Method for setting approval node an approval process based on countersignature
A technology of approval nodes and processes, which is applied in the field of setting approval nodes in the approval process, can solve the problems of difficulty in remembering the difference between roles and permissions with similar permissions, error-prone, complex and time-consuming, etc., to ensure authenticity and credibility degree, avoiding mutual influence, and avoiding the effect of information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0075] [Embodiment 2] The method of setting the approval node based on the countersignature in the approval process also includes a step of setting the approval role to view the content of the form fields involved in the approval process, and different approval roles of the same countersignature node can view the content of the form fields The permissions can be different. It is more convenient to use, has a wide range of applications, and facilitates the hiding of some sensitive fields to avoid information leakage.
[0076] For example: For a contract approval process, the sales-related approval role in the countersignature node can be set to be able to view all fields; the production-related approval role can be set to only view the product model field, product quantity field, technical indicator field, and Delivery time field; financial-related approvers can be set to only view the product model, product unit price, contract amount, billing information, and payment method fiel...
Embodiment 3
[0077] [Embodiment 3] Based on the setting method of the countersigned approval node in the approval process, an approval process includes a start node, at least one approval node, and an end node, including the following sequential steps: Step 1: Set the approval method of the approval node For countersignature, the approval node is called a countersignature node. The countersignature node summarizes all countersignature comments of the node's approval role, and provides a reference for the approval role of the subsequent approval node; Step 2: Set one or more approval roles for the countersignature node; It also includes a step of setting the countersignature node to anonymous countersignature. After setting it to anonymous countersignature, except the approval role can see its own countersignature comments, other non-approval roles cannot see the countersignature comments submitted by the approval role.
[0078] An anonymous countersignature function is provided. After setting ...
Embodiment 5
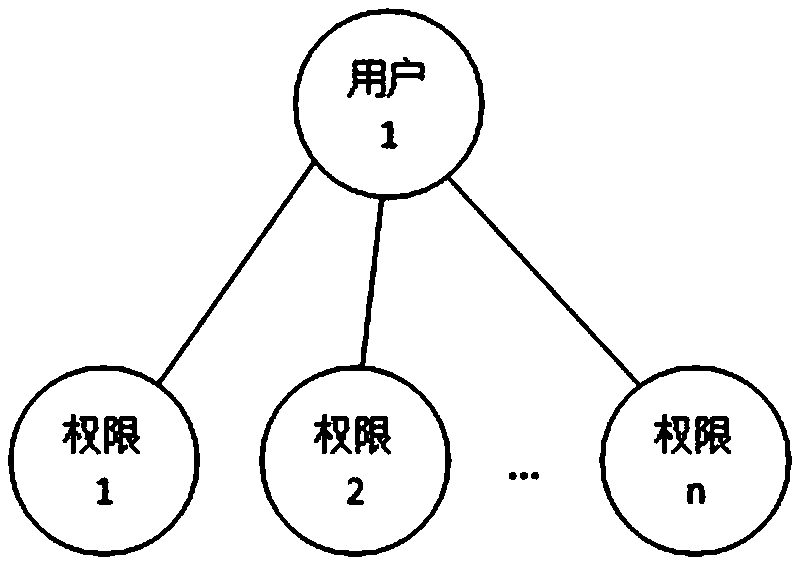
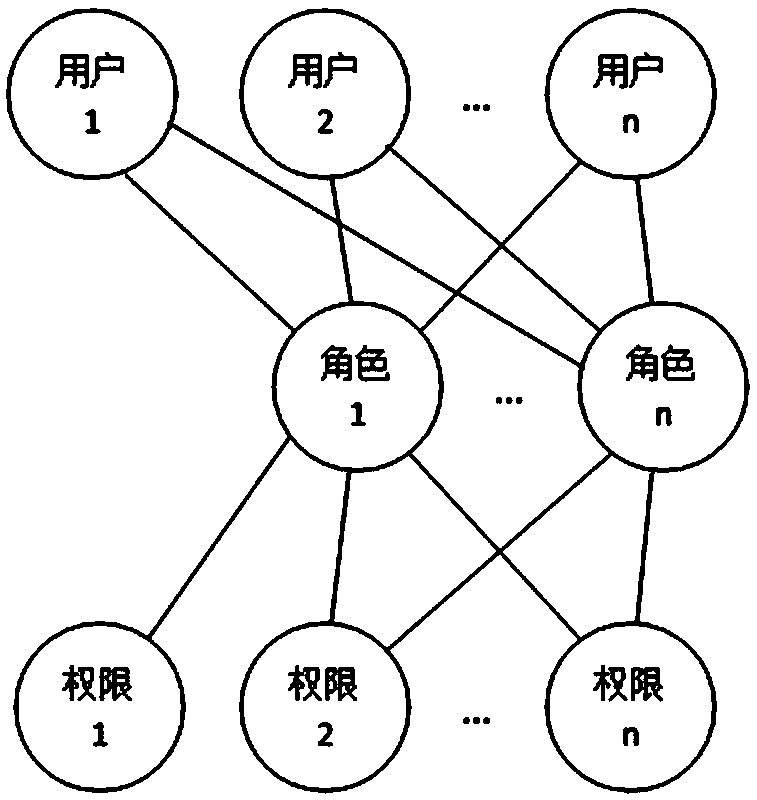
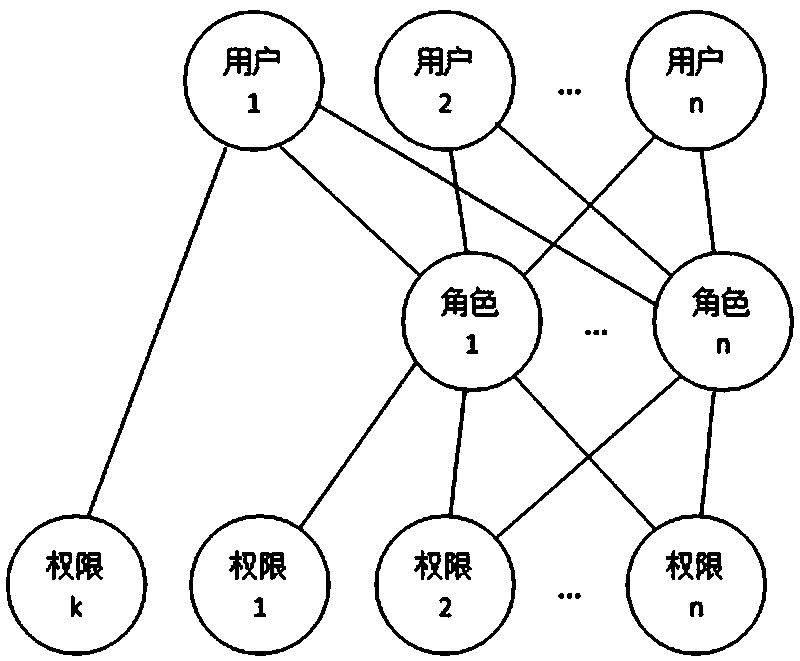
[0096] [Example 5] Such as Figure 5 As shown, the generation of the approval process includes the following steps: S1: Build a user-role-authority three-tier structure model, where: role layer: the main body of the process approval in the workflow is a role, and each role is an independent individual , Instead of a group / class, a role can only be associated with a unique user at the same time period, and a user can be associated with one or more roles; the composition of the role is: post name + post number; authority level: being executed by the workflow The required authority constitutes, and the authority is directly authorized to the role; user layer: the user determines the approval task in the approval process through the associated role, and performs the approval operation with the authority of the associated role; S2: Figure 7 As shown, the approval process is generated based on the three-tier structure model. An approval process includes a start node, at least one appr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com