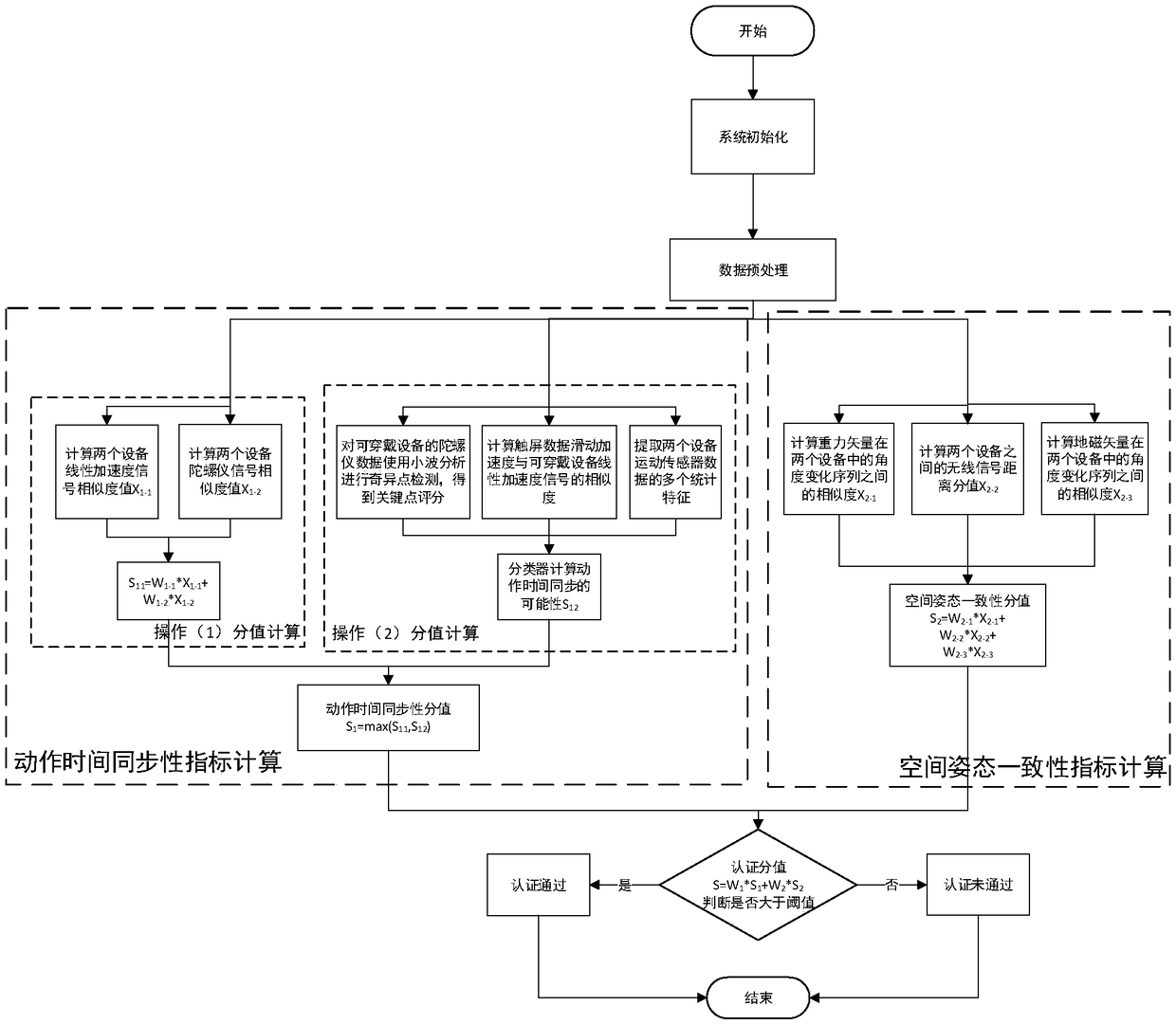
[0116] The flow chart of concrete implementation example 1 of the present invention is as figure 2 with Figure 4 As shown, it is a multi-smart device identity authentication method and system combined with wearable devices. The smart device is a smart terminal equipped with buttons, and the wearable device is a smart bracelet equipped with acceleration, gyroscope sensors and magnetometers. The button operation performed on the smart terminal, the real-time sensor data such as the acceleration, gyroscope, and magnetometer of the smart terminal and the smart bracelet, and judging the movement time synchronization and spatial attitude consistency between multiple devices during interactive operations are based on this. Realize continuous authentication and unlock authentication of user operations on smart terminals.
[0117] The continuous authentication can be the authentication of the interactive behavior within a sliding time window; the unlocking authentication can be the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com