Method and device for predicting network attack
A network attack and prediction method technology, applied in the field of network security, can solve the problems of inability to predict attacks and not distinguish between attack behavior and attack results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
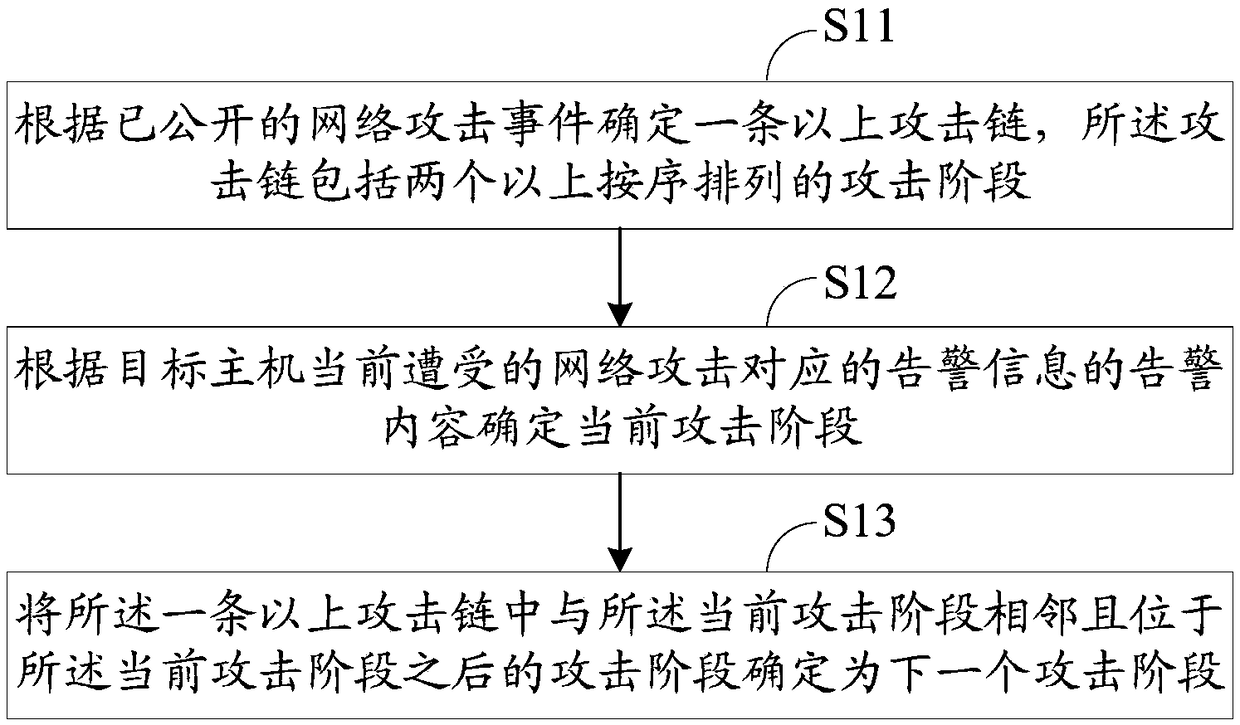
[0149] This embodiment provides a network attack prediction method, figure 1 It is a schematic flow diagram of the network attack prediction method, and the network attack prediction method includes:
[0150] Step S11: Determine more than one attack chain according to the published network attack events, and the attack chain includes more than two attack stages arranged in sequence;
[0151] Step S12: Determine the current attack stage according to the alarm content of the alarm information corresponding to the network attack currently suffered by the target host;
[0152] Step S13: Determine the attack stage that is adjacent to the current attack stage and located after the current attack stage in the one or more attack chains as the next attack stage.
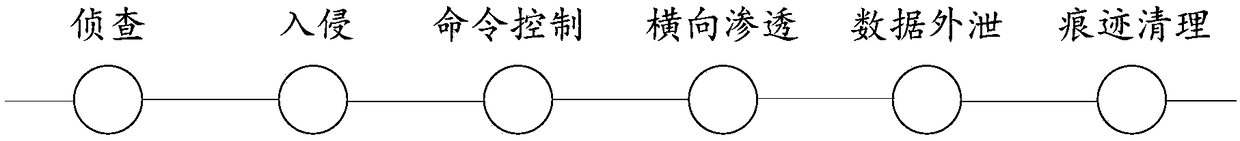
[0153] Specifically, the attack chain refers to a series of cyclic processing processes from detection to destruction of the attacked host by the attacker, usually composed of several different attack stages, and each attack stage ach...
Embodiment 2
[0164] This embodiment provides another network attack prediction method. Compared with the network attack prediction method provided in Embodiment 1, this embodiment determines the current attack stage according to the alarm content of the alarm information corresponding to the network attack currently suffered by the target host. Before, the alarm information was also obtained. Figure 4 It is a schematic diagram of the process of obtaining the alarm information in this embodiment, and the obtaining the alarm information includes:
[0165] Step S41: Detect whether the target host is under the network attack and determine the attack type of the network attack;
[0166] Step S42, if the target host is attacked by the network, detect whether the network attack is successful and determine the attack action of the successful network attack;
[0167] Step S43: If the network attack is successful, the first alarm sub-information is generated, otherwise, the second alarm sub-information is...
