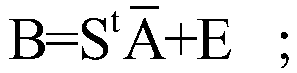Encryption and decryption device and encryption and decryption method based on universal hash functions
A general-purpose hashing, encryption and decryption technology, applied in the field of encryption and decryption devices, can solve problems such as high computational complexity requirements and large storage requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
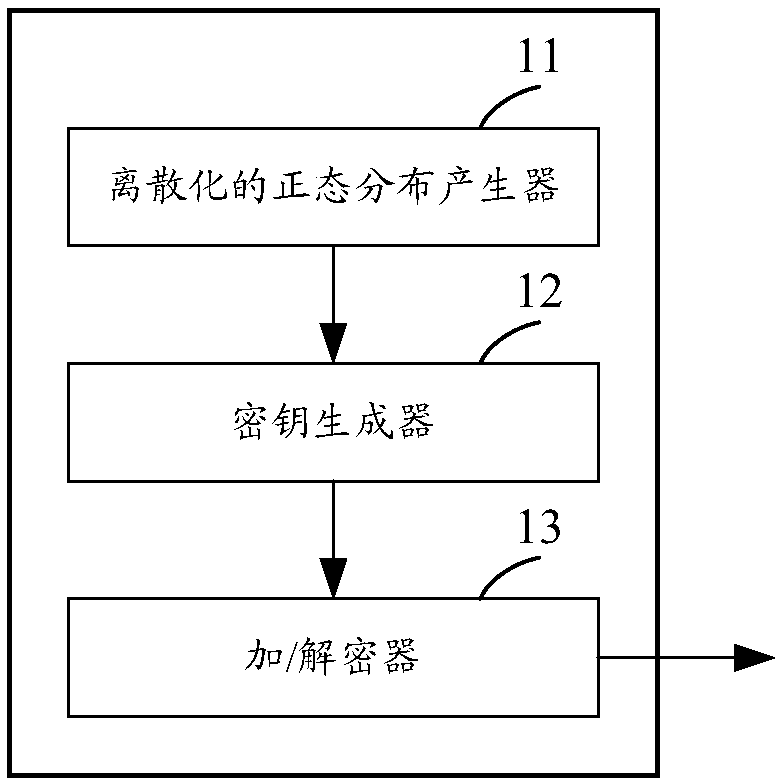
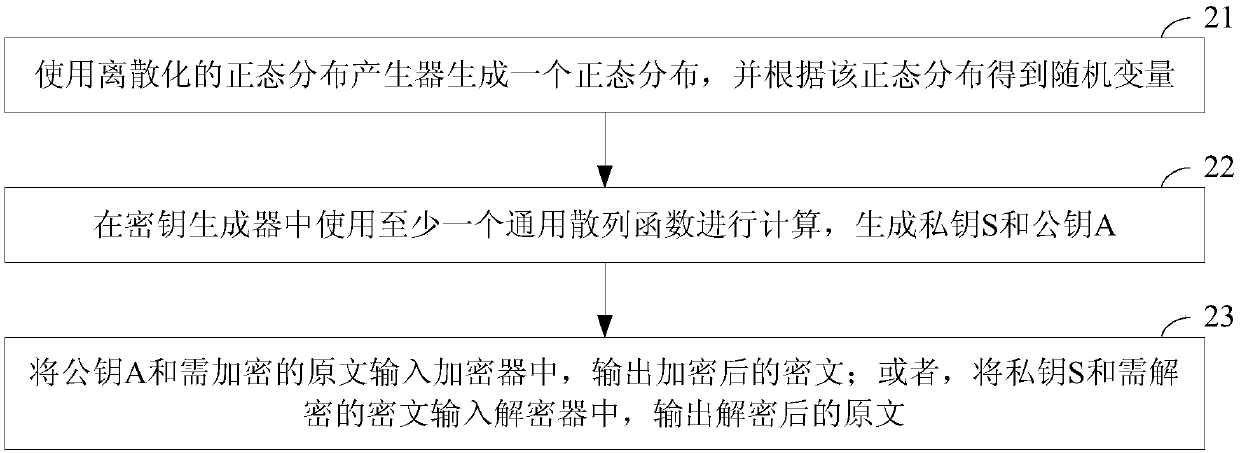
[0152] Specific embodiment one, use a universal hash function as Matrix to generate private key S and public key A.
[0153] For example, preferably, in a specific embodiment of the present invention, the step 22 may include the following steps:
[0154] Step 221a, from the integer ring Z in a uniform distribution q Take an n×l matrix above to get the S matrix.
[0155] Among them, n is a security parameter, and l is the length of the bit vector to be encrypted.
[0156] Step 221b, generate a general hash function, use the general hash function as matrix.
[0157] Preferably, in a specific embodiment of the present invention, the universal hash function may be a Toeplitz hash matrix.
[0158] Step 221c, according to normal distribution from integer ring Z q Take an l×m matrix to get the E matrix.
[0159] Among them, m is the length of the ciphertext. For example, m=(12+6c)n logn.
[0160] Step 221d, according to S matrix, matrix and E matrix, calculate the inte...
specific Embodiment 2
[0168] Embodiment 2: A general hash function is used as the S matrix to generate the private key S and the public key A.
[0169] For example, preferably, in a specific embodiment of the present invention, the step 22 may include the following steps:
[0170] Step 222a, generate a general hash function, and use the general hash function as an S matrix.
[0171] Step 222b, from the integer ring Z in a uniform distribution q Taking an n×m matrix above, we get matrix.
[0172] Among them, n is a security parameter, and m is the length of the ciphertext. For example, m=(12+6c)n logn.
[0173] Step 222c, according to normal distribution from integer ring Z q Take an l×m matrix to get the E matrix.
[0174] Among them, l is the length of the bit vector to be encrypted.
[0175] Step 222d, according to S matrix, matrix and E matrix, calculate the intermediate matrix B.
[0176] For example, preferably, in a specific embodiment of the present invention, the intermediate m...
specific Embodiment 3
[0182] Specific embodiment 3: A general hash function is used as the E matrix to generate the private key S and the public key A.
[0183] For example, preferably, in a specific embodiment of the present invention, the step 22 may include the following steps:
[0184] Step 223a, from the integer ring Z in a uniform distribution q Take an n×l matrix above to get the S matrix.
[0185] Among them, n is a security parameter, and l is the length of the bit vector to be encrypted.
[0186] Step 223b, from the integer ring Z in a uniform distribution q Taking an n×m matrix above, we get matrix.
[0187] Among them, m is the length of the ciphertext. For example, m=(12+6c)n logn.
[0188] Step 223c, generate a general hash function, and use the general hash function as an E matrix.
[0189] Step 223d, according to S matrix, matrix and E matrix, calculate the intermediate matrix B.
[0190] For example, preferably, in a specific embodiment of the present invention, the inte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com