Unmanned secure communication authentication protocol
A technology for safe communication and unmanned driving, applied in the field of unmanned vehicle safety communication authentication protocol, can solve problems such as the difficulty of trusted entities, and achieve the effect of reducing communication overhead, protecting privacy and ensuring privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
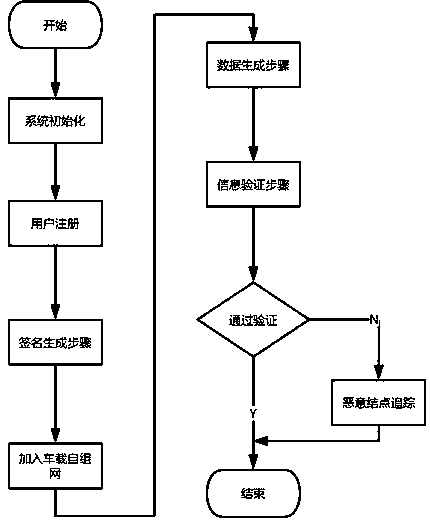
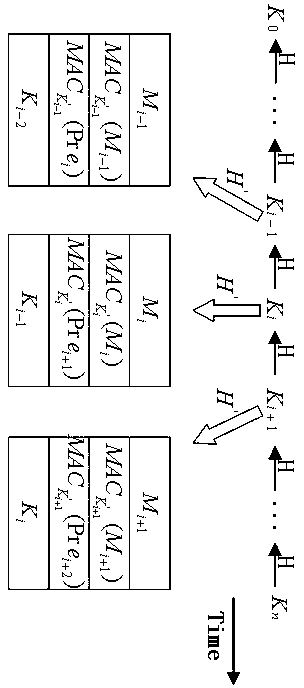
[0044] The present invention will be further described in detail below in conjunction with the above-mentioned accompanying drawings. It should be understood that after reading the teachings of the present invention, those skilled in the art can make various changes or modifications to the present invention, and these equivalent forms also fall within the scope defined by the appended claims of the present application.
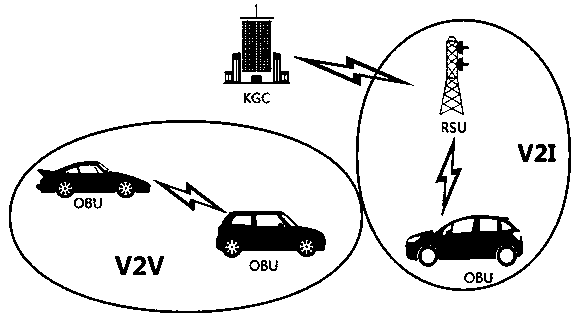
[0045] Such as figure 1 As shown, VANET mainly includes three components: On-Board Unit (OBU), Roadside Unit (RSU) and Trusted Authentication Authority (TA). However, the security authentication protocol described in the present invention mainly refers to vehicle-to-vehicle communication (V2V), ie does not involve the RSU component. The security authentication scheme described in the present invention mainly involves two parts, TA and OBU. TA is responsible for the distribution and management of keys, and the tracking of malicious vehicles. OBU is responsibl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com