Embodiment 3
[0211] This embodiment provides a network attack prediction system. The network attack prediction system includes: a first determination module configured to determine more than one attack chain according to a published network attack event, and the attack chain includes two or more in sequence The second determining module is used to determine the current attack stage according to the alarm content of the alarm information corresponding to the network attack currently suffered by the target host; the third determining module is used to compare the one or more attack chains with the current The attack stage adjacent to and located after the current attack stage is determined to be the next attack stage.
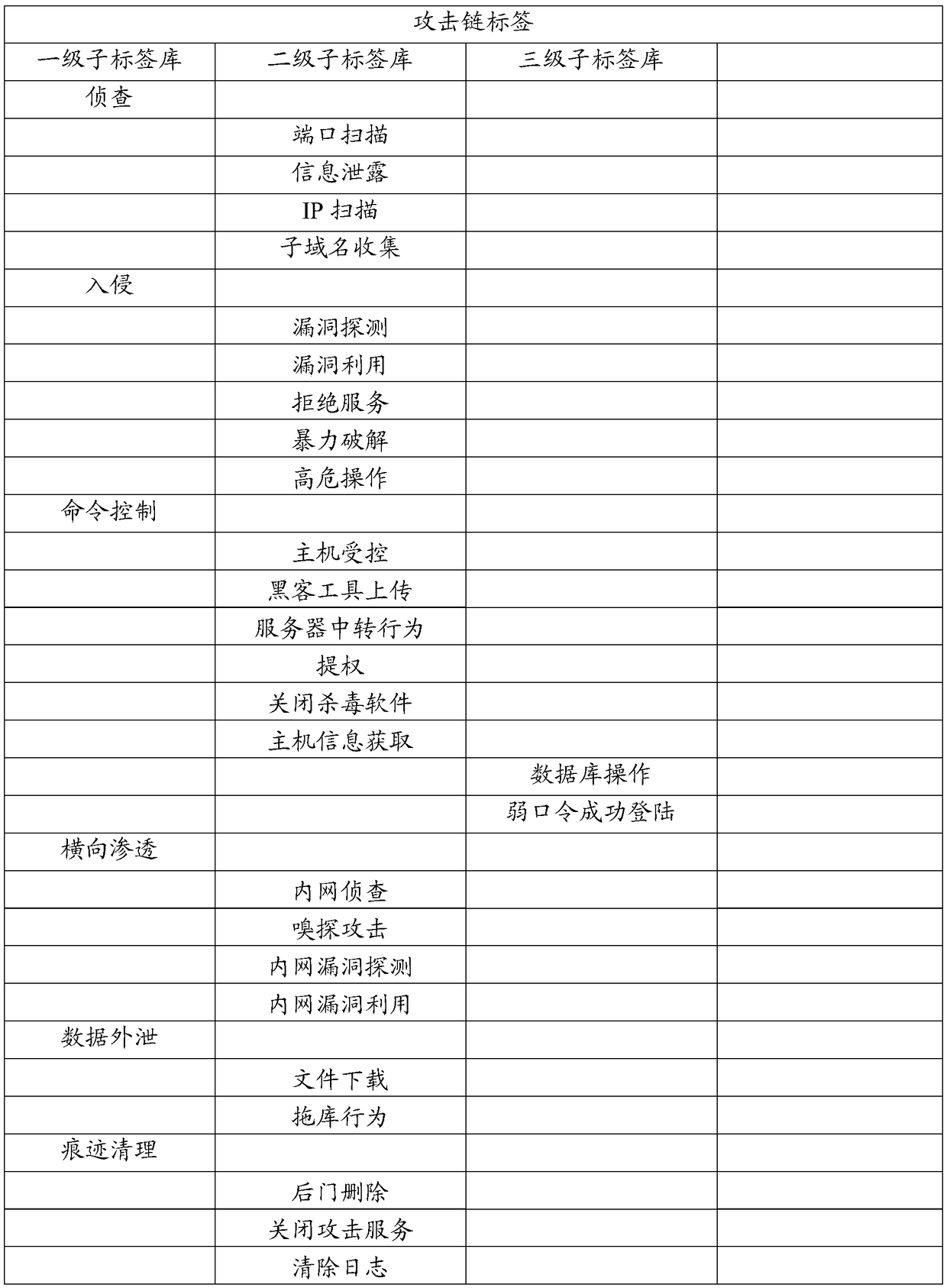
[0212] Further, the second determining module includes: a first determining unit, configured to determine an attack chain tag corresponding to the alarm information from a pre-established tag library according to the alarm content of the alarm information, wherein the tag Each a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com