Linux access authority control method based on index node
A technology of access rights and index nodes, applied in the computer field, can solve cumbersome problems and achieve the effect of convenient deployment and implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described below in conjunction with accompanying drawing and specific embodiment:
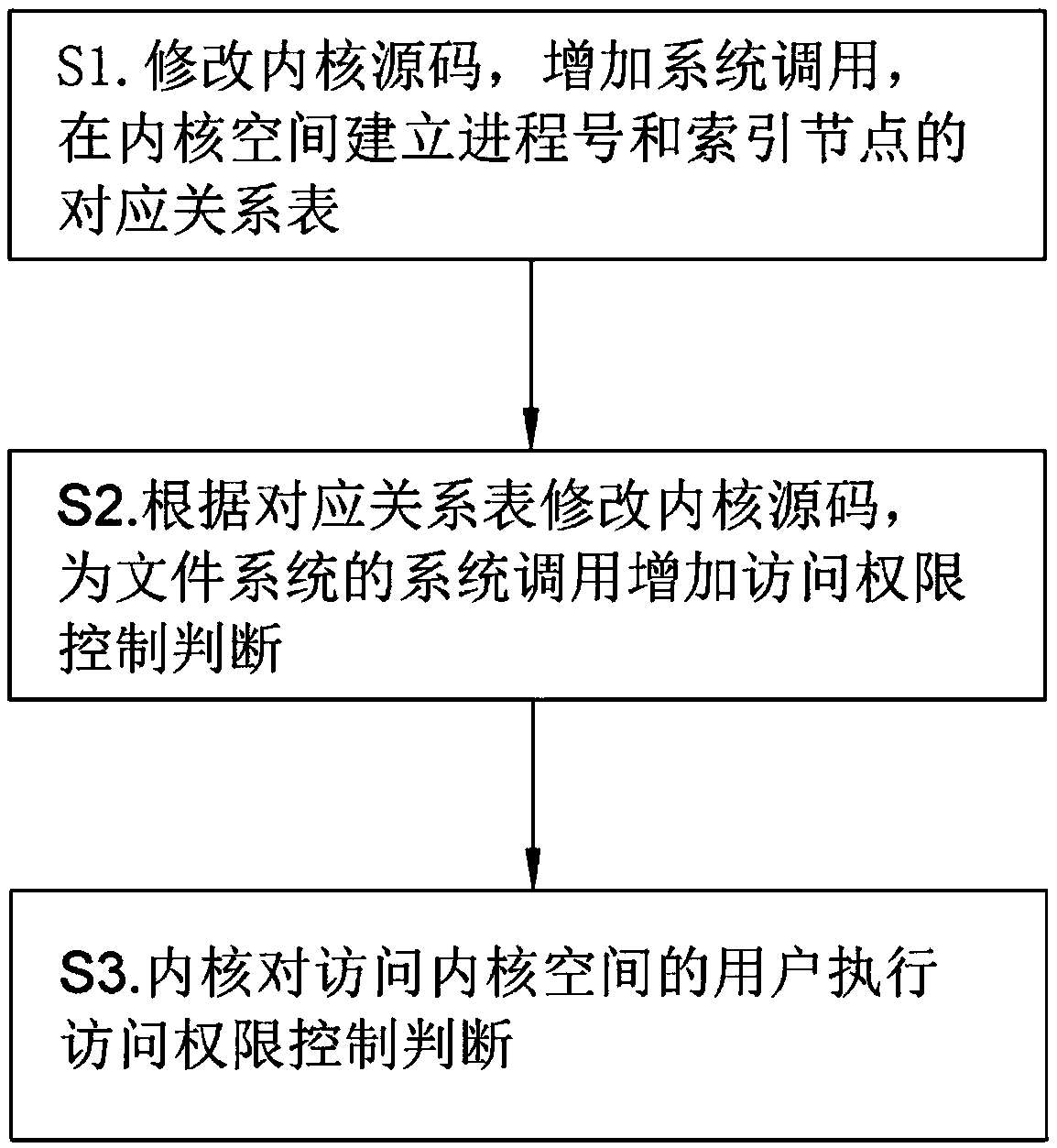
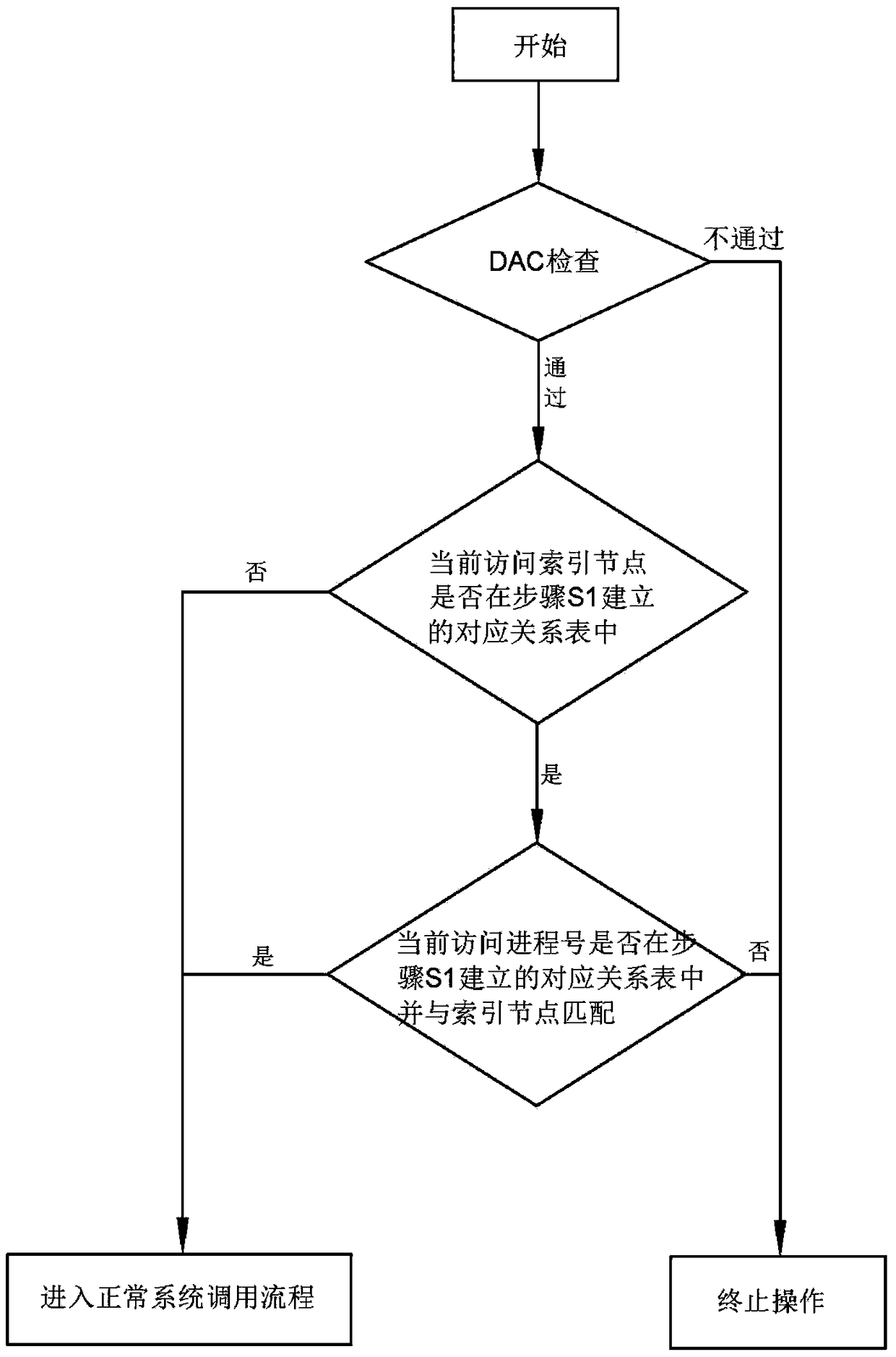
[0023] Such as Figure 1~2 As shown, the index node-based Linux access authority control method of the present invention comprises the following steps:
[0024] S1. Modify the kernel source code, add a system call, and after the system call interface is initialized, establish a corresponding relationship table between the index node and the process number in the kernel space; the loading process of the corresponding relationship table is realized by system calling or loading a read-only device .
[0025] S2. Modify the kernel source code, and add access control judgment for the system call of the file system according to the corresponding relationship table described in step S1; wherein the system call of the file system can be modified according to the actual usage scenario, including but not limited to open, and can also be read, write, etc.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com