Handheld terminal of realizing computer information security protection, vulnerability scanning and protection reinforcement and protection method
A hand-held terminal and vulnerability scanning technology, applied in computer security devices, computing, platform integrity maintenance, etc., can solve problems such as high professional skills requirements for operation and maintenance personnel, untimely protection schemes, and inability to fully grasp and understand , to achieve the effect of saving manpower, improving the level of safety protection and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below in conjunction with specific drawings and embodiments.
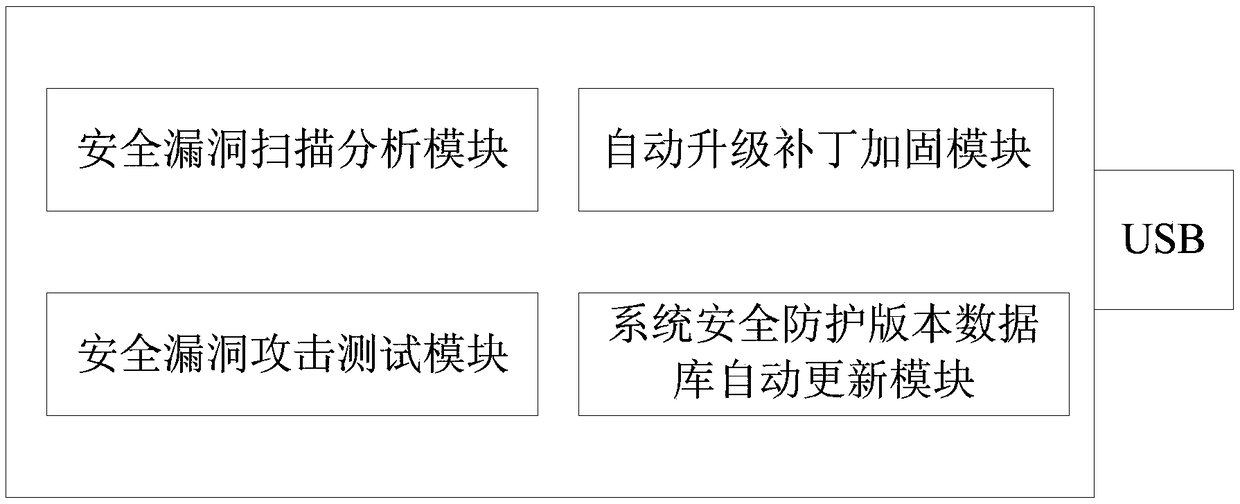
[0025] Such as figure 1 As shown, a handheld terminal that realizes computer information security protection loophole scanning and protection reinforcement provided by the present invention includes a USB interface, a display screen, a security loophole scanning analysis module, an automatic upgrade patch reinforcement module, a security loophole attack testing module, and a system Security protection version database automatic update module;
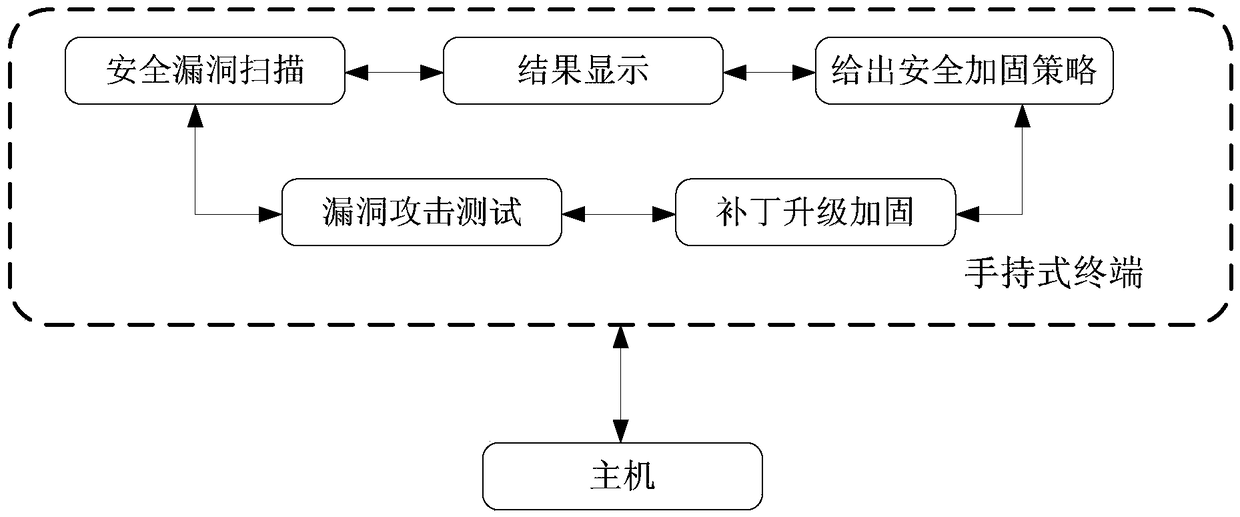
[0026] The handheld terminal is inserted into the device host to be detected through the USB interface to realize security vulnerability scanning and protection reinforcement of the device host;
[0027] 1) Security vulnerability scanning and analysis module;
[0028] The security vulnerability scanning and analysis module scans and analyzes the security vulnerabilities of the target host or network to find potential s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com