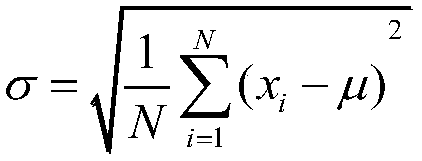Hypergraph and random forest (HG-RF)-based intrusion detection method
A random forest, intrusion detection technology, applied in special data processing applications, instruments, electrical digital data processing and other directions, can solve the problems of low training accuracy and reduced voting accuracy, to improve classification accuracy, improve classification accuracy, reduce The effect of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The specific implementation of the present invention will be further described below in conjunction with the drawings and examples, but it is not a limitation of the present invention.
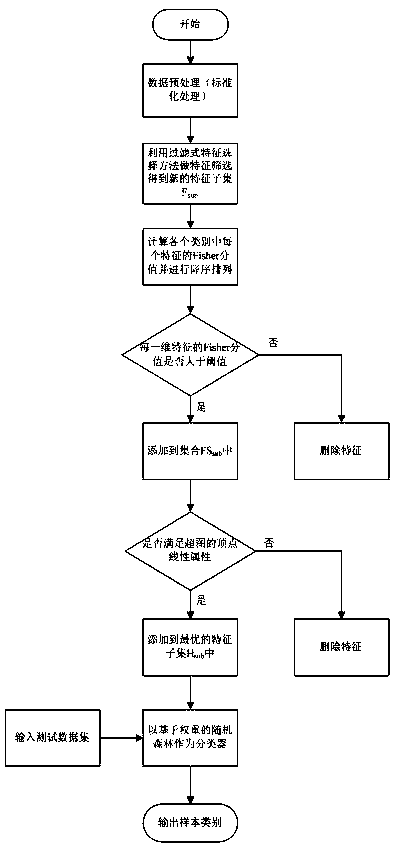
[0039] figure 1 Shows an intrusion detection method based on hypergraph and random forest, including the following steps:
[0040] (1) Data preprocessing, the specific process is as follows: For the downloaded 10% KDD data set and corrected data set, use 10% of the KDD data set as the training set, and the corrected data set as the test set, and convert all character variables into For digital variables, use the standard deviation formula to standardize the data. The standard deviation formula is as follows:
[0041]
[0042] Where x i Represents the value of the i-th sample in each dimension attribute, μ represents the average value of each dimension feature attribute, and N represents the total number of training set samples;
[0043] (2) Feature screening to obtain a new feature subset F su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com