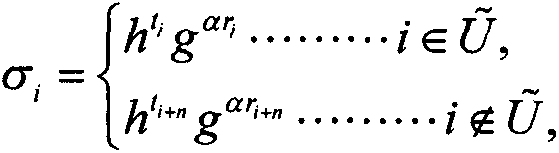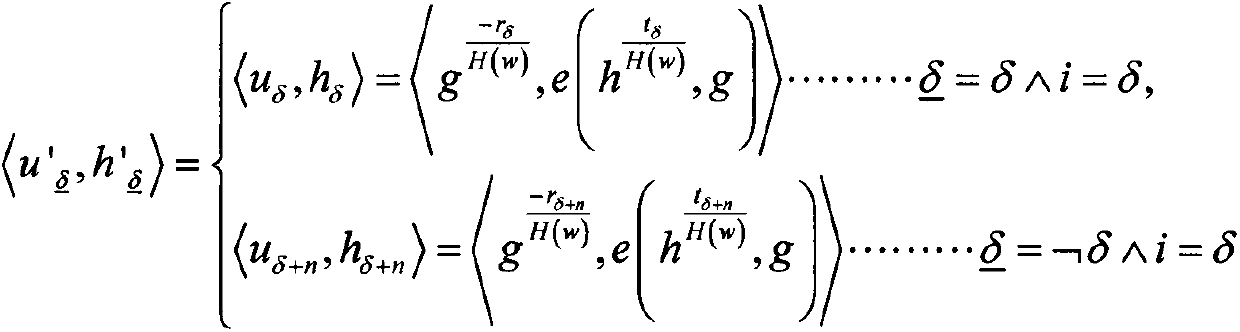Encryption method supporting non-monotone access structure, with constant cipertext length and capable of searching attribute set
An access structure, non-monotonic technology, applied in the field of computer security, to achieve the effect of reducing computing costs and communication costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
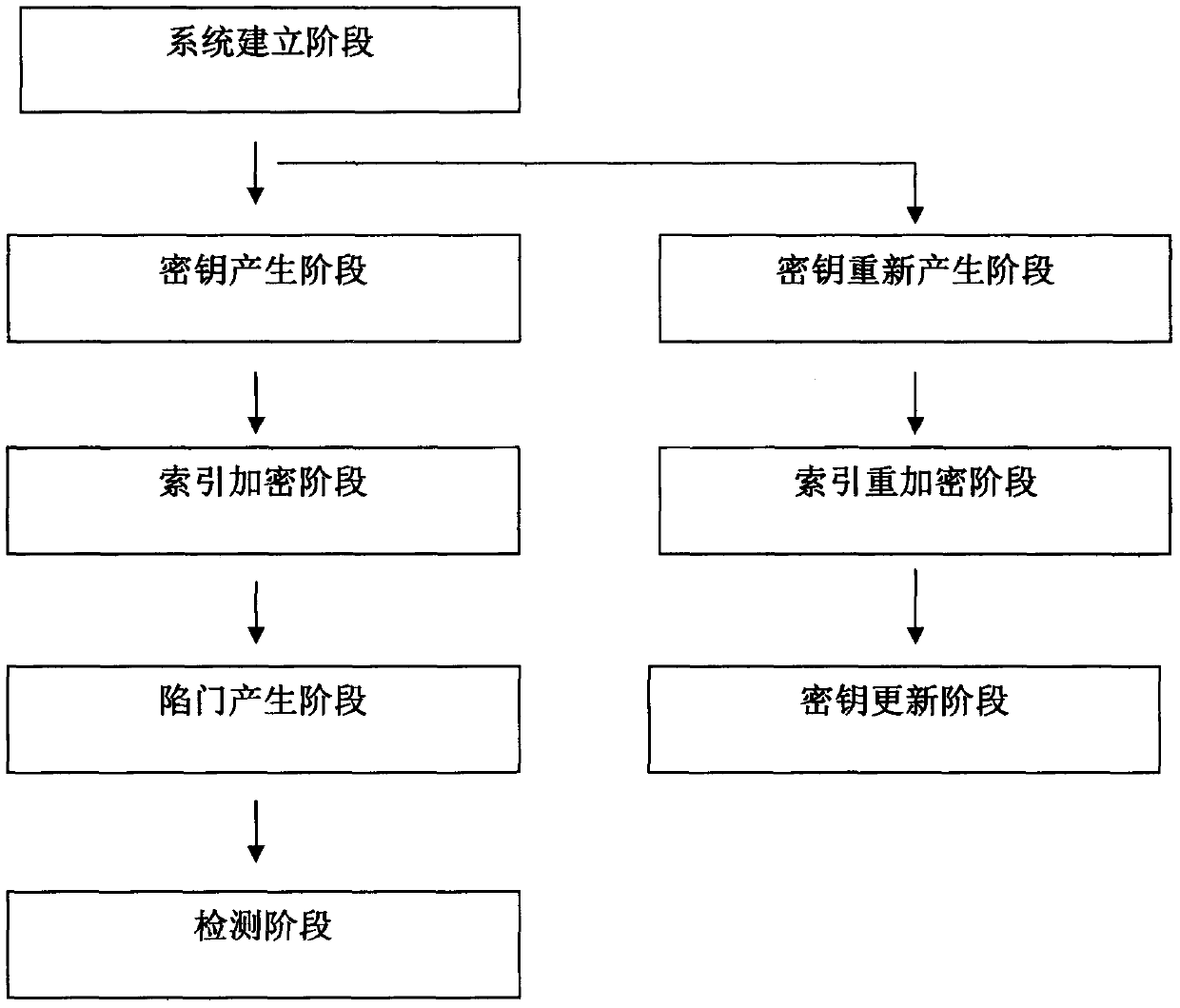
[0032] The following is attached figure 1 , the present invention will be further described.
[0033] The system of the present invention comprises following 8 stages:
[0034] (1) System establishment stage: the central institution inputs safety parameters 1 l and the total attribute set The number of attributes in n, run the bilinear group generation algorithm BG(1 l ) → (e, p, G, G τ ) to get a bilinear group. Suppose g and h are generators of group G, H: {0, 1} * → Z p is a collision-resistant hash function. The central agency randomly selects random parameters and and calculate and where k=1, 2, . . . , 2n. The central authority sets the initial version number ver=1.
[0035] The public parameters of the system are The master key is
[0036] (2) Key generation phase: when the owned attribute set is S U When a user U joins the system, the central organization randomly selects random parameters and calculate a U =g α and
[0037]
[0038] in,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com